
 |
| |||||||
Plagegeister aller Art und deren Bekämpfung: TR/Crypt.XPACK.Gen in directx.exeWindows 7 Wenn Du nicht sicher bist, ob Du dir Malware oder Trojaner eingefangen hast, erstelle hier ein Thema. Ein Experte wird sich mit weiteren Anweisungen melden und Dir helfen die Malware zu entfernen oder Unerwünschte Software zu deinstallieren bzw. zu löschen. Bitte schildere dein Problem so genau wie möglich. Sollte es ein Trojaner oder Viren Problem sein wird ein Experte Dir bei der Beseitigug der Infektion helfen. |
 |
| | #1 |
| | TR/Crypt.XPACK.Gen in directx.exe hi zusammen! ich habe ein problem mit einem trojaner. AntiVir findet den trojaner TR/Crypt.XPACK.Gen in den dateien E:\WINDOWS\system32\directx.exe und E:\WINDOWS\Driver Cache\IEXPLORER.EXE danke fuer eure hilfe! möli hier mein HJT-Log: Logfile of Trend Micro HijackThis v2.0.2 Scan saved at 19:45:00, on 12.04.2008 Platform: Windows XP SP2 (WinNT 5.01.2600) MSIE: Internet Explorer v7.00 (7.00.5730.0011) Boot mode: Normal Running processes: E:\WINDOWS\System32\smss.exe E:\WINDOWS\system32\winlogon.exe E:\WINDOWS\system32\services.exe E:\WINDOWS\system32\lsass.exe E:\WINDOWS\system32\Ati2evxx.exe E:\WINDOWS\system32\svchost.exe E:\WINDOWS\System32\svchost.exe E:\WINDOWS\system32\Ati2evxx.exe E:\WINDOWS\system32\spoolsv.exe E:\Programme\Pinnacle\Shared Files\Programs\StrmServer\StrmServer.exe E:\WINDOWS\Explorer.EXE E:\Programme\AntiVir PersonalEdition Classic\sched.exe E:\Programme\AntiVir PersonalEdition Classic\avguard.exe E:\Programme\Digidesign\Drivers\MMERefresh.exe E:\Programme\Pinnacle\MediaServer\Microsoft SQL Server\MSSQL$PINNACLESYS\Binn\sqlservr.exe E:\Programme\MusicIP\MusicIP Mixer\MusicMagicServer.exe E:\WINDOWS\System32\svchost.exe E:\WINDOWS\System32\svchost.exe E:\Programme\Simese\Simese.exe E:\PROGRA~1\SQUEEZ~1\server\Bin\MSWIN3~1\mysqld.exe E:\WINDOWS\System32\svchost.exe e:\programme\pinnacle\shared files\programs\mediaserver\pmshost.exe E:\Programme\DU Meter\DUMeter.exe E:\WINDOWS\system32\devldr32.exe E:\Programme\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe E:\Programme\ATI Technologies\ATI.ACE\CLI.EXE E:\WINDOWS\system32\ctfmon.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosBtMng.exe E:\Programme\SqueezeCenter\SqueezeTray.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosA2dp.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosBtHsp.exe E:\PROGRA~1\SQUEEZ~1\server\SQUEEZ~1.EXE E:\Programme\Toshiba\Bluetooth Toshiba Stack\tosOBEX.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\tosBtProc.exe E:\Programme\MusicIP\MusicIP Mixer\mDNSResponder.exe E:\Programme\ATI Technologies\ATI.ACE\cli.exe E:\Programme\AntiVir PersonalEdition Classic\avgnt.exe E:\Programme\Internet Explorer\iexplore.exe E:\Programme\AntiVir PersonalEdition Classic\avscan.exe E:\Programme\Internet Explorer\iexplore.exe E:\Dokumente und Einstellungen\Steff\Desktop\HiJackThis.exe R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.google.ch/ R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157 R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896 R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896 R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157 R1 - HKCU\Software\Microsoft\Internet Connection Wizard,ShellNext = http://www.google.ch/ O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - E:\Programme\Gemeinsame Dateien\Adobe\Acrobat\ActiveX\AcroIEHelper.dll O3 - Toolbar: (no name) - {42CDD1BF-3FFB-4238-8AD1-7859DF00B1D6} - (no file) O3 - Toolbar: (no name) - {BA52B914-B692-46c4-B683-905236F6F655} - (no file) O4 - HKLM\..\Run: [DU Meter] E:\Programme\DU Meter\DUMeter.exe O4 - HKLM\..\Run: [avgnt] "E:\Programme\AntiVir PersonalEdition Classic\avgnt.exe" /min O4 - HKLM\..\Run: [PinnacleDriverCheck] # E:\WINDOWS\system32\PSDrvCheck.exe -CheckReg O4 - HKLM\..\Run: [PMCRemote] # E:\Programme\Pinnacle\Shared Files\Programs\Remote\Remoterm.exe O4 - HKLM\..\Run: [PMCS] # "E:\Programme\Pinnacle\Shared Files\Programs\MediaCenterService\PMC.Service.Main.exe" -host -clearDebug O4 - HKLM\..\Run: [NeroFilterCheck] E:\WINDOWS\system32\NeroCheck.exe O4 - HKLM\..\Run: [VirtualCloneDrive] "E:\Programme\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe" /s O4 - HKLM\..\Run: [ATICCC] "E:\Programme\ATI Technologies\ATI.ACE\CLIStart.exe" O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "E:\Programme\Adobe\Reader 8.0\Reader\Reader_sl.exe" O4 - HKCU\..\Run: [WebCamRT.exe] : O4 - HKCU\..\Run: [ctfmon.exe] E:\WINDOWS\system32\ctfmon.exe O4 - HKCU\..\Run: [BitTorrent] "E:\Programme\BitTorrent\bittorrent.exe" --force_start_minimized O4 - HKUS\S-1-5-19\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'LOKALER DIENST') O4 - HKUS\S-1-5-20\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'NETZWERKDIENST') O4 - HKUS\S-1-5-18\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'SYSTEM') O4 - HKUS\.DEFAULT\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'Default user') O4 - Global Startup: AutorunsDisabled O4 - Global Startup: Bluetooth Manager.lnk = ? O4 - Global Startup: Pinnacle ShowCenter StreamServer.lnk = ? O4 - Global Startup: SqueezeCenter-Taskleisten-Tool.lnk = E:\Programme\SqueezeCenter\SqueezeTray.exe O8 - Extra context menu item: E&xport to Microsoft Excel - res://E:\PROGRA~1\MICROS~2\OFFICE11\EXCEL.EXE/3000 O9 - Extra button: (no name) - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - E:\WINDOWS\system32\msjava.dll O9 - Extra 'Tools' menuitem: Sun Java Konsole - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - E:\WINDOWS\system32\msjava.dll O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - E:\PROGRA~1\MICROS~2\OFFICE11\REFIEBAR.DLL O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - E:\Programme\Messenger\msmsgs.exe O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - E:\Programme\Messenger\msmsgs.exe O12 - Plugin for .fpx: C:\\Program Files\\Internet Explorer\\PLUGINS\\NPRVRT32.dll O12 - Plugin for .ivr: C:\\Program Files\\Internet Explorer\\PLUGINS\\NPRVRT32.dll O15 - Trusted Zone: http://linktrader.cyberspacehq.com O16 - DPF: {156BF4B7-AE3A-4365-BD88-95A75AF8F09D} (HPSDDX Class) - http://www.hp.com/cpso-support-new/SDD/hpsddObjSigned.cab O16 - DPF: {2CA0FF2C-0CE1-4382-A0C4-B2782965CCC2} (G-Vista ActiveX) - http://www.dilas.ch/plugin/gvista30/gvista30.cab O16 - DPF: {4ED9DDF0-7479-4BBE-9335-5A1EDB1D8A21} - http://download.mcafee.com/molbin/shared/mcinsctl/en-us/4,0,0,81/mcinsctl.cab O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1124829689790 O16 - DPF: {AE4CEC9D-C836-4579-829B-4C345101B3B9} (GVista Terrain Renderer) - http://www.dilas.ch/plugin/gvista/gvista2709.cab O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) - http://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab O23 - Service: AntiVir Scheduler (AntiVirScheduler) - Avira GmbH - E:\Programme\AntiVir PersonalEdition Classic\sched.exe O23 - Service: AntiVir PersonalEdition Classic Service (AntiVirService) - Avira GmbH - E:\Programme\AntiVir PersonalEdition Classic\avguard.exe O23 - Service: Ati HotKey Poller - ATI Technologies Inc. - E:\WINDOWS\system32\Ati2evxx.exe O23 - Service: ATI Smart - Unknown owner - E:\WINDOWS\system32\ati2sgag.exe O23 - Service: Bonjour Service - Apple Computer, Inc. - E:\Programme\MusicIP\MusicIP Mixer\mDNSResponder.exe O23 - Service: Digidesign MME Refresh Service (DigiRefresh) - Digidesign, A Division of Avid Technology, Inc. - E:\Programme\Digidesign\Drivers\MMERefresh.exe O23 - Service: digiSPTIService - Digidesign, A Division of Avid Technology, Inc. - E:\Programme\Digidesign\Pro Tools\digiSPTIService.exe O23 - Service: Firebird Server - MAGIX Instance (FirebirdServerMAGIXInstance) - MAGIX® - E:\Programme\Common\Database\bin\fbserver.exe O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - E:\Programme\Gemeinsame Dateien\InstallShield\Driver\1150\Intel 32\IDriverT.exe O23 - Service: MusicIP Server - Unknown owner - E:\Programme\MusicIP\MusicIP Mixer\MusicMagicServer.exe O23 - Service: Pinnacle Systems Media Service (PinnacleSys.MediaServer) - Pinnacle Systems - e:\programme\pinnacle\shared files\programs\mediaserver\pmshost.exe O23 - Service: SimeseServer - Mattic - E:\Programme\Simese\Simese.exe O23 - Service: SqueezeMySQL - Unknown owner - E:\PROGRA~1\SQUEEZ~1\server\Bin\MSWIN3~1\mysqld.exe |
| | #2 | |
     | TR/Crypt.XPACK.Gen in directx.exe Hi,
__________________lasse die beiden Files mal Online prüfen: virustotal Oben auf der Seite --> auf Durchsuchen klicken --> Datei aussuchen (oder gleich die Datei mit korrektem Pfad einkopieren) --> Doppelklick auf die zu prüfende Datei --> klick auf "Send"... jetzt abwarten - dann mit der rechten Maustaste den Text markieren -> kopieren - einfügen VirusTotal - Free Online Virus and Malware Scan Zitat:
Download ComboFix (http://download.bleepingcomputer.com/sUBs/ComboFix.exe) und speichert es auf den Desktop! Alle Fenster schliessen und combofix.exe starten Folge den Instruktionen in dem Fenster Waehrend Combofix lauft NICHT ins Fenster klicken sonst friert dein Rechner ein Wenn das Tool fertig ist,oeffnet sich ein logfile(combofix.txt ) nun das KOMPLETTE Log mit rechtem Mausklick abkopieren und ins Forum mit rechtem Mausklick "einfügen" Poste es zusammen mit einem neuen Log von HijackThis chris
__________________ |
| | #3 |
| | TR/Crypt.XPACK.Gen in directx.exe hi chris
__________________vielen dank fuer deine hilfe!! ich bin sehr froh, dass ich mit diesem "scheiss-virus" nicht alleine fertig werden muss. gruss möli here we go mit den informationen (teil 1): **************************************************************************************** E:\WINDOWS\system32\directx.exe: Antivirus Version letzte aktualisierung Ergebnis AhnLab-V3 2008.4.15.0 2008.04.14 Win-Trojan/Rukap.82432.DG AntiVir 7.6.0.85 2008.04.14 TR/Crypt.XPACK.Gen Authentium 4.93.8 2008.04.13 Possibly a new variant of W32/NewUnknownMalware-OC05!Maximus Avast 4.8.1169.0 2008.04.14 - AVG 7.5.0.516 2008.04.14 - BitDefender 7.2 2008.04.14 Packer.PESpin.A CAT-QuickHeal 9.50 2008.04.14 (Suspicious) - DNAScan ClamAV 0.92.1 2008.04.14 PUA.Packed.PESpin DrWeb 4.44.0.09170 2008.04.14 Trojan.Click.origin eSafe 7.0.15.0 2008.04.09 Suspicious File eTrust-Vet 31.3.5697 2008.04.14 - Ewido 4.0 2008.04.14 - F-Prot 4.4.2.54 2008.04.14 W32/Heuristic-162!Eldorado F-Secure 6.70.13260.0 2008.04.14 Backdoor.Win32.Rukap.gen FileAdvisor 1 2008.04.14 - Fortinet 3.14.0.0 2008.04.14 - Ikarus T3.1.1.26 2008.04.14 Trojan-PWS.Win32.LdPinch.beo Kaspersky 7.0.0.125 2008.04.14 Backdoor.Win32.Rukap.gen McAfee 5273 2008.04.14 BackDoor-CZY Microsoft 1.3408 2008.04.14 Backdoor:Win32/Rukap.gen!A NOD32v2 3026 2008.04.14 a variant of Win32/Rukap.BS Norman 5.80.02 2008.04.14 - Panda 9.0.0.4 2008.04.14 Suspicious file Prevx1 V2 2008.04.14 Heuristic: Suspicious Self Modifying EXE Rising 20.40.02.00 2008.04.14 Backdoor.Dservice.a Sophos 4.28.0 2008.04.14 Mal/Behav-199 Sunbelt 3.0.1041.0 2008.04.12 - Symantec 10 2008.04.14 Backdoor.Sdbot TheHacker 6.2.92.277 2008.04.14 W32/Behav-Heuristic-070 VBA32 3.12.6.4 2008.04.14 suspected of Trojan-Clicker.Agent.36 VirusBuster 4.3.26:9 2008.04.14 Packed/PeSpin Webwasher-Gateway 6.6.2 2008.04.14 Trojan.Crypt.XPACK.Gen weitere Informationen File size: 82432 bytes MD5...: 9678ada3b72fcde69a370a3104278f72 SHA1..: 1b353f72a7f268b0c4c583b3ada405fe2263aff5 SHA256: 28190ea6ca868d817da4313e7c1c2405192728773a7195c4fb176910445d7372 SHA512: 7bd16989039054a3cb09cfa31afe5c68d51fe00df45ef9dd5f2c7a391d3fa19e 4ee63a51407176b2a8009e8fee1b302dd72f976e7a803c02d5fd5fae00bdfd09 PEiD..: PESpin v1.304 -> Cyberbob PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x4260d4 timedatestamp.....: 0x0 (Thu Jan 01 00:00:00 1970) machinetype.......: 0x14c (I386) ( 4 sections ) name viradd virsiz rawdsiz ntrpy md5 .petite 0x1000 0x16000 0xbe00 8.00 d96081d890d2ab668cd5b46c2d564e36 .petite 0x17000 0x5000 0x1800 7.97 82ebac3e9fdcd13673184a99ba34a5e2 .petite 0x1c000 0xa000 0x1e00 7.98 1d946a1fb81077c0a01058eb628fe082 .petite 0x26000 0x48ba 0x4a00 7.85 9f50b7c47a790c1666edb1d2c1e294f2 ( 3 imports ) > USER32.DLL: MessageBoxA > COMCTL32.DLL: InitCommonControls > KERNEL32.dll: LoadLibraryA, GetProcAddress ( 0 exports ) packers: Troj-Crypt.E packers: PESpin Prevx info: http://info.prevx.com/aboutprogramtext.asp?PX5=CCA9994200A1412B42D7013B4B9C410001ED26B1 **************************************************************************************** E:\WINDOWS\Driver Cache\IEXPLORER.EXE: virustotal meldet, dass dies dasselbe file is wie directx.exe. filesize und die hashes stimmen auch ueberein. **************************************************************************************** die restlichen programme sind von meinen mediaservern. diese sind mir bekannt und sollten sauber sein: E:\Programme\SqueezeCenter\SqueezeTray.exe: Antivirus Version letzte aktualisierung Ergebnis AhnLab-V3 2008.4.15.0 2008.04.14 - AntiVir 7.6.0.85 2008.04.14 - Authentium 4.93.8 2008.04.13 - Avast 4.8.1169.0 2008.04.14 - AVG 7.5.0.516 2008.04.14 - BitDefender 7.2 2008.04.14 - CAT-QuickHeal 9.50 2008.04.14 - ClamAV 0.92.1 2008.04.14 - DrWeb 4.44.0.09170 2008.04.14 - eSafe 7.0.15.0 2008.04.09 - eTrust-Vet 31.3.5697 2008.04.14 - Ewido 4.0 2008.04.14 - F-Prot 4.4.2.54 2008.04.14 - F-Secure 6.70.13260.0 2008.04.14 - FileAdvisor 1 2008.04.14 - Fortinet 3.14.0.0 2008.04.14 - Ikarus T3.1.1.26.0 2008.04.14 - Kaspersky 7.0.0.125 2008.04.14 - McAfee 5273 2008.04.14 - Microsoft 1.3408 2008.04.14 - NOD32v2 3026 2008.04.14 - Norman 5.80.02 2008.04.14 - Panda 9.0.0.4 2008.04.14 - Prevx1 V2 2008.04.14 Heuristic: Suspicious Self Modifying File Rising 20.40.02.00 2008.04.14 - Sophos 4.28.0 2008.04.14 - Sunbelt 3.0.1041.0 2008.04.12 - Symantec 10 2008.04.14 - TheHacker 6.2.92.277 2008.04.14 - VBA32 3.12.6.4 2008.04.14 - VirusBuster 4.3.26:9 2008.04.14 - Webwasher-Gateway 6.6.2 2008.04.14 - weitere Informationen File size: 1740887 bytes MD5...: e593db5f8012cd1424864b3c008f6e10 SHA1..: f3908f813a397a3df65e16032b407b96022761f5 SHA256: 0f87f070c0e9c7067319877b138a4bd3fad09234da2bee749230187b9e76e268 SHA512: 00cd5a4bd2e969a529ff6b5f356a8a97d055808eb5163c733a439c2d5207e57a 590453be676ef63d8902a5c5684b3b826f0e28df2bd994174cd92da5c01ce3c7 PEiD..: Armadillo v1.71 PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x40b51c timedatestamp.....: 0x45fe3a27 (Mon Mar 19 07:22:15 2007) machinetype.......: 0x14c (I386) ( 4 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0xd16a 0xe000 6.28 482de97c73bc1f29eb591977a1a9fbde .rdata 0xf000 0x27f4 0x3000 4.79 135cf716c1023c4e4bb29ca54d45756c .data 0x12000 0x1ab8 0x2000 2.62 1ad56e97e448a4351410e1754712df1a .rsrc 0x14000 0x194230 0x195000 7.90 7fd950f06bbd6407a24e2bda89a0ce83 ( 7 imports ) > KERNEL32.dll: LeaveCriticalSection, GetLastError, CreateThread, GetCurrentThreadId, GetVersion, MultiByteToWideChar, GetModuleHandleA, GetModuleFileNameA, GetProcAddress, LoadLibraryA, FreeLibrary, GetVersionExA, GetShortPathNameW, WideCharToMultiByte, FindClose, FindFirstFileA, GetComputerNameA, CreateFileA, CloseHandle, Sleep, EnterCriticalSection, GetTempPathA, InitializeCriticalSection, DeleteCriticalSection, UnmapViewOfFile, MapViewOfFile, CreateFileMappingA, LockResource, LoadResource, FindResourceA, LoadLibraryExA, SetLastError, VirtualProtect, VirtualFree, VirtualAlloc, ExitThread, OutputDebugStringA, FindNextFileA > USER32.dll: DestroyWindow, CallNextHookEx, PostMessageA, MessageBoxA, SendMessageA, LoadIconA, RegisterClassExA, RegisterWindowMessageA, CreateWindowExA, ShowWindow, UpdateWindow, GetMessageA, TranslateMessage, DispatchMessageA, PostQuitMessage, DefWindowProcA, GetDoubleClickTime, LoadMenuIndirectA, GetSubMenu, GetCursorPos, TrackPopupMenu, DestroyMenu, RegisterHotKey, KillTimer, SetTimer, GetSystemMetrics, LoadImageA, GetWindowTextLengthA, GetWindowTextA, UnhookWindowsHookEx, SetForegroundWindow, SetWindowsHookExA > ADVAPI32.dll: GetUserNameA > SHELL32.dll: ShellExecuteExA, Shell_NotifyIconA > ole32.dll: CoInitializeEx > MSVCRT.dll: _setjmp3, time, wcslen, memcmp, _except_handler3, __set_app_type, __p__fmode, __p__commode, _adjust_fdiv, __setusermatherr, _initterm, __getmainargs, __p___initenv, exit, _XcptFilter, _exit, _onexit, __dllonexit, _stricmp, _unlink, _rmdir, _putenv, _fileno, _dup2, _strnicmp, _chmod, _getpid, _mkdir, _strdup, _stat, wcscmp, strrchr, toupper, getenv, abort, vsprintf, calloc, _controlfp, __3@YAXPAX@Z, memcpy, __CxxFrameHandler, __p__environ, __CxxLongjmpUnwind, __2@YAPAXI@Z, sprintf, memset, strcmp, strncpy, strncmp, strlen, malloc, strcpy, fclose, fgets, fopen, strcat, free, fputs, _iob, perror, strchr, strstr, fprintf, _ftol, localtime, atol, _pctype, _isctype, __mb_cur_max, atoi, fwrite, rand, srand, _close, _futime, _open_osfhandle, _errno, fread, fflush, fputc > WININET.dll: InternetCloseHandle, InternetReadFile, InternetOpenUrlA, InternetOpenA ( 0 exports ) Prevx info: http://info.prevx.com/aboutprogramtext.asp?PX5=C29192AB5769278290311ABA0DC176004102F607 |
| | #4 |
| | TR/Crypt.XPACK.Gen in directx.exe teil 2: **************************************************************************************** E:\Programme\MusicIP\MusicIP Mixer\MusicMagicServer.exe: Antivirus Version letzte aktualisierung Ergebnis AhnLab-V3 2008.4.15.0 2008.04.14 - AntiVir 7.6.0.85 2008.04.14 - Authentium 4.93.8 2008.04.13 - Avast 4.8.1169.0 2008.04.14 - AVG 7.5.0.516 2008.04.14 - BitDefender 7.2 2008.04.14 - CAT-QuickHeal 9.50 2008.04.14 - ClamAV 0.92.1 2008.04.14 - DrWeb 4.44.0.09170 2008.04.14 - eSafe 7.0.15.0 2008.04.09 - eTrust-Vet 31.3.5697 2008.04.14 - Ewido 4.0 2008.04.14 - F-Prot 4.4.2.54 2008.04.14 - F-Secure 6.70.13260.0 2008.04.14 - FileAdvisor 1 2008.04.14 - Fortinet 3.14.0.0 2008.04.14 - Ikarus T3.1.1.26.0 2008.04.14 - Kaspersky 7.0.0.125 2008.04.14 - McAfee 5273 2008.04.14 - Microsoft 1.3408 2008.04.14 - NOD32v2 3026 2008.04.14 - Norman 5.80.02 2008.04.14 - Panda 9.0.0.4 2008.04.14 - Prevx1 V2 2008.04.14 Heuristic: Suspicious Self Modifying File Rising 20.40.02.00 2008.04.14 - Sophos 4.28.0 2008.04.14 - Sunbelt 3.0.1041.0 2008.04.12 - Symantec 10 2008.04.14 - TheHacker 6.2.92.277 2008.04.14 - VBA32 3.12.6.4 2008.04.14 - VirusBuster 4.3.26:9 2008.04.14 - Webwasher-Gateway 6.6.2 2008.04.14 - weitere Informationen File size: 2732032 bytes MD5...: 394ea7fc251921a6653cb2610b414228 SHA1..: 169ea665e6e894d5c67650734d15bf15e6f8a3e8 SHA256: d26711512b113fc8087bb477c4331140c6064e85eebc2843058ce53fa374ebc1 SHA512: c6bdfec815f6c3a9f128c9e81ff2e1ff0d5fccdec91c6e451cfa2f9ebe4bebfb 1fccf5b54dd93f47611049a26fe34487be581024c5f526a6ded21f782566ab7e PEiD..: Armadillo v1.71 PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x5bf9b4 timedatestamp.....: 0x46ae103f (Mon Jul 30 16:22:23 2007) machinetype.......: 0x14c (I386) ( 6 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x3000 0x1fe092 0x1ff000 6.64 db9ab4b6d7d7472ce0bc2b59fc008abb .rdata 0x202000 0x3d9ea 0x3e000 5.45 34550faa1a3c64b6db182a8ec11f6ef4 .data 0x240000 0x41e78 0x39000 5.50 d26d2992ad4999ebb4e44583ede38b11 .data1 0x282000 0x2920 0x3000 4.78 27b3e788856ffc94bd750373229fcb2f DATA 0x285000 0x1de20 0x1e000 7.36 c9ab2fe0aa9e15bddb15e5e1b6327dbf .rsrc 0x2a3000 0x208 0x1000 0.53 348cd641b3fd1770f663114ca93ccbae ( 10 imports ) > dnssd.dll: DNSServiceRefDeallocate, DNSServiceRegister > SHELL32.dll: SHFileOperationW > LIBEXPAT.dll: -, -, -, -, -, -, -, -, - > ADVAPI32.dll: RegisterEventSourceA, ReportEventA, DeregisterEventSource, RegOpenKeyExA, RegQueryValueExA, RegEnumKeyW, RegOpenKeyExW, RegCreateKeyExW, RegQueryValueExW, RegCloseKey, RegSetValueExW, StartServiceCtrlDispatcherW, RegisterServiceCtrlHandlerW, SetServiceStatus, QueryServiceStatus, OpenServiceW, DeleteService, OpenSCManagerW, CloseServiceHandle, CreateServiceW > USER32.dll: MessageBoxA, GetUserObjectInformationW, KillTimer, GetDesktopWindow, wsprintfW, GetProcessWindowStation, SetTimer, wsprintfA > ole32.dll: CoCreateGuid, CoInitialize, CoCreateInstance, OleInitialize > MSVCP60.dll: ___D_$basic_stringstream@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEXXZ, __1_$basic_iostream@DU_$char_traits@D@std@@@std@@UAE@XZ, __1_$basic_istream@DU_$char_traits@D@std@@@std@@UAE@XZ, __1_$basic_ios@DU_$char_traits@D@std@@@std@@UAE@XZ, __1ios_base@std@@UAE@XZ, ___7_$basic_istream@DU_$char_traits@D@std@@@std@@6B@, ___7_$basic_ostream@DU_$char_traits@D@std@@@std@@6B@, __1locale@std@@QAE@XZ, ___7_$basic_streambuf@DU_$char_traits@D@std@@@std@@6B@, __Tidy@_$basic_stringbuf@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@IAEXXZ, ___7_$basic_stringbuf@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@6B@, _str@_$basic_stringstream@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBE_AV_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@2@XZ, __6std@@YAAAV_$basic_ostream@DU_$char_traits@D@std@@@0@AAV10@D@Z, ___7_$basic_stringstream@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@6B@, __0_$basic_stringbuf@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAE@H@Z, ___7_$basic_iostream@DU_$char_traits@D@std@@@std@@6B@, __0_$basic_ostream@DU_$char_traits@D@std@@@std@@QAE@PAV_$basic_streambuf@DU_$char_traits@D@std@@@1@_N1@Z, __0_$basic_istream@DU_$char_traits@D@std@@@std@@QAE@PAV_$basic_streambuf@DU_$char_traits@D@std@@@1@_N@Z, ___7_$basic_ios@DU_$char_traits@D@std@@@std@@6B@, ___8_$basic_stringstream@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@7B_$basic_ostream@DU_$char_traits@D@std@@@1@@, ___8_$basic_stringstream@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@7B_$basic_istream@DU_$char_traits@D@std@@@1@@, _find@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QBEIPBGII@Z, _append@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV12@ID@Z, _assign@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV12@PBD@Z, __1_$basic_streambuf@DU_$char_traits@D@std@@@std@@UAE@XZ, ___D_$basic_ofstream@DU_$char_traits@D@std@@@std@@QAEXXZ, __1_$basic_ostream@DU_$char_traits@D@std@@@std@@UAE@XZ, ___7_$basic_filebuf@DU_$char_traits@D@std@@@std@@6B@, _endl@std@@YAAAV_$basic_ostream@DU_$char_traits@D@std@@@1@AAV21@@Z, __6_$basic_ostream@DU_$char_traits@D@std@@@std@@QAEAAV01@N@Z, __6std@@YAAAV_$basic_ostream@DU_$char_traits@D@std@@@0@AAV10@PBD@Z, _clear@ios_base@std@@QAEXH_N@Z, __Initcvt@_$basic_filebuf@DU_$char_traits@D@std@@@std@@IAEXXZ, __Init@_$basic_filebuf@DU_$char_traits@D@std@@@std@@IAEXPAU_iobuf@@W4_Initfl@12@@Z, ___Fiopen@std@@YAPAU_iobuf@@PBDH@Z, ___7_$basic_ofstream@DU_$char_traits@D@std@@@std@@6B@, __0_$basic_filebuf@DU_$char_traits@D@std@@@std@@QAE@PAU_iobuf@@@Z, _init@_$basic_ios@DU_$char_traits@D@std@@@std@@IAEXPAV_$basic_streambuf@DU_$char_traits@D@std@@@2@_N@Z, __0ios_base@std@@IAE@XZ, ___8_$basic_ofstream@DU_$char_traits@D@std@@@std@@7B@, __9std@@YA_NABV_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@0@0@Z, _max_size@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBEIXZ, __4_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV01@PBD@Z, __4_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV01@ABV01@@Z, _length@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBEIXZ, _rfind@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBEIPBDI@Z, __4_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEAAV01@PBG@Z, __4_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEAAV01@ABV01@@Z, _find@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBEIPBDI@Z, __8std@@YA_NABV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@PBG@Z, __C@_1___Nullstr@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@CAPBDXZ@4DB, __Eos@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@AAEXI@Z, __Grow@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@AAE_NI_N@Z, __1_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAE@XZ, __Grow@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@AAE_NI_N@Z, __Xlen@std@@YAXXZ, __C@_1___Nullstr@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@CAPBGXZ@4GB, __Tidy@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@AAEX_N@Z, _assign@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEAAV12@ABV12@II@Z, _npos@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@2IB, __1_Lockit@std@@QAE@XZ, __0_Lockit@std@@QAE@XZ, _assign@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEAAV12@PBGI@Z, _rfind@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBEIPBDII@Z, __Copy@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@AAEXI@Z, _append@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEAAV12@PBGI@Z, __Hstd@@YA_AV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@ABV10@PBG@Z, __Hstd@@YA_AV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@ABV10@0@Z, __1_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAE@XZ, __Tidy@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@AAEX_N@Z, _c_str@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QBEPBGXZ, _append@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEAAV12@ABV12@II@Z, __Eos@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@AAEXI@Z, __Split@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@AAEXXZ, __Xran@std@@YAXXZ, _assign@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV12@ABV12@II@Z, _npos@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@2IB, _erase@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEAAV12@II@Z, __Copy@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@AAEXI@Z, __0_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAE@PBGABV_$allocator@G@1@@Z, _substr@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBE_AV12@II@Z, _find@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBEIPBDII@Z, _assign@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV12@PBDI@Z, __Split@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@AAEXXZ, _c_str@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QBEPBDXZ, __0_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAE@PBDABV_$allocator@D@1@@Z, __8std@@YA_NABV_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@0@PBD@Z, __0_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAE@ABV01@@Z, __Mstd@@YA_NABV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@0@Z, __Hstd@@YA_AV_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@0@PBDABV10@@Z, __Freeze@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@AAEXXZ, _erase@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV12@II@Z, __Hstd@@YA_AV_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@0@ABV10@PBD@Z, __Hstd@@YA_AV_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@0@ABV10@0@Z, __Hstd@@YA_AV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@PBGABV10@@Z, __0_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAE@ABV01@@Z, __8std@@YA_NABV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@0@Z, _append@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV12@ABV12@II@Z, _append@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV12@PBDI@Z, __Mstd@@YA_NABV_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@0@0@Z, _max_size@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QBEIXZ, _substr@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QBE_AV12@II@Z, __Freeze@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@AAEXXZ, _rfind@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QBEIPBGII@Z, __9std@@YA_NABV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@0@Z, __8std@@YA_NPBGABV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@@Z, __9std@@YA_NABV_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@0@PBG@Z, __Y_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAAV01@PBD@Z, _append@_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEAAV12@IG@Z, __8std@@YA_NABV_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@0@0@Z, __0_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAE@ABV_$allocator@D@1@@Z, __Refcnt@_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@AAEAAEPBD@Z, ___F_$basic_string@GU_$char_traits@G@std@@V_$allocator@G@2@@std@@QAEXXZ, __A_$basic_string@DU_$char_traits@D@std@@V_$allocator@D@2@@std@@QAEAADI@Z > MSVCRT.dll: wcsncmp, iswlower, iswalpha, towupper, _itow, _wutime, getc, iswdigit, putchar, tolower, iswalnum, mktime, sscanf, _wtol, isalnum, _wrmdir, abort, remove, modf, strlen, strcpy, strcat, strcmp, getenv, fflush, strerror, wcsstr, _vsnprintf, vfprintf, _pctype, __mb_cur_max, _isctype, gmtime, strtoul, fputs, signal, __dllonexit, _onexit, __1type_info@@UAE@XZ, _exit, _XcptFilter, __p___initenv, __getmainargs, _initterm, __setusermatherr, _adjust_fdiv, __p__commode, __p__fmode, __set_app_type, _except_handler3, _terminate@@YAXXZ, _controlfp, _open, _chmod, _utime, _strdup, _fstat, _close, _wcsnicmp, _strnicmp, _wcsicmp, _stricmp, isupper, strtol, wcsncpy, iswupper, towlower, iswspace, ctime, wcschr, isalpha, atol, perror, strstr, wcscmp, _CxxThrowException, time, srand, rand, rename, _setmode, fseek, ftell, _errno, frexp, ldexp, qsort, ceil, floor, calloc, toupper, memchr, realloc, _purecall, strrchr, sprintf, _stat, _unlink, wcscat, strncmp, strncpy, _iob, fwrite, fread, free, malloc, fopen, _wrename, _wunlink, _wopen, _wtoi, _ftol, fprintf, _wfopen, fgets, strchr, isspace, isdigit, fclose, _wstat, _lseek, _read, _write, _itoa, _ftime, _hypot, _fileno, _getch, atan, vsprintf, _open_osfhandle, _fdopen, setvbuf, _getpid, wcscpy, wcsrchr, atof, atoi, wcslen, __2@YAPAXI@Z, exit, printf, __CxxFrameHandler, islower, _putenv, raise, _setjmp3, memmove, _CIpow > WSOCK32.dll: -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, - > KERNEL32.dll: QueryPerformanceCounter, GetTickCount, GetVersionExA, FlushConsoleInputBuffer, SetEnvironmentVariableA, WriteConsoleA, LocalFree, LocalAlloc, FormatMessageA, AllocConsole, CreateEventA, ResetEvent, SetThreadIdealProcessor, GetStdHandle, GetFileType, GetVersion, GetCurrentThreadId, SetLastError, GetModuleHandleA, GetModuleFileNameA, LoadLibraryA, GetSystemDirectoryA, CreateMutexA, ReleaseMutex, FreeLibrary, GetEnvironmentVariableA, SearchPathA, GetModuleHandleW, GetProcAddress, GlobalMemoryStatus, TerminateProcess, SetThreadPriority, LeaveCriticalSection, TryEnterCriticalSection, EnterCriticalSection, DeleteCriticalSection, InitializeCriticalSection, CreateDirectoryW, GetExitCodeProcess, GetLocaleInfoW, MultiByteToWideChar, WideCharToMultiByte, GetDiskFreeSpaceExW, GetVolumeInformationW, SetErrorMode, GetLogicalDrives, GetDriveTypeW, CreateProcessW, GetComputerNameW, GetCurrentProcessId, GetSystemTimeAsFileTime, GetShortPathNameW, GetLongPathNameW, GetFullPathNameW, FileTimeToSystemTime, GetDateFormatW, CreateThread, GetFileAttributesW, GetTempPathA, GetLongPathNameA, GetFullPathNameA, FindFirstFileW, FindNextFileW, FindClose, GetLastError, CreateEventW, GetCurrentThread, CloseHandle, WaitForSingleObject, SetEvent, SuspendThread, ResumeThread, GetModuleFileNameW, Sleep, SetThreadAffinityMask, GetExitCodeThread, TlsSetValue, TlsGetValue, QueryPerformanceFrequency, TlsAlloc, GetSystemInfo, TlsFree, SleepEx, VirtualQuery, TerminateThread ( 0 exports ) Prevx info: http://info.prevx.com/aboutprogramtext.asp?PX5=E6D46F3700AA368CB04129623914A800B2D782F1 |
| | #5 |
| | TR/Crypt.XPACK.Gen in directx.exe teil 3: **************************************************************************************** E:\Programme\Simese\Simese.exe: Antivirus Version letzte aktualisierung Ergebnis AhnLab-V3 2008.4.15.0 2008.04.14 - AntiVir 7.6.0.85 2008.04.14 - Authentium 4.93.8 2008.04.13 - Avast 4.8.1169.0 2008.04.14 - AVG 7.5.0.516 2008.04.14 - BitDefender 7.2 2008.04.14 - CAT-QuickHeal 9.50 2008.04.14 - ClamAV 0.92.1 2008.04.14 - DrWeb 4.44.0.09170 2008.04.14 - eSafe 7.0.15.0 2008.04.09 - eTrust-Vet 31.3.5697 2008.04.14 - Ewido 4.0 2008.04.14 - F-Prot 4.4.2.54 2008.04.14 - F-Secure 6.70.13260.0 2008.04.14 - FileAdvisor 1 2008.04.14 - Fortinet 3.14.0.0 2008.04.14 - Ikarus T3.1.1.26 2008.04.14 - Kaspersky 7.0.0.125 2008.04.14 - McAfee 5273 2008.04.14 - Microsoft 1.3408 2008.04.14 - NOD32v2 3026 2008.04.14 - Norman 5.80.02 2008.04.14 - Panda 9.0.0.4 2008.04.14 - Prevx1 V2 2008.04.14 - Rising 20.40.02.00 2008.04.14 - Sophos 4.28.0 2008.04.14 - Sunbelt 3.0.1041.0 2008.04.12 - Symantec 10 2008.04.14 - TheHacker 6.2.92.277 2008.04.14 - VBA32 3.12.6.4 2008.04.14 - VirusBuster 4.3.26:9 2008.04.14 - Webwasher-Gateway 6.6.2 2008.04.14 - weitere Informationen File size: 832512 bytes MD5...: 62f53cd225d82b95a735e7a23fca7798 SHA1..: 5cae397696481b04affe7d46ccc911bb2a56f971 SHA256: 2d18e7178dc5b32c5e68c7f0a5fe59c65ad6ad95f85c6495531071337b91d3ca SHA512: 2ce6a9b3382139b4acb1827416218b89800c3c8a4f8ed34aca68fd13b3e9d62a 20f117e3b9dc61ce4bf00f0d7e1c7a64295c3fa33804742862e27d401b49f63c PEiD..: - PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x4a10ec timedatestamp.....: 0x2a425e19 (Fri Jun 19 22:22:17 1992) machinetype.......: 0x14c (I386) ( 8 sections ) name viradd virsiz rawdsiz ntrpy md5 CODE 0x1000 0xa0274 0xa0400 6.53 a42247b57ef9e73d2b7502562fad420c DATA 0xa2000 0x356c 0x3600 4.22 8016d622ad0c32d26f743eea498aebda BSS 0xa6000 0x1459 0x0 0.00 d41d8cd98f00b204e9800998ecf8427e .idata 0xa8000 0x2cc6 0x2e00 4.98 b68cfa2b549a634df999c6d4003c7927 .tls 0xab000 0x1c 0x0 0.00 d41d8cd98f00b204e9800998ecf8427e .rdata 0xac000 0x18 0x200 0.20 85422ac51edd7e06779c87424bb0834b .reloc 0xad000 0xd014 0xd200 6.60 cdaa9c6163d7e2744012537559b3dc7e .rsrc 0xbb000 0x17400 0x17400 4.06 8f5cc231b10ac13ba515299f72873fc5 ( 18 imports ) > kernel32.dll: GetCurrentThreadId, DeleteCriticalSection, LeaveCriticalSection, EnterCriticalSection, InitializeCriticalSection, VirtualFree, VirtualAlloc, LocalFree, LocalAlloc, InterlockedDecrement, InterlockedIncrement, VirtualQuery, WideCharToMultiByte, MultiByteToWideChar, lstrlenA, lstrcpynA, lstrcpyA, LoadLibraryExA, GetThreadLocale, GetStartupInfoA, GetProcAddress, GetModuleHandleA, GetModuleFileNameA, GetLocaleInfoA, GetLastError, GetCommandLineA, FreeLibrary, FindFirstFileA, FindClose, ExitProcess, ExitThread, CreateThread, WriteFile, UnhandledExceptionFilter, SetFilePointer, SetEndOfFile, RtlUnwind, ReadFile, RaiseException, GetStdHandle, GetFileSize, GetSystemTime, GetFileType, CreateFileA, CloseHandle > user32.dll: GetKeyboardType, LoadStringA, MessageBoxA, CharNextA > advapi32.dll: RegQueryValueExA, RegOpenKeyExA, RegCloseKey > oleaut32.dll: VariantChangeTypeEx, VariantCopyInd, VariantClear, SysStringLen, SysFreeString, SysReAllocStringLen, SysAllocStringLen > kernel32.dll: TlsSetValue, TlsGetValue, LocalAlloc, GetModuleHandleA, GetModuleFileNameA > advapi32.dll: SetSecurityDescriptorDacl, ReportEventA, RegisterEventSourceA, RegQueryValueExA, RegQueryInfoKeyA, RegOpenKeyExA, RegFlushKey, RegEnumKeyExA, RegCreateKeyExA, RegCloseKey, OpenProcessToken, InitializeSecurityDescriptor, GetUserNameA, GetTokenInformation, FreeSid, EqualSid, DeregisterEventSource, AllocateAndInitializeSid > kernel32.dll: lstrcpyA, WriteProcessMemory, WritePrivateProfileStringA, WriteFile, WaitForSingleObject, WaitForMultipleObjects, VirtualUnlock, VirtualQueryEx, VirtualQuery, VirtualProtect, VirtualLock, VirtualFree, VirtualAlloc, UnmapViewOfFile, TerminateProcess, SystemTimeToFileTime, SuspendThread, Sleep, SizeofResource, SetThreadPriority, SetThreadLocale, SetPriorityClass, SetLastError, SetFileTime, SetFilePointer, SetFileAttributesA, SetEvent, SetErrorMode, SetEndOfFile, SetCurrentDirectoryA, ResumeThread, ResetEvent, ReadProcessMemory, ReadFile, QueryPerformanceFrequency, QueryPerformanceCounter, OpenProcess, MultiByteToWideChar, MulDiv, MapViewOfFile, LockResource, LocalFree, LocalFileTimeToFileTime, LocalAlloc, LoadResource, LoadLibraryA, LeaveCriticalSection, IsBadReadPtr, InitializeCriticalSection, GlobalUnlock, GlobalReAlloc, GlobalHandle, GlobalLock, GlobalFree, GlobalDeleteAtom, GlobalAlloc, GlobalAddAtomA, GetWindowsDirectoryA, GetVersionExA, GetVersion, GetTimeZoneInformation, GetTickCount, GetThreadPriority, GetThreadLocale, GetTempPathA, GetSystemTime, GetSystemInfo, GetSystemDirectoryA, GetStringTypeExA, GetProfileStringA, GetProfileIntA, GetProcAddress, GetPrivateProfileStringA, GetPriorityClass, GetModuleHandleA, GetModuleFileNameA, GetLocaleInfoA, GetLocalTime, GetLastError, GetFullPathNameA, GetFileSize, GetFileAttributesA, GetExitCodeThread, GetExitCodeProcess, GetEnvironmentVariableA, GetDiskFreeSpaceA, GetDateFormatA, GetCurrentThreadId, GetCurrentThread, GetCurrentProcessId, GetCurrentProcess, GetComputerNameA, GetCPInfo, FreeResource, InterlockedIncrement, InterlockedExchange, InterlockedDecrement, FreeLibrary, FormatMessageA, FlushInstructionCache, FindResourceA, FindNextFileA, FindNextChangeNotification, FindFirstFileA, FindFirstChangeNotificationA, FindCloseChangeNotification, FindClose, FileTimeToLocalFileTime, FileTimeToDosDateTime, EnumCalendarInfoA, EnterCriticalSection, DuplicateHandle, DosDateTimeToFileTime, DeleteFileA, DeleteCriticalSection, CreateThread, CreateProcessA, CreatePipe, CreateMutexA, CreateFileMappingA, CreateFileA, CreateEventA, CreateDirectoryA, CompareStringA, CloseHandle > version.dll: VerQueryValueA, GetFileVersionInfoSizeA, GetFileVersionInfoA > gdi32.dll: UnrealizeObject, StretchBlt, SetWindowOrgEx, SetWinMetaFileBits, SetViewportOrgEx, SetTextColor, SetStretchBltMode, SetROP2, SetPixel, SetEnhMetaFileBits, SetDIBColorTable, SetBrushOrgEx, SetBkMode, SetBkColor, SelectPalette, SelectObject, SaveDC, RestoreDC, Rectangle, RectVisible, RealizePalette, Polyline, PlayEnhMetaFile, PatBlt, MoveToEx, MaskBlt, LineTo, IntersectClipRect, GetWindowOrgEx, GetWinMetaFileBits, GetTextMetricsA, GetTextExtentPointA, GetTextExtentPoint32A, GetSystemPaletteEntries, GetStockObject, GetPixel, GetPaletteEntries, GetObjectA, GetEnhMetaFilePaletteEntries, GetEnhMetaFileHeader, GetEnhMetaFileBits, GetDeviceCaps, GetDIBits, GetDIBColorTable, GetDCOrgEx, GetCurrentPositionEx, GetClipBox, GetBrushOrgEx, GetBitmapBits, ExtTextOutA, ExcludeClipRect, DeleteObject, DeleteEnhMetaFile, DeleteDC, CreateSolidBrush, CreatePenIndirect, CreatePalette, CreateHalftonePalette, CreateFontIndirectA, CreateDIBitmap, CreateDIBSection, CreateCompatibleDC, CreateCompatibleBitmap, CreateBrushIndirect, CreateBitmap, CopyEnhMetaFileA, BitBlt > user32.dll: WindowFromPoint, WinHelpA, WaitMessage, UpdateWindow, UnregisterClassA, UnionRect, UnhookWindowsHookEx, TranslateMessage, TranslateMDISysAccel, TrackPopupMenu, TabbedTextOutA, SystemParametersInfoA, ShowWindow, ShowScrollBar, ShowOwnedPopups, ShowCursor, SetWindowsHookExA, SetWindowTextA, SetWindowPos, SetWindowPlacement, SetWindowLongA, SetTimer, SetScrollRange, SetScrollPos, SetScrollInfo, SetRect, SetPropA, SetMenuItemInfoA, SetMenu, SetForegroundWindow, SetFocus, SetCursor, SetClassLongA, SetCapture, SetActiveWindow, SendNotifyMessageA, SendMessageA, ScrollWindow, ScrollDC, ScreenToClient, RemovePropA, RemoveMenu, ReleaseDC, ReleaseCapture, RegisterWindowMessageA, RegisterClipboardFormatA, RegisterClassA, PtInRect, PostThreadMessageA, PostQuitMessage, PostMessageA, PeekMessageA, OffsetRect, OemToCharA, MsgWaitForMultipleObjects, MessageBoxA, MapWindowPoints, MapVirtualKeyA, LoadStringA, LoadKeyboardLayoutA, LoadIconA, LoadCursorA, LoadBitmapA, KillTimer, IsZoomed, IsWindowVisible, IsWindowEnabled, IsWindow, IsRectEmpty, IsIconic, IsDialogMessageA, IsChild, IsCharAlphaA, InvalidateRect, IntersectRect, InsertMenuItemA, InsertMenuA, InflateRect, GetWindowThreadProcessId, GetWindowTextA, GetWindowRect, GetWindowPlacement, GetWindowLongA, GetWindowDC, GetTopWindow, GetTabbedTextExtentA, GetSystemMetrics, GetSystemMenu, GetSysColor, GetSubMenu, GetScrollRange, GetScrollPos, GetScrollInfo, GetPropA, GetParent, GetWindow, GetMessageA, GetMenuStringA, GetMenuState, GetMenuItemInfoA, GetMenuItemID, GetMenuItemCount, GetMenu, GetLastActivePopup, GetKeyboardState, GetKeyboardLayoutList, GetKeyboardLayout, GetKeyState, GetKeyNameTextA, GetIconInfo, GetForegroundWindow, GetFocus, GetDoubleClickTime, GetDesktopWindow, GetDCEx, GetDC, GetCursorPos, GetCursor, GetClipboardData, GetClientRect, GetClassNameA, GetClassInfoA, GetCapture, GetAsyncKeyState, GetActiveWindow, FrameRect, FindWindowA, FillRect, EqualRect, EnumWindows, EnumThreadWindows, EndPaint, EnableWindow, EnableScrollBar, EnableMenuItem, DrawTextA, DrawMenuBar, DrawIconEx, DrawIcon, DrawFrameControl, DrawFocusRect, DrawEdge, DispatchMessageA, DestroyWindow, DestroyMenu, DestroyIcon, DestroyCursor, DeleteMenu, DefWindowProcA, DefMDIChildProcA, DefFrameProcA, CreateWindowExA, CreatePopupMenu, CreateMenu, CreateIcon, ClientToScreen, CheckMenuItem, CallWindowProcA, CallNextHookEx, BeginPaint, AttachThreadInput, CharLowerBuffA, CharLowerA, CharUpperBuffA, AdjustWindowRectEx, ActivateKeyboardLayout > ole32.dll: CoUninitialize, CoInitialize, IsEqualGUID > oleaut32.dll: GetErrorInfo, SysFreeString > comctl32.dll: ImageList_SetIconSize, ImageList_GetIconSize, ImageList_Write, ImageList_Read, ImageList_GetDragImage, ImageList_DragShowNolock, ImageList_SetDragCursorImage, ImageList_DragMove, ImageList_DragLeave, ImageList_DragEnter, ImageList_EndDrag, ImageList_BeginDrag, ImageList_GetIcon, ImageList_Remove, ImageList_DrawEx, ImageList_Draw, ImageList_GetBkColor, ImageList_SetBkColor, ImageList_ReplaceIcon, ImageList_Add, ImageList_GetImageCount, ImageList_Destroy, ImageList_Create, InitCommonControls > shell32.dll: Shell_NotifyIconA, ShellExecuteA > wsock32.dll: socket, setsockopt, send, recvfrom, recv, inet_ntoa, inet_addr, htons, htonl, connect, closesocket, bind > iphlpapi.dll: GetIpAddrTable > advapi32.dll: StartServiceCtrlDispatcherA, SetServiceStatus, RegisterServiceCtrlHandlerA, OpenServiceA, OpenSCManagerA, DeleteService, CreateServiceA, CloseServiceHandle > kernel32.dll: GetProcAddress, LoadLibraryA, GetModuleHandleA ( 0 exports ) **************************************************************************************** E:\PROGRA~1\SQUEEZ~1\server\Bin\MSWIN3~1\mysqld.exe: Antivirus Version letzte aktualisierung Ergebnis AhnLab-V3 2008.4.15.0 2008.04.14 - AntiVir 7.6.0.85 2008.04.14 - Authentium 4.93.8 2008.04.13 - Avast 4.8.1169.0 2008.04.14 - AVG 7.5.0.516 2008.04.14 - BitDefender 7.2 2008.04.14 - CAT-QuickHeal 9.50 2008.04.14 - ClamAV 0.92.1 2008.04.14 - DrWeb 4.44.0.09170 2008.04.14 - eSafe 7.0.15.0 2008.04.09 - eTrust-Vet 31.3.5697 2008.04.14 - Ewido 4.0 2008.04.14 - F-Prot 4.4.2.54 2008.04.14 - F-Secure 6.70.13260.0 2008.04.14 - FileAdvisor 1 2008.04.14 - Fortinet 3.14.0.0 2008.04.14 - Ikarus T3.1.1.26 2008.04.14 - Kaspersky 7.0.0.125 2008.04.14 - McAfee 5273 2008.04.14 - Microsoft 1.3408 2008.04.14 - NOD32v2 3026 2008.04.14 - Norman 5.80.02 2008.04.14 - Panda 9.0.0.4 2008.04.14 - Prevx1 V2 2008.04.14 - Rising 20.40.02.00 2008.04.14 - Sophos 4.28.0 2008.04.14 - Sunbelt 3.0.1041.0 2008.04.12 - Symantec 10 2008.04.14 - TheHacker 6.2.92.277 2008.04.14 - VBA32 3.12.6.4 2008.04.14 - VirusBuster 4.3.26:9 2008.04.14 - Webwasher-Gateway 6.6.2 2008.04.14 - weitere Informationen File size: 4149248 bytes MD5...: 467a9a4d3356bda216251475fc5100a5 SHA1..: e2933359351794dcca40ede8bd123db8736f76ca SHA256: ea871fed3f8bb0658ddab1893d0dfd7b4cda93f1108207e77f0bf4328592525f SHA512: 1fb0617fb617a09aab273de2cdf4f95b1c98813e2cf8cc10cd457e756d5cb056 836ba249f474b5372ba3ab9694ad1598a21df493716ad2ab0386dca6029f5807 PEiD..: - PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x6209fc timedatestamp.....: 0x4476672d (Fri May 26 02:25:49 2006) machinetype.......: 0x14c (I386) ( 5 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0x23cac4 0x23d000 6.57 827a132cc5247c46ec66d775f6ff740d .rdata 0x23e000 0xa1d74 0xa2000 5.92 53070ed785290f2f8fd00b70c8e3c02c .data 0x2e0000 0x11f0f4 0x113000 5.23 b61b90f9c109d1b29e2c2f553af014fc .tls 0x400000 0x65 0x1000 0.00 620f0b67a91f7f74151bc5be745b7110 .rsrc 0x401000 0x118 0x1000 0.30 820e8d855508ef22e37bd463c756c6b0 ( 4 imports ) > WSOCK32.dll: -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, -, - > KERNEL32.dll: GetModuleFileNameA, InterlockedDecrement, SetEvent, Sleep, DisconnectNamedPipe, CancelIo, LocalFree, FormatMessageA, CreateNamedPipeA, ConnectNamedPipe, UnmapViewOfFile, GetCurrentThreadId, MapViewOfFile, CreateFileMappingA, CreateEventA, FreeConsole, SetThreadPriority, GetCurrentThread, GetCurrentProcessId, GetVersionExA, ResumeThread, GetCurrentProcess, LocalAlloc, lstrcpyA, lstrlenA, GetProcAddress, LoadLibraryExA, FreeLibrary, VirtualProtect, IsBadCodePtr, IsBadReadPtr, InitializeCriticalSection, DeleteCriticalSection, InterlockedExchangeAdd, InterlockedIncrement, EnterCriticalSection, LeaveCriticalSection, GetLastError, CreateFileA, WaitNamedPipeA, SetNamedPipeHandleState, CloseHandle, GetTickCount, GetLocaleInfoW, DuplicateHandle, SetFileAttributesA, RemoveDirectoryA, GetFileInformationByHandle, PeekNamedPipe, SetFileTime, LocalFileTimeToFileTime, SystemTimeToFileTime, SetEnvironmentVariableW, LockFile, WaitForSingleObject, FlushViewOfFile, SetUnhandledExceptionFilter, LoadLibraryA, SetEnvironmentVariableA, GetOEMCP, GetACP, CompareStringW, GetSystemDirectoryA, GetModuleHandleA, GetWindowsDirectoryA, GetLocaleInfoA, CreateSemaphoreA, ReleaseSemaphore, QueryPerformanceCounter, QueryPerformanceFrequency, GetSystemTimeAsFileTime, SetEndOfFile, SetFilePointer, GetSystemInfo, UnlockFile, GetVersion, GetFileAttributesExA, ReadFile, WriteFile, WaitForMultipleObjects, GetLocalTime, VirtualAlloc, FindFirstFileA, FindClose, FindNextFileA, CreateDirectoryA, DeleteFileA, MoveFileA, GetFileSize, FlushFileBuffers, GetOverlappedResult, CreateThread, ExitThread, ResetEvent, ReleaseMutex, CreateMutexA, ExitProcess, TerminateProcess, RtlUnwind, HeapAlloc, HeapFree, SetConsoleCtrlHandler, GetFileAttributesA, GetCommandLineA, WideCharToMultiByte, GetTimeZoneInformation, SetStdHandle, GetFileType, FileTimeToSystemTime, FileTimeToLocalFileTime, HeapReAlloc, GetFullPathNameA, GetDriveTypeA, SetHandleCount, GetStdHandle, GetStartupInfoA, TlsAlloc, SetLastError, TlsFree, TlsSetValue, TlsGetValue, RaiseException, HeapDestroy, HeapCreate, VirtualFree, IsBadWritePtr, HeapSize, UnhandledExceptionFilter, FreeEnvironmentStringsA, GetEnvironmentStrings, FreeEnvironmentStringsW, GetEnvironmentStringsW, GetCPInfo, GetUserDefaultLCID, EnumSystemLocalesA, IsValidLocale, IsValidCodePage, GetStringTypeA, MultiByteToWideChar, GetStringTypeW, GetCurrentDirectoryA, InterlockedExchange, VirtualQuery, LCMapStringA, LCMapStringW, SetCurrentDirectoryA, CompareStringA > USER32.dll: SetTimer, MessageBoxA, PeekMessageA, KillTimer > ADVAPI32.dll: CreateServiceA, StartServiceCtrlDispatcherA, QueryServiceConfigA, QueryServiceStatus, RegisterServiceCtrlHandlerA, OpenThreadToken, OpenProcessToken, GetTokenInformation, AllocateAndInitializeSid, EqualSid, CryptGenRandom, CryptAcquireContextA, CryptReleaseContext, IsValidSid, GetLengthSid, InitializeAcl, AddAccessAllowedAce, RegOpenKeyExA, RegEnumValueA, FreeSid, OpenSCManagerA, OpenServiceA, CloseServiceHandle, SetServiceStatus, InitializeSecurityDescriptor, SetSecurityDescriptorDacl, RegisterEventSourceA, ReportEventA, DeregisterEventSource, RegCreateKeyA, RegSetValueExA, RegCloseKey, DeleteService ( 0 exports ) **************************************************************************************** combofix.txt: ComboFix 08-04-13.3 - Moeli 2008-04-14 22:33:47.1 - NTFSx86 Microsoft Windows XP Professional 5.1.2600.2.1252.1.1031.18.384 [GMT 2:00] ausgeführt von:: E:\Dokumente und Einstellungen\Moeli\Desktop\ComboFix.exe * Neuer Wiederherstellungspunkt wurde erstellt WARNING -THIS MACHINE DOES NOT HAVE THE RECOVERY CONSOLE INSTALLED !! . (((((((((((((((((((((((((((((((((((( Weitere Löschungen )))))))))))))))))))))))))))))))))))))))))))))))) . E:\Dokumente und Einstellungen\LocalService\Lokale Einstellungen\Anwendungsdaten\Microsoft\Windows Media\10.0\WMSDKNSD.XML E:\WINDOWS\system32\Cache . ((((((((((((((((((((((( Dateien erstellt von 2008-03-14 bis 2008-04-14 )))))))))))))))))))))))))))))) . 2008-03-22 21:08 . 2008-03-22 21:08 <DIR> d-------- E:\Programme\SqueezeCenter 2008-03-22 21:07 . 2008-03-22 21:08 <DIR> d-------- E:\Dokumente und Einstellungen\All Users\Anwendungsdaten\SqueezeCenter 2008-03-19 21:47 . 2008-03-19 21:47 <DIR> d-------- E:\Programme\MagicISO . (((((((((((((((((((((((((((((((((((( Find3M Bericht )))))))))))))))))))))))))))))))))))))))))))))))))))))) . 2008-04-09 10:35 --------- d-----w E:\Dokumente und Einstellungen\Moeli\Anwendungsdaten\uTorrent 2008-04-09 10:14 --------- d-----w E:\Dokumente und Einstellungen\Moeli\Anwendungsdaten\Azureus 2008-04-09 10:11 --------- d-----w E:\Programme\ORF-Ski Challenge 2007 2008-04-06 16:15 --------- d-----w E:\Dokumente und Einstellungen\Moeli\Anwendungsdaten\Canon 2008-04-02 07:44 --------- d-----w E:\Dokumente und Einstellungen\Moeli\Anwendungsdaten\albumart 2008-03-22 19:08 --------- d-----w E:\Programme\SlimServer 2008-03-15 09:23 --------- d-----w E:\Programme\Emule 2008-03-09 11:08 --------- d-----w E:\Dokumente und Einstellungen\Moeli\Anwendungsdaten\FileZilla 2008-03-05 07:47 --------- d-----w E:\Programme\Tifny 2008-02-27 20:39 --------- d-----w E:\Dokumente und Einstellungen\Moeli\Anwendungsdaten\Skype 2008-02-18 19:07 --------- d-----w E:\Programme\uTorrent 2008-02-14 20:22 --------- d-----w E:\Programme\BitTorrent 2007-01-02 21:29 16 ---ha-w E:\Programme\mxfilerelatedcache.mxc2 2006-05-03 09:06 163,328 --sh--r E:\WINDOWS\system32\flvDX.dll 2007-02-21 10:47 31,232 --sh--r E:\WINDOWS\system32\msfDX.dll . (((((((((((((((((((((((((((( Autostart Punkte der Registrierung )))))))))))))))))))))))))))))))))))))))) . . REGEDIT4 *Hinweis* leere Eintrage & legitime Standardeintrage werden nicht angezeigt. [HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] "WebCamRT.exe"=":" [] "ctfmon.exe"="E:\WINDOWS\system32\ctfmon.exe" [2004-08-04 00:57 15360] "BitTorrent"="E:\Programme\BitTorrent\bittorrent.exe" [ ] "eyeBeam SIP Client"="" [] [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] "DU Meter"="E:\Programme\DU Meter\DUMeter.exe" [2001-10-13 01:31 1123328] "avgnt"="E:\Programme\AntiVir PersonalEdition Classic\avgnt.exe" [2007-10-14 12:09 249896] "PinnacleDriverCheck"="# E:\WINDOWS\system32\PSDrvCheck.exe" [ ] "PMCRemote"="# E:\Programme\Pinnacle\Shared Files\Programs\Remote\Remoterm.exe" [ ] "PMCS"="# E:\Programme\Pinnacle\Shared Files\Programs\MediaCenterService\PMC.Service.Main.exe" [ ] "NeroFilterCheck"="E:\WINDOWS\system32\NeroCheck.exe" [2001-07-09 10:50 155648] "VirtualCloneDrive"="E:\Programme\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe" [2005-04-12 17:27 45056] "ATICCC"="E:\Programme\ATI Technologies\ATI.ACE\CLIStart.exe" [2006-09-25 10:12 90112] "Adobe Reader Speed Launcher"="E:\Programme\Adobe\Reader 8.0\Reader\Reader_sl.exe" [2008-01-11 23:16 39792] [HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Run] "CTFMON.EXE"="E:\WINDOWS\System32\CTFMON.EXE" [2004-08-04 00:57 15360] E:\Dokumente und Einstellungen\All Users\Startmen\Programme\Autostart\ Bluetooth Manager.lnk - E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosBtMng1.exe [2004-12-21 20:42:32 45056] Pinnacle ShowCenter StreamServer.lnk - E:\Programme\Pinnacle\Shared Files\Programs\StrmServer\StrmServer.exe [2006-05-12 00:16:43 163840] SqueezeCenter-Taskleisten-Tool.lnk - E:\Programme\SqueezeCenter\SqueezeTray.exe [2008-03-22 21:08:08 1740887] [HKEY_LOCAL_MACHINE\software\microsoft\security center] "UpdatesDisableNotify"=dword:00000001 [HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile] "EnableFirewall"= 0 (0x0) [HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List] "%windir%\\system32\\sessmgr.exe"= "E:\\Programme\\InterVideo\\DVD6\\WinDVD.exe"= "E:\\Programme\\Emule\\emule.exe"= "E:\\Programme\\Messenger\\msmsgs.exe"= "E:\\WINDOWS\\system32\\dpvsetup.exe"= "E:\\WINDOWS\\system32\\rundll32.exe"= "E:\\Programme\\concept design\\onlineTV 2\\onlineTV.exe"= "E:\\Programme\\MusicIP\\MusicIP Mixer\\mDNSResponder.exe"= "E:\\Programme\\uTorrent\\uTorrent.exe"= "E:\\Programme\\Skype\\Phone\\Skype.exe"= [HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List] "3389:TCP"= 3389:TCP:@xpsp2res.dll,-22009 "9000:TCP"= 9000:TCP:SqueezeCenter 9000 tcp "3483:UDP"= 3483:UDP:SqueezeCenter 3483 udp "3483:TCP"= 3483:TCP:SqueezeCenter 3483 tcp R0 avgntmgr;avgntmgr;E:\WINDOWS\system32\drivers\avgntmgr.sys [2007-09-09 10:51] R0 DigiFilter;DigiFilter;E:\WINDOWS\system32\drivers\DigiFilt.sys [2005-10-25 23:19] R0 SI3112r;Silicon Image SiI 3112 SATARaid Controller;E:\WINDOWS\system32\DRIVERS\si3112r.sys [2003-02-24 05:21] R1 avgntdd;avgntdd;E:\WINDOWS\system32\DRIVERS\avgntdd.sys [2007-09-09 10:51] R2 cvintdrv;cvintdrv;E:\WINDOWS\system32\drivers\cvintdrv.sys [2000-09-07 10:00] R2 MusicIP Server;MusicIP Server;E:\Programme\MusicIP\MusicIP Mixer\MusicMagicServer.exe [2007-07-30 09:23] R2 SimeseServer;SimeseServer;E:\Programme\Simese\Simese.exe [2006-04-09 17:59] R2 SqueezeMySQL;SqueezeMySQL;E:\PROGRA~1\SQUEEZ~1\server\Bin\MSWIN3~1\mysqld.exe [2008-03-03 11:49] R2 SVKP;SVKP;E:\WINDOWS\System32\SVKP.sys [2004-06-03 21:27] R3 3xHybrid;Pinnacle PCTV 310i Stereo DVB-T;E:\WINDOWS\system32\DRIVERS\3xHybrid.sys [2005-09-02 14:43] R3 uscsc108;uscsc108;E:\WINDOWS\system32\DRIVERS\uscsc108.sys [2003-03-09 18:41] S0 ElbyVCD;ElbyVCD;E:\WINDOWS\system32\DRIVERS\ElbyVCD.sys [] S1 Asapi;Asapi;E:\WINDOWS\system32\drivers\Asapi.sys [2002-04-17 20:27] S1 lusbaudio;Logitech USB Microphone;E:\WINDOWS\system32\drivers\lvsound2.sys [2002-12-10 18:52] S3 FirebirdServerMAGIXInstance;Firebird Server - MAGIX Instance;E:\Programme\Common\Database\bin\fbserver.exe [2005-11-17 16:18] S3 hcdriver;EHCI;E:\WINDOWS\system32\Drivers\hcdriver.sys [2003-04-25 22:16] S3 HCWBT8XX;Hauppauge WinTV 848/9 WDM Video Driver;E:\WINDOWS\system32\drivers\HCWBT8XX.sys [2003-05-12 12:01] S3 LV506AV;Logitech QuickCam Cordless(PID_0430);E:\WINDOWS\system32\DRIVERS\LV506AV.SYS [2002-12-10 18:56] S3 Memctl;Memctl;E:\Programme\ABIT\FlashMenu\Memctl.sys [2001-11-29 19:49] S3 MIDUSB;Driver for MidiStuio-2;E:\WINDOWS\system32\Drivers\mstud-2drv.sys [2005-08-16 12:17] [HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\svchost] HPZ12 REG_MULTI_SZ Pml Driver HPZ12 Net Driver HPZ12 *Newly Created Service* - CATCHME . Inhalt des "geplante Tasks" Ordners "2007-07-20 21:38:28 E:\WINDOWS\Tasks\PMCS_Wakeup633205715083075056.job" - E:\Programme\Pinnacle\Shared Files\Programs\MediaCenterService\PMC.Service.Main.exe "2008-04-14 20:00:43 E:\WINDOWS\Tasks\StrmServer.job" - E:\Programme\Pinnacle\Shared Files\Programs\StrmServer\StrmServer.exe . ************************************************************************** catchme 0.3.1353 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net Rootkit scan 2008-04-14 22:37:47 Windows 5.1.2600 Service Pack 2 NTFS Scanne versteckte Prozesse... Scanne versteckte Autostart Einträge... Scanne versteckte Dateien... Scan erfolgreich abgeschlossen versteckte Dateien: 0 ************************************************************************** . Zeit der Fertigstellung: 2008-04-14 22:38:39 ComboFix-quarantined-files.txt 2008-04-14 20:38:13 17 Verzeichnis(se), 2,367,791,104 Bytes frei 21 Verzeichnis(se), 2,358,386,688 Bytes frei |
| | #6 |
| | TR/Crypt.XPACK.Gen in directx.exe teil 4 (letzer teil): **************************************************************************************** neues HJT-log: Logfile of Trend Micro HijackThis v2.0.2 Scan saved at 22:44:57, on 14.04.2008 Platform: Windows XP SP2 (WinNT 5.01.2600) MSIE: Internet Explorer v7.00 (7.00.5730.0011) Boot mode: Normal Running processes: E:\WINDOWS\System32\smss.exe E:\WINDOWS\system32\winlogon.exe E:\WINDOWS\system32\services.exe E:\WINDOWS\system32\lsass.exe E:\WINDOWS\system32\Ati2evxx.exe E:\WINDOWS\system32\svchost.exe E:\WINDOWS\System32\svchost.exe E:\WINDOWS\system32\Ati2evxx.exe E:\WINDOWS\system32\spoolsv.exe E:\Programme\AntiVir PersonalEdition Classic\sched.exe E:\Programme\AntiVir PersonalEdition Classic\avguard.exe E:\Programme\Digidesign\Drivers\MMERefresh.exe E:\Programme\Pinnacle\MediaServer\Microsoft SQL Server\MSSQL$PINNACLESYS\Binn\sqlservr.exe E:\Programme\MusicIP\MusicIP Mixer\MusicMagicServer.exe E:\WINDOWS\System32\svchost.exe E:\WINDOWS\System32\svchost.exe E:\Programme\Simese\Simese.exe E:\PROGRA~1\SQUEEZ~1\server\Bin\MSWIN3~1\mysqld.exe E:\WINDOWS\System32\svchost.exe e:\programme\pinnacle\shared files\programs\mediaserver\pmshost.exe E:\Programme\DU Meter\DUMeter.exe E:\Programme\AntiVir PersonalEdition Classic\avgnt.exe E:\Programme\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe E:\WINDOWS\system32\devldr32.exe E:\WINDOWS\system32\ctfmon.exe E:\Programme\ATI Technologies\ATI.ACE\CLI.EXE E:\Programme\Pinnacle\Shared Files\Programs\StrmServer\StrmServer.exe E:\Programme\SqueezeCenter\SqueezeTray.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosBtMng.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosA2dp.exe E:\PROGRA~1\SQUEEZ~1\server\SQUEEZ~1.EXE E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosBtHsp.exe E:\Programme\MusicIP\MusicIP Mixer\mDNSResponder.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\tosOBEX.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\tosBtProc.exe E:\Programme\ATI Technologies\ATI.ACE\cli.exe E:\WINDOWS\explorer.exe E:\Dokumente und Einstellungen\Moeli\Desktop\HiJackThis.exe R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.google.ch/ R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157 R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896 R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896 R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157 R1 - HKCU\Software\Microsoft\Internet Connection Wizard,ShellNext = http://www.google.ch/ O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - E:\Programme\Gemeinsame Dateien\Adobe\Acrobat\ActiveX\AcroIEHelper.dll O3 - Toolbar: (no name) - {42CDD1BF-3FFB-4238-8AD1-7859DF00B1D6} - (no file) O3 - Toolbar: (no name) - {BA52B914-B692-46c4-B683-905236F6F655} - (no file) O4 - HKLM\..\Run: [DU Meter] E:\Programme\DU Meter\DUMeter.exe O4 - HKLM\..\Run: [avgnt] "E:\Programme\AntiVir PersonalEdition Classic\avgnt.exe" /min O4 - HKLM\..\Run: [PinnacleDriverCheck] # E:\WINDOWS\system32\PSDrvCheck.exe -CheckReg O4 - HKLM\..\Run: [PMCRemote] # E:\Programme\Pinnacle\Shared Files\Programs\Remote\Remoterm.exe O4 - HKLM\..\Run: [PMCS] # "E:\Programme\Pinnacle\Shared Files\Programs\MediaCenterService\PMC.Service.Main.exe" -host -clearDebug O4 - HKLM\..\Run: [NeroFilterCheck] E:\WINDOWS\system32\NeroCheck.exe O4 - HKLM\..\Run: [VirtualCloneDrive] "E:\Programme\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe" /s O4 - HKLM\..\Run: [ATICCC] "E:\Programme\ATI Technologies\ATI.ACE\CLIStart.exe" O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "E:\Programme\Adobe\Reader 8.0\Reader\Reader_sl.exe" O4 - HKCU\..\Run: [WebCamRT.exe] : O4 - HKCU\..\Run: [ctfmon.exe] E:\WINDOWS\system32\ctfmon.exe O4 - HKCU\..\Run: [BitTorrent] "E:\Programme\BitTorrent\bittorrent.exe" --force_start_minimized O4 - HKUS\S-1-5-19\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'LOKALER DIENST') O4 - HKUS\S-1-5-20\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'NETZWERKDIENST') O4 - HKUS\S-1-5-18\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'SYSTEM') O4 - HKUS\.DEFAULT\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'Default user') O4 - Global Startup: AutorunsDisabled O4 - Global Startup: Bluetooth Manager.lnk = ? O4 - Global Startup: Pinnacle ShowCenter StreamServer.lnk = ? O4 - Global Startup: SqueezeCenter-Taskleisten-Tool.lnk = E:\Programme\SqueezeCenter\SqueezeTray.exe O8 - Extra context menu item: E&xport to Microsoft Excel - res://E:\PROGRA~1\MICROS~2\OFFICE11\EXCEL.EXE/3000 O9 - Extra button: (no name) - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - E:\WINDOWS\system32\msjava.dll O9 - Extra 'Tools' menuitem: Sun Java Konsole - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - E:\WINDOWS\system32\msjava.dll O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - E:\PROGRA~1\MICROS~2\OFFICE11\REFIEBAR.DLL O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - E:\Programme\Messenger\msmsgs.exe O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - E:\Programme\Messenger\msmsgs.exe O12 - Plugin for .fpx: C:\\Program Files\\Internet Explorer\\PLUGINS\\NPRVRT32.dll O12 - Plugin for .ivr: C:\\Program Files\\Internet Explorer\\PLUGINS\\NPRVRT32.dll O15 - Trusted Zone: http://linktrader.cyberspacehq.com O16 - DPF: {156BF4B7-AE3A-4365-BD88-95A75AF8F09D} (HPSDDX Class) - http://www.hp.com/cpso-support-new/SDD/hpsddObjSigned.cab O16 - DPF: {2CA0FF2C-0CE1-4382-A0C4-B2782965CCC2} (G-Vista ActiveX) - http://www.dilas.ch/plugin/gvista30/gvista30.cab O16 - DPF: {4ED9DDF0-7479-4BBE-9335-5A1EDB1D8A21} - http://download.mcafee.com/molbin/shared/mcinsctl/en-us/4,0,0,81/mcinsctl.cab O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1124829689790 O16 - DPF: {AE4CEC9D-C836-4579-829B-4C345101B3B9} (GVista Terrain Renderer) - http://www.dilas.ch/plugin/gvista/gvista2709.cab O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) - http://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab O23 - Service: AntiVir Scheduler (AntiVirScheduler) - Avira GmbH - E:\Programme\AntiVir PersonalEdition Classic\sched.exe O23 - Service: AntiVir PersonalEdition Classic Service (AntiVirService) - Avira GmbH - E:\Programme\AntiVir PersonalEdition Classic\avguard.exe O23 - Service: Ati HotKey Poller - ATI Technologies Inc. - E:\WINDOWS\system32\Ati2evxx.exe O23 - Service: ATI Smart - Unknown owner - E:\WINDOWS\system32\ati2sgag.exe O23 - Service: Bonjour Service - Apple Computer, Inc. - E:\Programme\MusicIP\MusicIP Mixer\mDNSResponder.exe O23 - Service: Digidesign MME Refresh Service (DigiRefresh) - Digidesign, A Division of Avid Technology, Inc. - E:\Programme\Digidesign\Drivers\MMERefresh.exe O23 - Service: digiSPTIService - Digidesign, A Division of Avid Technology, Inc. - E:\Programme\Digidesign\Pro Tools\digiSPTIService.exe O23 - Service: Firebird Server - MAGIX Instance (FirebirdServerMAGIXInstance) - MAGIX® - E:\Programme\Common\Database\bin\fbserver.exe O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - E:\Programme\Gemeinsame Dateien\InstallShield\Driver\1150\Intel 32\IDriverT.exe O23 - Service: MusicIP Server - Unknown owner - E:\Programme\MusicIP\MusicIP Mixer\MusicMagicServer.exe O23 - Service: Pinnacle Systems Media Service (PinnacleSys.MediaServer) - Pinnacle Systems - e:\programme\pinnacle\shared files\programs\mediaserver\pmshost.exe O23 - Service: SimeseServer - Mattic - E:\Programme\Simese\Simese.exe O23 - Service: SqueezeMySQL - Unknown owner - E:\PROGRA~1\SQUEEZ~1\server\Bin\MSWIN3~1\mysqld.exe -- End of file - 7926 bytes **************************************************************************************** |
| | #7 | ||
     | TR/Crypt.XPACK.Gen in directx.exe Hi, dann wollen wir mal: Also: Anleitung Avenger (by swandog46) 1.) Lade dir das Tool Avenger und speichere es auf dem Desktop: 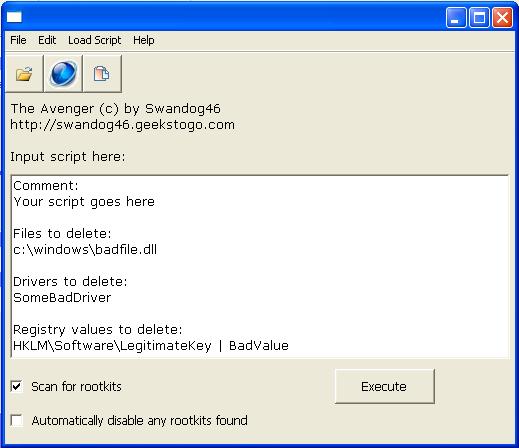 2.) Das Programm so einstellen wie es auf dem Bild zu sehen ist. Kopiere nun folgenden Text in das weiße Feld: (bei -> "input script here") Zitat:
4.) Um den Avenger zu starten klicke auf -> Execute Dann bestätigen mit "Yes" das der Rechner neu startet! 5.) Nachdem das System neu gestartet ist, findest du hier einen Report vom Avenger -> C:\avenger.txt Öffne die Datei mit dem Editor und kopiere den gesamten Text in deinen Beitrag hier am Trojaner-Board. Hijackthis, fixen: öffne das HijackThis -- Button "scan" -- vor den nachfolgenden Einträge Häkchen setzen -- Button "Fix checked" -- PC neustarten Beim fixen müssen alle Programme geschlossen sein! Zitat:
Unbekannt O16 - DPF: {2CA0FF2C-0CE1-4382-A0C4-B2782965CCC2} (G-Vista ActiveX) - http://www.dilas.ch/plugin/gvista30/gvista30.cab Falls nein, ebenfalls fixen... Scanne noch mit Dr. Web: Anleitung: Anleitung: DrWeb - CureIt - Anleitung Aber bitte den Download von hier nutzen http://freedrweb.com/?lng=de chris
__________________  Don't bring me down Don't bring me down Vor dem posten beachten! Spenden (Wer spenden will, kann sich gerne melden  ) ) |
| | #8 |
| | TR/Crypt.XPACK.Gen in directx.exe hi chris, alles soweit gemacht und hier sind die logs. gruss möli **************************************************************************************** avenger.txt: Logfile of The Avenger Version 2.0, (c) by Swandog46 http://swandog46.geekstogo.com Platform: Windows XP ******************* Script file opened successfully. Script file read successfully. Backups directory opened successfully at E:\Avenger ******************* Beginning to process script file: Rootkit scan active. No rootkits found! File "E:\WINDOWS\system32\directx.exe" deleted successfully. Error: file "E:\WINDOWS\Driver Cache\IEXPLORER.EXE" not found! Deletion of file "E:\WINDOWS\Driver Cache\IEXPLORER.EXE" failed! Status: 0xc0000034 (STATUS_OBJECT_NAME_NOT_FOUND) --> the object does not exist Completed script processing. ******************* Finished! Terminate. **************************************************************************************** entgegen der fehlermeldung von avenger, war das file IEXPLORER.EXE immer noch im entsprechenden verzeichnis zu finden: "Error: file "E:\WINDOWS\Driver Cache\IEXPLORER.EXE" not found!" nach zweimaligem ausführen von Dr. Web ist es nun auch weg. beim oder nach dem ersten run, kriegte ich einen blue-screen. **************************************************************************************** Dr. Web - CureIt.log: ----------------------------------------------------------------------------- Prüfstatistiken ----------------------------------------------------------------------------- Geprüfte Objekte: 199585 Infizierte Objekte gefunden: 3 Objekte mit Modifikation gefunden: 0 Verdächtige Objekte gefunden: 0 Adware-Programm gefunden: 0 Dialer-Programm gefunden: 0 Scherz-Programm gefunden: 0 Riskware programm gefunden: 0 Hacktool-Programm gefunden: 0 Desinfizierte Objekte: 0 Gelöschte Objekte: 0 Umbenannte Objekte: 0 Verschobene Objekte: 3 Ignorierte Objekte: 0 Leistung:: 38 Kb/s Dauer:: 01:57:29 ----------------------------------------------------------------------------- ============================================================================= Gesamte Sitzungsstatistik ============================================================================= Geprüfte Objekte: 200130 Infizierte Objekte gefunden: 3 Objekte mit Modifikation gefunden: 0 Verdächtige Objekte gefunden: 0 Adware-Programm gefunden: 0 Dialer-Programm gefunden: 0 Scherz-Programm gefunden: 0 Riskware programm gefunden: 0 Hacktool-Programm gefunden: 0 Desinfizierte Objekte: 0 Gelöschte Objekte: 0 Umbenannte Objekte: 0 Verschobene Objekte: 3 Ignorierte Objekte: 0 Leistung:: 66 Kb/s Dauer:: 01:58:51 ============================================================================= Dr. Web - DrWeb.csv: A0154276.EXE E:\System Volume Information\_restore{612B912B-4F63-43B3-A971-90C48ED208A5}\RP1022 Trojan.Click.origin Nicht desinfizierbar.Verschoben. A0155277.exe E:\System Volume Information\_restore{612B912B-4F63-43B3-A971-90C48ED208A5}\RP1022 Trojan.Click.origin Nicht desinfizierbar.Verschoben. A0155278.EXE E:\System Volume Information\_restore{612B912B-4F63-43B3-A971-90C48ED208A5}\RP1022 Trojan.Click.origin Nicht desinfizierbar.Verschoben. **************************************************************************************** HTJ-log: Logfile of Trend Micro HijackThis v2.0.2 Scan saved at 08:21:56, on 16.04.2008 Platform: Windows XP SP2 (WinNT 5.01.2600) MSIE: Internet Explorer v7.00 (7.00.5730.0011) Boot mode: Normal Running processes: E:\WINDOWS\System32\smss.exe E:\WINDOWS\system32\winlogon.exe E:\WINDOWS\system32\services.exe E:\WINDOWS\system32\lsass.exe E:\WINDOWS\system32\Ati2evxx.exe E:\WINDOWS\system32\svchost.exe E:\WINDOWS\System32\svchost.exe E:\WINDOWS\system32\Ati2evxx.exe E:\WINDOWS\system32\spoolsv.exe E:\Programme\AntiVir PersonalEdition Classic\sched.exe E:\Programme\AntiVir PersonalEdition Classic\avguard.exe E:\Programme\Digidesign\Drivers\MMERefresh.exe E:\Programme\Pinnacle\MediaServer\Microsoft SQL Server\MSSQL$PINNACLESYS\Binn\sqlservr.exe E:\Programme\MusicIP\MusicIP Mixer\MusicMagicServer.exe E:\WINDOWS\System32\svchost.exe E:\WINDOWS\System32\svchost.exe E:\Programme\Simese\Simese.exe E:\PROGRA~1\SQUEEZ~1\server\Bin\MSWIN3~1\mysqld.exe E:\WINDOWS\System32\svchost.exe e:\programme\pinnacle\shared files\programs\mediaserver\pmshost.exe E:\Programme\MusicIP\MusicIP Mixer\mDNSResponder.exe E:\WINDOWS\Explorer.EXE E:\Programme\DU Meter\DUMeter.exe E:\Programme\AntiVir PersonalEdition Classic\avgnt.exe E:\Programme\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe E:\Programme\ATI Technologies\ATI.ACE\CLI.EXE E:\WINDOWS\system32\ctfmon.exe E:\Programme\Pinnacle\Shared Files\Programs\StrmServer\StrmServer.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosBtMng.exe E:\Programme\SqueezeCenter\SqueezeTray.exe E:\WINDOWS\system32\devldr32.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosA2dp.exe E:\PROGRA~1\SQUEEZ~1\server\SQUEEZ~1.EXE E:\Programme\Toshiba\Bluetooth Toshiba Stack\TosBtHsp.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\tosOBEX.exe E:\Programme\Toshiba\Bluetooth Toshiba Stack\tosBtProc.exe E:\Programme\ATI Technologies\ATI.ACE\cli.exe E:\Programme\Internet Explorer\IEXPLORE.EXE E:\WINDOWS\system32\NOTEPAD.EXE E:\Dokumente und Einstellungen\Moeli\Desktop\HiJackThis.exe R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://www.google.ch/ R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157 R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896 R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896 R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157 R1 - HKCU\Software\Microsoft\Internet Connection Wizard,ShellNext = http://www.google.ch/ O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - E:\Programme\Gemeinsame Dateien\Adobe\Acrobat\ActiveX\AcroIEHelper.dll O4 - HKLM\..\Run: [DU Meter] E:\Programme\DU Meter\DUMeter.exe O4 - HKLM\..\Run: [avgnt] "E:\Programme\AntiVir PersonalEdition Classic\avgnt.exe" /min O4 - HKLM\..\Run: [PinnacleDriverCheck] # E:\WINDOWS\system32\PSDrvCheck.exe -CheckReg O4 - HKLM\..\Run: [PMCRemote] # E:\Programme\Pinnacle\Shared Files\Programs\Remote\Remoterm.exe O4 - HKLM\..\Run: [PMCS] # "E:\Programme\Pinnacle\Shared Files\Programs\MediaCenterService\PMC.Service.Main.exe" -host -clearDebug O4 - HKLM\..\Run: [NeroFilterCheck] E:\WINDOWS\system32\NeroCheck.exe O4 - HKLM\..\Run: [VirtualCloneDrive] "E:\Programme\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe" /s O4 - HKLM\..\Run: [ATICCC] "E:\Programme\ATI Technologies\ATI.ACE\CLIStart.exe" O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "E:\Programme\Adobe\Reader 8.0\Reader\Reader_sl.exe" O4 - HKCU\..\Run: [ctfmon.exe] E:\WINDOWS\system32\ctfmon.exe O4 - HKCU\..\Run: [BitTorrent] "E:\Programme\BitTorrent\bittorrent.exe" --force_start_minimized O4 - HKUS\S-1-5-19\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'LOKALER DIENST') O4 - HKUS\S-1-5-20\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'NETZWERKDIENST') O4 - HKUS\S-1-5-18\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'SYSTEM') O4 - HKUS\.DEFAULT\..\Run: [CTFMON.EXE] E:\WINDOWS\System32\CTFMON.EXE (User 'Default user') O4 - Global Startup: AutorunsDisabled O4 - Global Startup: Bluetooth Manager.lnk = ? O4 - Global Startup: Pinnacle ShowCenter StreamServer.lnk = ? O4 - Global Startup: SqueezeCenter-Taskleisten-Tool.lnk = E:\Programme\SqueezeCenter\SqueezeTray.exe O8 - Extra context menu item: E&xport to Microsoft Excel - res://E:\PROGRA~1\MICROS~2\OFFICE11\EXCEL.EXE/3000 O9 - Extra button: (no name) - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - E:\WINDOWS\system32\msjava.dll O9 - Extra 'Tools' menuitem: Sun Java Konsole - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - E:\WINDOWS\system32\msjava.dll O9 - Extra button: Research - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - E:\PROGRA~1\MICROS~2\OFFICE11\REFIEBAR.DLL O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - E:\Programme\Messenger\msmsgs.exe O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - E:\Programme\Messenger\msmsgs.exe O12 - Plugin for .fpx: C:\\Program Files\\Internet Explorer\\PLUGINS\\NPRVRT32.dll O12 - Plugin for .ivr: C:\\Program Files\\Internet Explorer\\PLUGINS\\NPRVRT32.dll O15 - Trusted Zone: http://linktrader.cyberspacehq.com O16 - DPF: {156BF4B7-AE3A-4365-BD88-95A75AF8F09D} (HPSDDX Class) - http://www.hp.com/cpso-support-new/SDD/hpsddObjSigned.cab O16 - DPF: {4ED9DDF0-7479-4BBE-9335-5A1EDB1D8A21} - http://download.mcafee.com/molbin/shared/mcinsctl/en-us/4,0,0,81/mcinsctl.cab O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1124829689790 O16 - DPF: {AE4CEC9D-C836-4579-829B-4C345101B3B9} (GVista Terrain Renderer) - http://www.dilas.ch/plugin/gvista/gvista2709.cab O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) - http://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab O23 - Service: AntiVir Scheduler (AntiVirScheduler) - Avira GmbH - E:\Programme\AntiVir PersonalEdition Classic\sched.exe O23 - Service: AntiVir PersonalEdition Classic Service (AntiVirService) - Avira GmbH - E:\Programme\AntiVir PersonalEdition Classic\avguard.exe O23 - Service: Ati HotKey Poller - ATI Technologies Inc. - E:\WINDOWS\system32\Ati2evxx.exe O23 - Service: ATI Smart - Unknown owner - E:\WINDOWS\system32\ati2sgag.exe O23 - Service: Bonjour Service - Apple Computer, Inc. - E:\Programme\MusicIP\MusicIP Mixer\mDNSResponder.exe O23 - Service: Digidesign MME Refresh Service (DigiRefresh) - Digidesign, A Division of Avid Technology, Inc. - E:\Programme\Digidesign\Drivers\MMERefresh.exe O23 - Service: digiSPTIService - Digidesign, A Division of Avid Technology, Inc. - E:\Programme\Digidesign\Pro Tools\digiSPTIService.exe O23 - Service: Firebird Server - MAGIX Instance (FirebirdServerMAGIXInstance) - MAGIX® - E:\Programme\Common\Database\bin\fbserver.exe O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - E:\Programme\Gemeinsame Dateien\InstallShield\Driver\1150\Intel 32\IDriverT.exe O23 - Service: MusicIP Server - Unknown owner - E:\Programme\MusicIP\MusicIP Mixer\MusicMagicServer.exe O23 - Service: Pinnacle Systems Media Service (PinnacleSys.MediaServer) - Pinnacle Systems - e:\programme\pinnacle\shared files\programs\mediaserver\pmshost.exe O23 - Service: SimeseServer - Mattic - E:\Programme\Simese\Simese.exe O23 - Service: SqueezeMySQL - Unknown owner - E:\PROGRA~1\SQUEEZ~1\server\Bin\MSWIN3~1\mysqld.exe -- End of file - 7692 bytes **************************************************************************************** |
| | #9 |
     | TR/Crypt.XPACK.Gen in directx.exe Hi, sieht soweit gut aus... Zur Sicherheit die Systemwiederherstellung löschen: Systemwiederherstellung löschen http://www.systemwiederherstellung-deaktivieren.de/windows-xp.html Wenn der Rechner einwandfrei läuft abschließend alle Systemwiederherstellungspunkte löschen lassen(das sind die: C:\System Volume Information\_restore - Dateien die gefunden wurden, d.h. der Trojaner wurde mit gesichert und wenn Du auf einen Restorepunkt zurück gehen solltest, dann ist er wieder da) wie folgt: Arbeitsplatz ->rechte Maus -> Eigenschaften -> Systemwiederherstellung -> anhaken: "Systemwiederherstellung auf allen Laufwerken deaktivieren" -> Übernehmen -> Sicherheitsabfrage OK -> Fenster mit OK schliessen -> neu Booten; Dann das gleiche nochmal nur das Häkchen entfernen (dann läuft sie wieder). Einen ersten Restorepunkt setzten: Start->Programme->Zubehör->Systemprogramme->Systemwiederherstellung->einen Wiederherstellungspunkt erstellen->weiter, Beschreibung ausdenken->Erstellen chris
__________________  Don't bring me down Don't bring me down Vor dem posten beachten! Spenden (Wer spenden will, kann sich gerne melden  ) ) |
| | #10 |
| | TR/Crypt.XPACK.Gen in directx.exe hallo chris! es sieht wieder prima aus. nach dem loeschen der recovery files hat Dr. Web keinen virus mehr gefunden. jetzt lasse ich gerade noch den antivir mein system scannen. uff, nun geht es mir gerade wieder viel besser ... ich danke dir unendlich fuer deine hilfbereitschaft und gut verstaendlichen anweisungen! noch eine frage ... weisst du, was dieser Crypt.XPACK.Gen virus anstellen kann? ist es denkbar, dass jemand fremder zugriff auf meinen PC hatte, daten verschickt wurden oder datenfiles veraendert wurden? nochmals herzlichen dank und mach weiter so. gruss moeli |
 |
| Themen zu TR/Crypt.XPACK.Gen in directx.exe |
| adobe, avira, bho, bonjour, computer, desktop, drivers, einstellungen, excel, helper, hijack, hijackthis, hkus\s-1-5-18, hotkey, internet, internet explorer, magix, microsoft, mssql, object, pdf, problem, programme, shockwave, software, system, torrent.exe, tr/crypt.xpack.ge, tr/crypt.xpack.gen, trojaner tr/crypt.xpack.gen, windows, windows xp |