
 |
| |||||||
Plagegeister aller Art und deren Bekämpfung: GVU Trojaner 2.12, Siredef, etc. eingefangenWindows 7 Wenn Du nicht sicher bist, ob Du dir Malware oder Trojaner eingefangen hast, erstelle hier ein Thema. Ein Experte wird sich mit weiteren Anweisungen melden und Dir helfen die Malware zu entfernen oder Unerwünschte Software zu deinstallieren bzw. zu löschen. Bitte schildere dein Problem so genau wie möglich. Sollte es ein Trojaner oder Viren Problem sein wird ein Experte Dir bei der Beseitigug der Infektion helfen. |
 |
| | #1 |
| | GVU Trojaner 2.12, Siredef, etc. eingefangen Hallo Helfer-Team, offenbar bin ich beim Schutz meines Systems sehr nachlässig vorgegangen, was sich letzte Woche bei mir gerächt hat. Ich wurde mit dem Sperrbildschirm einer Ransomware begrüßt ... wenn ich mich recht erinnere war es der "GVU Trojaner 2.12" (die Erinnerung kommt jenem Screenshot in der BKA-Trojaner-Galerie auf botfrei.de am nächsten). Ich habe ein paar Schritte unternommen in der Hoffnung, die Infektion zumindest teilweise bekämpfen zu können ... allerdings hält sich der Erfolg durchaus in Grenzen, weswegen ich auf fachkundige Hilfe hier hoffe. 1. Start im abgesicherten Modus, Systemwiederherstellung durchgeführt. Ich kann wieder auf den Desktop zugreifen. Aber ich verzichte vorerst darauf. 2. Laptop mit Kaspersky Rescue Disc gestartet. WindowsUnlocker laufen lassen. Log: Code:
ATTFilter Kaspersky Lab WindowsUnlocker, 2013
version 1.2.2 Feb 27 2013 09:42:26
Bearbeitet Volume "/discs/C:"
Registrierung "/discs/C:/windows/system32/config/system" wurde erfolgreich geöffnet
"AlternateShell" - OK
"AlternateShell" - OK
Registrierung "/discs/C:/windows/system32/config/software" wurde erfolgreich geöffnet
Windows wurde erkannt: Windows 7 Professional ( 7600.win7_gdr.130318-1532 ) C:\windows
Bearbeitet "Winlogon"
"Shell" - OK
"Userinit" - verdächtige Veränderung: C:\Windows\system32\userinit.exe,c:\Program Files (x86)\Hewlett-Packard\HP ProtectTools Security Manager\Bin\DPAgent.exe,
Userinit - wurde wiederhergestellt nach C:\windows\system32\userinit.exe,
Bearbeitet WOW64 "Winlogon"
"Shell" - OK
"Userinit" - OK
Bearbeitet "Windows"
Bearbeitet WOW64 "Windows"
Bearbeitet "Image File Execution Options"
Bearbeitet "Run"
Bearbeitet WOW64 "Run"
Bearbeitet Volume "/discs/Webbrowser"
Bearbeitet Volume "/discs/E:"
Bearbeitet Volume "/discs/Kaspersky Rescue Disk"
Bearbeitet Volume "/discs/sda1"
Bearbeitet Volume "/discs/Dateimanager"
Bearbeitet Volume "/discs/Kaspersky Registry Editor"
Bearbeitet Volume "/discs/F:"
Registrierung "/discs/C:/Windows/ServiceProfiles/LocalService/NTUSER.DAT" wurde erfolgreich geöffnet
Bearbeitet "Winlogon"
Bearbeitet "Windows"
Bearbeitet "Run"
Registrierung "/discs/C:/Windows/ServiceProfiles/NetworkService/NTUSER.DAT" wurde erfolgreich geöffnet
Bearbeitet "Winlogon"
Bearbeitet "Windows"
Bearbeitet "Run"
Registrierung "/discs/C:/Users/Jörg/NTUSER.DAT" wurde erfolgreich geöffnet
Bearbeitet "Winlogon"
Bearbeitet "Windows"
Bearbeitet "Run"
Bearbeitet /dev/sda
/dev/sda -> /var/kl/WUnlocker.1.2.2_04.05.2013_10.17.30_quarantine/krd0000.dta
Bearbeitet /dev/sda1
/dev/sda1 -> /var/kl/WUnlocker.1.2.2_04.05.2013_10.17.30_quarantine/krd0001.dta
Bearbeitet /dev/sda2
/dev/sda2 -> /var/kl/WUnlocker.1.2.2_04.05.2013_10.17.30_quarantine/krd0002.dta
Bearbeitet /dev/sda3
/dev/sda3 -> /var/kl/WUnlocker.1.2.2_04.05.2013_10.17.30_quarantine/krd0003.dta
Bearbeitet /dev/sda4
/dev/sda4 -> /var/kl/WUnlocker.1.2.2_04.05.2013_10.17.30_quarantine/krd0004.dta
Bearbeitet /dev/dm-0
/dev/dm-0 -> /var/kl/WUnlocker.1.2.2_04.05.2013_10.17.30_quarantine/krd0005.dta
3. Die Rescue Disc nach Viren/Trojaner/Malware suchen lassen. Log: Code:
ATTFilter Untersuchung von Objekten: wurde abgeschlossen vor weniger als einer Minute (Ereignis: 178, Objekte: 2840819, Zeit: 15:23:20)
05.05.13 01:42 Aufgabe wurde abgeschlossen
05.05.13 01:42 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33
05.05.13 01:42 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33
05.05.13 01:42 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33
05.05.13 01:42 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/5529023d-66787d3d
05.05.13 01:42 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/5529023d-66787d3d
05.05.13 01:42 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd
05.05.13 01:42 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd
05.05.13 01:41 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd
05.05.13 01:41 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee
05.05.13 01:41 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee
05.05.13 01:41 Gefunden: Exploit.Java.CVE-2012-1723.is /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee/Class2.class
05.05.13 01:41 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/52/4373f8f4-2fbc77e0
05.05.13 01:41 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/52/4373f8f4-2fbc77e0
05.05.13 01:41 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/38/711e1b66-2ee986be
05.05.13 01:41 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/38/711e1b66-2ee986be
05.05.13 01:41 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/37/2345d965-40ec2b5f
05.05.13 01:41 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/37/2345d965-40ec2b5f
05.05.13 01:41 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/28/6036dfdc-156e9d74
05.05.13 01:41 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/28/6036dfdc-156e9d74
05.05.13 01:41 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/22/5a8b0316-348c262c
05.05.13 01:40 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/22/5a8b0316-348c262c
05.05.13 01:40 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/60c2a012-6dba0c0c
05.05.13 01:40 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/60c2a012-6dba0c0c
05.05.13 01:40 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/5d2c0a52-31d1cc39
05.05.13 01:39 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/5d2c0a52-31d1cc39
05.05.13 01:39 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/11/3e94648b-70cb1d50
05.05.13 01:39 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/11/3e94648b-70cb1d50
05.05.13 01:39 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/0/e4915c0-748d45b0
05.05.13 01:39 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/0/e4915c0-748d45b0
05.05.13 01:39 Gelöscht: HEUR:Exploit.Java.CVE-2012-0507.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp
05.05.13 01:39 Gefunden: HEUR:Exploit.Java.CVE-2012-0507.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp
05.05.13 01:39 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
05.05.13 01:39 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
05.05.13 01:39 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
05.05.13 01:39 Gefunden: Exploit.Java.CVE-2012-1723.jr /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class
05.05.13 01:39 Gefunden: Exploit.Java.CVE-2012-1723.hn /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class
05.05.13 01:39 Gelöscht: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp
05.05.13 01:39 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp
05.05.13 01:39 Gefunden: Exploit.Java.CVE-2012-1723.cm /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class
05.05.13 01:38 Gefunden: Exploit.Java.CVE-2012-1723.cp /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class
05.05.13 01:38 Gelöscht: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/qeq8r.dat
05.05.13 01:37 Gefunden: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/qeq8r.dat
05.05.13 01:37 Gelöscht: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/llgr.dat
04.05.13 13:17 Gefunden: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/llgr.dat
04.05.13 12:15 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-0507.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp Zurückgestellt
04.05.13 12:15 Gefunden: HEUR:Exploit.Java.CVE-2012-0507.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp
04.05.13 12:12 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
04.05.13 12:12 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp Zurückgestellt
04.05.13 12:12 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
04.05.13 12:12 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.jr /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class Zurückgestellt
04.05.13 12:12 Gefunden: Exploit.Java.CVE-2012-1723.jr /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class
04.05.13 12:12 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.hn /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class Zurückgestellt
04.05.13 12:12 Gefunden: Exploit.Java.CVE-2012-1723.hn /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class
04.05.13 12:12 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp Zurückgestellt
04.05.13 12:12 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp
04.05.13 12:12 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.cm /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class Zurückgestellt
04.05.13 12:12 Gefunden: Exploit.Java.CVE-2012-1723.cm /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class
04.05.13 12:12 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.cp /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class Zurückgestellt
04.05.13 12:12 Gefunden: Exploit.Java.CVE-2012-1723.cp /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33 Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/5529023d-66787d3d Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/5529023d-66787d3d
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee
04.05.13 11:58 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.is C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee/Class2.class Zurückgestellt
04.05.13 11:58 Gefunden: Exploit.Java.CVE-2012-1723.is C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee/Class2.class
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/52/4373f8f4-2fbc77e0 Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/52/4373f8f4-2fbc77e0
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/38/711e1b66-2ee986be Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/38/711e1b66-2ee986be
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/37/2345d965-40ec2b5f Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/37/2345d965-40ec2b5f
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/28/6036dfdc-156e9d74 Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/28/6036dfdc-156e9d74
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/22/5a8b0316-348c262c Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/22/5a8b0316-348c262c
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/60c2a012-6dba0c0c Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/60c2a012-6dba0c0c
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/5d2c0a52-31d1cc39 Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/5d2c0a52-31d1cc39
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/11/3e94648b-70cb1d50 Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/11/3e94648b-70cb1d50
04.05.13 11:58 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/0/e4915c0-748d45b0 Zurückgestellt
04.05.13 11:58 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/0/e4915c0-748d45b0
04.05.13 11:57 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-0507.gen C:/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp Zurückgestellt
04.05.13 11:57 Gefunden: HEUR:Exploit.Java.CVE-2012-0507.gen C:/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp
04.05.13 11:50 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
04.05.13 11:50 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp Zurückgestellt
04.05.13 11:50 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
04.05.13 11:50 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.jr C:/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class Zurückgestellt
04.05.13 11:50 Gefunden: Exploit.Java.CVE-2012-1723.jr C:/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class
04.05.13 11:50 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.hn C:/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class Zurückgestellt
04.05.13 11:50 Gefunden: Exploit.Java.CVE-2012-1723.hn C:/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class
04.05.13 11:50 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp Zurückgestellt
04.05.13 11:50 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen C:/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp
04.05.13 11:50 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.cm C:/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class Zurückgestellt
04.05.13 11:50 Gefunden: Exploit.Java.CVE-2012-1723.cm C:/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class
04.05.13 11:50 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.cp C:/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class Zurückgestellt
04.05.13 11:50 Gefunden: Exploit.Java.CVE-2012-1723.cp C:/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class
04.05.13 11:33 Nicht desinfizierte Objekte: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/qeq8r.dat Zurückgestellt
04.05.13 11:33 Gefunden: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/qeq8r.dat
04.05.13 11:33 Nicht desinfizierte Objekte: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/llgr.dat Zurückgestellt
04.05.13 11:33 Gefunden: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/llgr.dat
04.05.13 11:10 Nicht desinfizierte Objekte: Trojan-Ransom.Win32.Foreign.bxjj C:/ProgramData/qeq8r.dat Zurückgestellt
04.05.13 11:10 Gefunden: Trojan-Ransom.Win32.Foreign.bxjj C:/ProgramData/qeq8r.dat
04.05.13 11:10 Nicht desinfizierte Objekte: Trojan-Ransom.Win32.Foreign.bxjj C:/ProgramData/llgr.dat Zurückgestellt
04.05.13 11:10 Gefunden: Trojan-Ransom.Win32.Foreign.bxjj C:/ProgramData/llgr.dat
04.05.13 10:51 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-0507.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp Zurückgestellt
04.05.13 10:51 Gefunden: HEUR:Exploit.Java.CVE-2012-0507.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp
04.05.13 10:46 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
04.05.13 10:46 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp Zurückgestellt
04.05.13 10:46 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
04.05.13 10:46 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.jr /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class Zurückgestellt
04.05.13 10:46 Gefunden: Exploit.Java.CVE-2012-1723.jr /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class
04.05.13 10:46 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.hn /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class Zurückgestellt
04.05.13 10:46 Gefunden: Exploit.Java.CVE-2012-1723.hn /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class
04.05.13 10:46 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp Zurückgestellt
04.05.13 10:46 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp
04.05.13 10:46 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.cm /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class Zurückgestellt
04.05.13 10:46 Gefunden: Exploit.Java.CVE-2012-1723.cm /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class
04.05.13 10:46 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.cp /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class Zurückgestellt
04.05.13 10:46 Gefunden: Exploit.Java.CVE-2012-1723.cp /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33 Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/9/6eadf189-14375f33
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/5529023d-66787d3d Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/5529023d-66787d3d
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/61/3144d27d-6ce7b2fd
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee
04.05.13 10:34 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.is /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee/Class2.class Zurückgestellt
04.05.13 10:34 Gefunden: Exploit.Java.CVE-2012-1723.is /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/59/491bbfb-640093ee/Class2.class
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/52/4373f8f4-2fbc77e0 Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/52/4373f8f4-2fbc77e0
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/38/711e1b66-2ee986be Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/38/711e1b66-2ee986be
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/37/2345d965-40ec2b5f Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/37/2345d965-40ec2b5f
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/28/6036dfdc-156e9d74 Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/28/6036dfdc-156e9d74
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/22/5a8b0316-348c262c Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/22/5a8b0316-348c262c
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/60c2a012-6dba0c0c Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/60c2a012-6dba0c0c
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/5d2c0a52-31d1cc39 Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/18/5d2c0a52-31d1cc39
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/11/3e94648b-70cb1d50 Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/11/3e94648b-70cb1d50
04.05.13 10:34 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/0/e4915c0-748d45b0 Zurückgestellt
04.05.13 10:34 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/LocalLow/Sun/Java/Deployment/cache/6.0/0/e4915c0-748d45b0
04.05.13 10:32 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-0507.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp Zurückgestellt
04.05.13 10:32 Gefunden: HEUR:Exploit.Java.CVE-2012-0507.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2347408806416956498.tmp
04.05.13 10:30 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
04.05.13 10:30 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp Zurückgestellt
04.05.13 10:30 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp
04.05.13 10:30 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.jr /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class Zurückgestellt
04.05.13 10:30 Nicht desinfizierte Objekte: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp Zurückgestellt
04.05.13 10:30 Gefunden: Exploit.Java.CVE-2012-1723.jr /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/vcs.class
04.05.13 10:30 Gefunden: HEUR:Exploit.Java.CVE-2012-1723.gen /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp
04.05.13 10:30 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.cm /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class Zurückgestellt
04.05.13 10:30 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.hn /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class Zurückgestellt
04.05.13 10:30 Gefunden: Exploit.Java.CVE-2012-1723.cm /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1a.class
04.05.13 10:30 Gefunden: Exploit.Java.CVE-2012-1723.hn /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache2141793567052607985.tmp/chcyih.class
04.05.13 10:30 Nicht desinfizierte Objekte: Exploit.Java.CVE-2012-1723.cp /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class Zurückgestellt
04.05.13 10:30 Gefunden: Exploit.Java.CVE-2012-1723.cp /mnt/MountedDevices/PD-F2D83907-0000000012D00000/Users/Jörg/AppData/Local/Temp/jar_cache1536752464902496919.tmp/l_r1a/l_r1c.class
04.05.13 10:20 Nicht desinfizierte Objekte: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/qeq8r.dat Zurückgestellt
04.05.13 10:20 Gefunden: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/qeq8r.dat
04.05.13 10:20 Nicht desinfizierte Objekte: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/llgr.dat Zurückgestellt
04.05.13 10:20 Gefunden: Trojan-Ransom.Win32.Foreign.bxjj /mnt/MountedDevices/PD-F2D83907-0000000012D00000/ProgramData/llgr.dat
04.05.13 10:19 Aufgabe wurde gestartet
4. Malwarebytes Anti-Malware installiert und suchen lassen. Log: Code:
ATTFilter Malwarebytes Anti-Malware 1.75.0.1300 www.malwarebytes.org Datenbank Version: v2013.05.05.03 Windows 7 x64 NTFS Internet Explorer 9.0.8112.16421 Jörg :: ****** [Administrator] 05.05.2013 12:28:56 mbam-log-2013-05-05 (12-28-56).txt Art des Suchlaufs: Vollständiger Suchlauf (C:\|D:\|E:\|F:\|Q:\|) Aktivierte Suchlaufeinstellungen: Speicher | Autostart | Registrierung | Dateisystem | Heuristiks/Extra | HeuristiKs/Shuriken | PUP | PUM Deaktivierte Suchlaufeinstellungen: P2P Durchsuchte Objekte: 467662 Laufzeit: 1 Stunde(n), 17 Minute(n), 8 Sekunde(n) Infizierte Speicherprozesse: 0 (Keine bösartigen Objekte gefunden) Infizierte Speichermodule: 0 (Keine bösartigen Objekte gefunden) Infizierte Registrierungsschlüssel: 0 (Keine bösartigen Objekte gefunden) Infizierte Registrierungswerte: 0 (Keine bösartigen Objekte gefunden) Infizierte Dateiobjekte der Registrierung: 0 (Keine bösartigen Objekte gefunden) Infizierte Verzeichnisse: 0 (Keine bösartigen Objekte gefunden) Infizierte Dateien: 0 (Keine bösartigen Objekte gefunden) (Ende) 5. Malwarebytes Anti-Rootkit heruntergeladen und suchen lassen. Danach Neustart des Systems. Log: Code:
ATTFilter Malwarebytes Anti-Rootkit BETA 1.05.0.1001
www.malwarebytes.org
Database version: v2013.05.05.04
Windows 7 x64 NTFS
Internet Explorer 9.0.8112.16421
Jörg :: ****** [administrator]
05.05.2013 15:16:04
mbar-log-2013-05-05 (15-16-04).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM | P2P
Scan options disabled:
Objects scanned: 30138
Time elapsed: 17 minute(s), 13 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 1
HKCU\SOFTWARE\CLASSES\CLSID\{fbeb8a05-beee-4442-804e-409d6c4515e9} (Hijack.Trojan.Siredef.C) -> Delete on reboot.
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 1
HKCU\SOFTWARE\CLASSES\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\INPROCSERVER32| (Trojan.0Access) -> Bad: (C:\$Recycle.Bin\S-1-5-21-2069978452-285043259-3883334984-1002\$1d9b1c173f91ffca9121b47860ae47af\n.) Good: (shell32.dll) -> Delete on reboot.
Folders Detected: 3
c:\$Recycle.Bin\S-1-5-21-2069978452-285043259-3883334984-1002\$1d9b1c173f91ffca9121b47860ae47af\U (Trojan.Siredef.C) -> Delete on reboot.
c:\$Recycle.Bin\S-1-5-21-2069978452-285043259-3883334984-1002\$1d9b1c173f91ffca9121b47860ae47af\L (Trojan.Siredef.C) -> Delete on reboot.
c:\$Recycle.Bin\S-1-5-21-2069978452-285043259-3883334984-1002\$1d9b1c173f91ffca9121b47860ae47af (Trojan.Siredef.C) -> Delete on reboot.
Files Detected: 1
c:\$Recycle.Bin\S-1-5-21-2069978452-285043259-3883334984-1002\$1d9b1c173f91ffca9121b47860ae47af\@ (Trojan.Siredef.C) -> Delete on reboot.
(end)
6. AdwCleaner heruntergeladen und mit "Löschen" arbeiten lassen. Danach Neustart des Systems. Log: Code:
ATTFilter # AdwCleaner v2.300 - Datei am 05/05/2013 um 15:52:21 erstellt
# Aktualisiert am 28/04/2013 von Xplode
# Betriebssystem : Windows 7 Professional (64 bits)
# Benutzer : Jörg - ******
# Bootmodus : Normal
# Ausgeführt unter : C:\Users\Jörg\Downloads\adwcleaner.exe
# Option [Löschen]
**** [Dienste] ****
***** [Dateien / Ordner] *****
***** [Registrierungsdatenbank] *****
Schlüssel Gelöscht : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{2FA28606-DE77-4029-AF96-B231E3B8F827}
Schlüssel Gelöscht : HKLM\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\SearchScopes\{2FA28606-DE77-4029-AF96-B231E3B8F827}
Schlüssel Gelöscht : HKLM\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{2FA28606-DE77-4029-AF96-B231E3B8F827}
***** [Internet Browser] *****
-\\ Internet Explorer v9.0.8112.16476
[OK] Die Registrierungsdatenbank ist sauber.
-\\ Mozilla Firefox v20.0.1 (de)
Datei : C:\Users\Jörg\AppData\Roaming\Mozilla\Firefox\Profiles\lrimm10i.default\prefs.js
[OK] Die Datei ist sauber.
*************************
AdwCleaner[S1].txt - [1073 octets] - [05/05/2013 15:52:21]
########## EOF - C:\AdwCleaner[S1].txt - [1133 octets] ##########
7. Avira AntiVir deinstalliert. Avast Free Antivirus heruntergeladen, installiert und suchen lassen. 4 infizierte Dateien in den "Temporary Internet Files" des IE wurden gefunden, welche ich vom Avast habe löschen lassen. Ein Log-File als gespeicherte Datei o.Ä. finde ich leider nicht. Ebenso keine entsprechende Funktion in Avast. Avast möchte nun einen Scan beim Systemstart ausführen. Nach dem Start des PCs kann ich mich nicht einloggen. Ich tippe mein Passwort für mein Benutzerkonto ein, aber die Enter-Taste zeigt keine Reaktion ... ebensowenig das Anklicken des "Pfeil"-Symboles. Nach einem weiteren Neustart des Laptops kann ich mich einloggen. Erhalte aber wie ein anderer User hier früher im Forum die Meldung "Ein kritischer Fehler ist aufgetreten. Windows wird in einer Minute neu gestartet. Speichern Sie jetzt Ihre Daten." (Beispiel: http://www.trojaner-board.de/121719-...-spoofing.html) Das wirkt nich authentisch, aber dafür so, als hätte Avast was aufgewühlt, was mich nun ärgert. Ein Starten im abgesicherten Modus ist noch möglich. Ein "normales" Hochfahren dauert seeeehr lange. Der Win7-Startbildschirm frohlockt fast eine ganze Minute mit "Willkommen". shutdown /A hilft leider nicht. Der Rechner startet dennoch neu. Auf msconfig kann ich nicht zugreifen. Nun ist es soweit, dass ich mir unsicher bin, ob Avast mein System "hasst" (was ich weniger vermute), oder ob irgendein Trojaner mich nun mit Zwangs-Neustarts ärgert (was ich eher vermute). Mit der Systemwiederherstellung will ich nun auch nicht wirklich hantieren ... am Ende wirds nurnoch noch schlimmer. 8. Malwarebytes Anti-Rootkit nochmal im abgesicherten Modus nochmal suchen gelassen ... ein Fund. Das Problem mit dem Zwangs-Neustarts behebt dies aber nicht. Der Fund ist im Prinzip auch nicht neu ... er trat schon beim ersten MBAR-Lauf auf. Log: Code:
ATTFilter Malwarebytes Anti-Rootkit BETA 1.05.0.1001
www.malwarebytes.org
Database version: v2013.05.05.04
Windows 7 x64 NTFS (Safe Mode)
Internet Explorer 9.0.8112.16421
Jörg :: ****** [administrator]
05.05.2013 19:52:11
mbar-log-2013-05-05 (19-52-11).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM | P2P
Scan options disabled:
Objects scanned: 29903
Time elapsed: 9 minute(s), 45 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 1
HKCU\SOFTWARE\CLASSES\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9} (Hijack.Trojan.Siredef.C) -> Delete on reboot.
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
Log: Code:
ATTFilter aswMBR version 0.9.9.1771 Copyright(c) 2011 AVAST Software
Run date: 2013-05-05 20:33:36
-----------------------------
20:33:36.757 OS Version: Windows x64 6.1.7600
20:33:36.757 Number of processors: 4 586 0x2A07
20:33:36.757 ComputerName: ****** UserName: Jörg
20:33:37.178 Initialize success
20:33:37.241 AVAST engine defs: 13050500
20:33:40.096 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Ide\IAAStorageDevice-1
20:33:40.096 Disk 0 Vendor: TOSHIBA_ MH00 Size: 305245MB BusType: 3
20:33:40.220 Disk 0 MBR read successfully
20:33:40.220 Disk 0 MBR scan
20:33:40.220 Disk 0 Windows 7 default MBR code
20:33:40.220 Disk 0 Partition 1 80 (A) 07 HPFS/NTFS NTFS 300 MB offset 2048
20:33:40.220 Disk 0 Partition 2 00 07 HPFS/NTFS NTFS 281595 MB offset 616448
20:33:40.252 Disk 0 Partition 3 00 07 HPFS/NTFS NTFS 18226 MB offset 577323008
20:33:40.267 Disk 0 Partition 4 00 0C FAT32 LBA MSDOS5.0 5115 MB offset 614649856
20:33:40.314 Disk 0 scanning C:\windows\system32\drivers
20:33:48.379 Service scanning
20:34:07.598 Modules scanning
20:34:07.598 Disk 0 trace - called modules:
20:34:07.630 ntoskrnl.exe CLASSPNP.SYS disk.sys hpdskflt.sys ACPI.sys iaStor.sys hal.dll
20:34:07.630 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0xfffffa800511a060]
20:34:07.645 3 CLASSPNP.SYS[fffff88001a8943f] -> nt!IofCallDriver -> [0xfffffa8004f8db10]
20:34:07.645 5 hpdskflt.sys[fffff8800140c361] -> nt!IofCallDriver -> [0xfffffa8004e9a880]
20:34:07.645 7 ACPI.sys[fffff88000f3a781] -> nt!IofCallDriver -> \Device\Ide\IAAStorageDevice-1[0xfffffa8004e9e050]
20:34:07.645 Scan finished successfully
21:57:34.665 Disk 0 MBR has been saved successfully to "D:\MBR.dat"
21:57:34.837 The log file has been saved successfully to "D:\aswMBR.txt"
10. Da keine emulierten Laufwerke vorhanden sind, lasse ich "Defogger" mal weg. "OTL" geladen und laufen lassen. Die beiden Log-Files befinden sich im Anhang dieses Beitrages, weil sie laut Forensoftware diesem zuviele Zeichen verpasst haben. Ich bitte dies zu entschuldigen. 11. Nun kommt GMER. Log: Code:
ATTFilter GMER 2.1.19163 - hxxp://www.gmer.net
Rootkit scan 2013-05-08 07:06:39
Windows 6.1.7600 x64 \Device\Harddisk0\DR0 -> \Device\Ide\IAAStorageDevice-1 TOSHIBA_ rev.MH00 298,09GB
Running: gem.exe; Driver: C:\Users\JRG~1\AppData\Local\Temp\pwldapog.sys
---- Threads - GMER 2.1 ----
Thread C:\windows\System32\svchost.exe [800:432] 000007fefc9b9688
---- Registry - GMER 2.1 ----
Reg HKLM\SYSTEM\CurrentControlSet\services\BTHPORT\Parameters\Keys\74de2b4caa39
Reg HKLM\SYSTEM\CurrentControlSet\services\BTHPORT\Parameters\Keys\74de2b4caa39@0013a970e0e8 0x50 0x59 0x62 0x8F ...
Reg HKLM\SYSTEM\ControlSet002\services\BTHPORT\Parameters\Keys\74de2b4caa39 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet002\services\BTHPORT\Parameters\Keys\74de2b4caa39@0013a970e0e8 0x50 0x59 0x62 0x8F ...
---- EOF - GMER 2.1 ----
So das war es vorerst mit Log-Files. Ich würde mich über Hinweise zum weiteren Vorgehen freuen. Danke. |
| | #2 |
| /// Helfer-Team        | GVU Trojaner 2.12, Siredef, etc. eingefangen Die Bereinigung besteht aus mehreren Schritten, die ausgefuehrt werden muessen. Diese Nacheinander abarbeiten und die 3 Logs, die dabei erstellt werden bitte in deine naechste Antwort einfuegen. Sollte der OTL-FIX nicht richig durchgelaufen sein. Fahre nicht fort, sondern melde dies bitte. 1. Schritt Fixen mit OTL Lade (falls noch nicht vorhanden) OTL von Oldtimer herunter und speichere es auf Deinem Desktop (nicht woanders hin).
Code:
ATTFilter :OTL
[2013.04.30 08:00:39 | 095,023,320 | ---- | M] () -- C:\ProgramData\r8qeq.pad
[2013.04.30 07:54:59 | 095,023,320 | ---- | M] () -- C:\ProgramData\rgll.pad
:Files
C:\ProgramData\*.exe
C:\ProgramData\*.dll
C:\ProgramData\*.tmp
C:\ProgramData\TEMP
C:\Users\Jörg\*.tmp
C:\Users\Jörg\AppData\*.dll
C:\Users\Jörg\AppData\*.exe
C:\Users\Jörg\AppData\Local\Temp\*.exe
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache
ipconfig /flushdns /c
:Commands
[emptytemp]
Hinweis für Mitleser: Obiges OTL-Script ist ausschließlich für diesen User in dieser Situtation erstellt worden. Auf keinen Fall auf anderen Rechnern anwenden, das kann andere Systeme nachhaltig schädigen! danach im NORMALEN Modus: Downloade Dir bitte
__________________ |
| | #3 | |
| | GVU Trojaner 2.12, Siredef, etc. eingefangen Hallo t'john.
__________________Danke für die schnelle Antwort. Hatte schon gesehen, dass du hier schon einigen weitergeholfen hast und bin optimistisch, dass der Fix hilft. Die beiden pad-Dateien kamen mir schon ominös vor, aber so mirnichts dirnichts wollte ich sie auch nicht löschen (auch wenn dies bei manch Anleitungen so vorgeschlagen wird). Wobei ... "2013.04.30 08:00:39" ... ja das müsste der Zeitpunkt gewesen sein, als mich der GVU-Trojaner-Bildschirm mir einen schlechten Morgen gewünscht hat. Ich werd den Fix mal heute Nachmittag arbeiten lassen, wenn ich zurück von der Arbeit bin. So ... hier die Logs. Von OTL: Code:
ATTFilter All processes killed
========== OTL ==========
C:\ProgramData\r8qeq.pad moved successfully.
C:\ProgramData\rgll.pad moved successfully.
========== FILES ==========
File\Folder C:\ProgramData\*.exe not found.
File\Folder C:\ProgramData\*.dll not found.
File\Folder C:\ProgramData\*.tmp not found.
File\Folder C:\ProgramData\TEMP not found.
File\Folder C:\Users\Jörg\*.tmp not found.
File\Folder C:\Users\Jörg\AppData\*.dll not found.
File\Folder C:\Users\Jörg\AppData\*.exe not found.
C:\Users\Jörg\AppData\Local\Temp\Extract.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\FP_PL_PFS_INSTALLER_32bit.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\HPHelpUpdater.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\InstallFlashPlayer.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\jre-6u37-windows-i586-iftw.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\Resource.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\SP52617.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\SP52772.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\SP53546.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\SP53628.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\SP53796.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\SP54149.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\SP54614.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\sp54620.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\SP54714.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\sp58915.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\UninstallHPSA.exe moved successfully.
C:\Users\Jörg\AppData\Local\Temp\UninstallHPTCA.exe moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\tmp folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\muffin folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\host folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\9 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\8 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\7 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\63 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\62 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\61 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\60 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\6 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\59 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\58 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\57 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\56 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\55 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\54 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\53 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\52 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\51 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\50 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\5 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\49 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\48 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\47 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\46 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\45 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\44 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\43 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\42 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\41 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\40 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\4 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\39 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\38 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\37 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\36 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\35 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\34 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\33 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\32 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\31 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\30 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\3 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\29 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\28 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\27 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\26 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\25 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\24 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\23 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\22 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\21 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\20 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\2 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\19 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\18 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\17 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\16 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\15 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\14 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\13 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\12 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\11 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\10 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\1 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\0 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache\6.0 folder moved successfully.
C:\Users\Jörg\AppData\LocalLow\Sun\Java\Deployment\cache folder moved successfully.
< ipconfig /flushdns /c >
Windows-IP-Konfiguration
Der DNS-Auflsungscache konnte nicht geleert werden: Beim Ausfhren der Funktion ist ein Fehler aufgetreten.
D:\cmd.bat deleted successfully.
D:\cmd.txt deleted successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 33170 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Jörg
->Temp folder emptied: 331239351 bytes
->Temporary Internet Files folder emptied: 480695308 bytes
->FireFox cache emptied: 79417471 bytes
->Flash cache emptied: 536 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 470864227 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 46356772 bytes
%systemroot%\sysnative\config\systemprofile\AppData\LocalLow\Sun\Java\Deployment folder emptied: 749 bytes
RecycleBin emptied: 10721275056 bytes
Total Files Cleaned = 11.568,00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 05082013_170724
Files\Folders moved on Reboot...
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
Von MBAM: Code:
ATTFilter Malwarebytes Anti-Malware 1.75.0.1300 www.malwarebytes.org Datenbank Version: v2013.05.05.03 Windows 7 x64 NTFS Internet Explorer 9.0.8112.16421 Jörg :: ***** [Administrator] 08.05.2013 17:21:12 mbam-log-2013-05-08 (17-21-12).txt Art des Suchlaufs: Vollständiger Suchlauf (C:\|D:\|E:\|F:\|Q:\|) Aktivierte Suchlaufeinstellungen: Speicher | Autostart | Registrierung | Dateisystem | Heuristiks/Extra | HeuristiKs/Shuriken | PUP | PUM Deaktivierte Suchlaufeinstellungen: P2P Durchsuchte Objekte: 460565 Laufzeit: 1 Stunde(n), 13 Minute(n), 4 Sekunde(n) Infizierte Speicherprozesse: 0 (Keine bösartigen Objekte gefunden) Infizierte Speichermodule: 0 (Keine bösartigen Objekte gefunden) Infizierte Registrierungsschlüssel: 0 (Keine bösartigen Objekte gefunden) Infizierte Registrierungswerte: 0 (Keine bösartigen Objekte gefunden) Infizierte Dateiobjekte der Registrierung: 0 (Keine bösartigen Objekte gefunden) Infizierte Verzeichnisse: 0 (Keine bösartigen Objekte gefunden) Infizierte Dateien: 0 (Keine bösartigen Objekte gefunden) (Ende) Kann ich die in MBAM-Quarantäne befindlichen Objekte (Trojan.Siredef.C und Trojan.0Access) löschen? by the way ... da das Systems erstmals seit ner Weile wieder "normal" gebootet ist, hat der adwclener noch zwei Logfiles ausgespuckt. Falls von Interesse: Code:
ATTFilter # AdwCleaner v2.300 - Datei am 06/05/2013 um 19:25:15 erstellt
# Aktualisiert am 28/04/2013 von Xplode
# Betriebssystem : Windows 7 Professional (64 bits)
# Benutzer : Jörg - ******
# Bootmodus : Abgesicherter Modus
# Ausgeführt unter : C:\Users\Jörg\Desktop\adwcleaner.exe
# Option [Suche]
**** [Dienste] ****
***** [Dateien / Ordner] *****
***** [Registrierungsdatenbank] *****
***** [Internet Browser] *****
-\\ Internet Explorer v9.0.8112.16476
[OK] Die Registrierungsdatenbank ist sauber.
-\\ Mozilla Firefox v20.0.1 (de)
Datei : C:\Users\Jörg\AppData\Roaming\Mozilla\Firefox\Profiles\lrimm10i.default\prefs.js
[OK] Die Datei ist sauber.
*************************
AdwCleaner[R1].txt - [718 octets] - [06/05/2013 19:25:15]
AdwCleaner[S1].txt - [1198 octets] - [05/05/2013 15:52:21]
########## EOF - C:\AdwCleaner[R1].txt - [837 octets] ##########
Code:
ATTFilter # AdwCleaner v2.300 - Datei am 06/05/2013 um 19:25:41 erstellt
# Aktualisiert am 28/04/2013 von Xplode
# Betriebssystem : Windows 7 Professional (64 bits)
# Benutzer : Jörg - ******
# Bootmodus : Abgesicherter Modus
# Ausgeführt unter : C:\Users\Jörg\Desktop\adwcleaner.exe
# Option [Löschen]
**** [Dienste] ****
***** [Dateien / Ordner] *****
***** [Registrierungsdatenbank] *****
***** [Internet Browser] *****
-\\ Internet Explorer v9.0.8112.16476
[OK] Die Registrierungsdatenbank ist sauber.
-\\ Mozilla Firefox v20.0.1 (de)
Datei : C:\Users\Jörg\AppData\Roaming\Mozilla\Firefox\Profiles\lrimm10i.default\prefs.js
[OK] Die Datei ist sauber.
*************************
AdwCleaner[R1].txt - [905 octets] - [06/05/2013 19:25:15]
AdwCleaner[S1].txt - [1198 octets] - [05/05/2013 15:52:21]
AdwCleaner[S2].txt - [839 octets] - [06/05/2013 19:25:41]
########## EOF - C:\AdwCleaner[S2].txt - [898 octets] ##########
Der betroffene Laptop war nun ne Weile an ... währenddessen hat sich Windows wohl Updates gezogen ... oder so. Es kam beim Hochfahren die Meldung "Windows wird konfiguriert. Schalten sie ihren Computer nicht aus.". Jedenfalls habe ich nun wieder folgedens Phänomen (wie oben schon beschrieben): Zitat:
|
| | #4 |
| | GVU Trojaner 2.12, Siredef, etc. eingefangen ------------------------ Hi nochmals. Ich habe nochmal versuch den Laptop zu booten ... das Problem bleibt bestehen, dass er nach einer Minute wieder neustartet. Das Hochfahren dauert mittlerweile sehr lange.  Ich habe in der Zwischenzeit nochmal OTL scannen lassen. Code:
ATTFilter OTL logfile created on: 11.05.2013 13:36:58 - Run 2 OTL by OldTimer - Version 3.2.69.0 Folder = D:\ 64bit- Professional (Version = 6.1.7600) - Type = NTWorkstation Internet Explorer (Version = 9.0.8112.16421) Locale: 00000407 | Country: Deutschland | Language: DEU | Date Format: dd.MM.yyyy 3,94 Gb Total Physical Memory | 2,71 Gb Available Physical Memory | 68,89% Memory free 7,87 Gb Paging File | 6,67 Gb Available in Paging File | 84,71% Paging File free Paging file location(s): ?:\pagefile.sys [binary data] %SystemDrive% = C: | %SystemRoot% = C:\windows | %ProgramFiles% = C:\Program Files (x86) Drive C: | 275,00 Gb Total Space | 176,52 Gb Free Space | 64,19% Space Free | Partition Type: NTFS Drive D: | 1,96 Gb Total Space | 0,75 Gb Free Space | 38,24% Space Free | Partition Type: FAT32 Drive E: | 17,80 Gb Total Space | 2,70 Gb Free Space | 15,19% Space Free | Partition Type: NTFS Drive F: | 4,98 Gb Total Space | 2,13 Gb Free Space | 42,69% Space Free | Partition Type: FAT32 Computer Name: ****** | User Name: Jörg | Logged in as Administrator. Boot Mode: SafeMode | Scan Mode: Current user | Include 64bit Scans Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days ========== Processes (SafeList) ========== PRC - [2013.05.07 21:48:46 | 000,602,112 | ---- | M] (OldTimer Tools) -- D:\OTL.exe ========== Modules (No Company Name) ========== ========== Services (SafeList) ========== SRV:64bit: - [2013.05.02 01:33:29 | 000,046,808 | ---- | M] (AVAST Software) [Auto | Stopped] -- C:\Program Files\AVAST Software\Avast\AvastSvc.exe -- (avast! Antivirus) SRV:64bit: - [2012.02.27 22:41:11 | 000,301,568 | ---- | M] (IDT, Inc.) [Auto | Stopped] -- C:\Program Files\IDT\WDM\STacSV64.exe -- (STacSV) SRV:64bit: - [2012.02.27 22:41:10 | 000,089,600 | ---- | M] (Andrea Electronics Corporation) [Auto | Stopped] -- C:\Program Files\IDT\WDM\AESTSr64.exe -- (AESTFilters) SRV:64bit: - [2011.08.23 05:37:04 | 003,175,728 | ---- | M] (Validity Sensors, Inc.) [Auto | Stopped] -- C:\Windows\SysNative\vcsFPService.exe -- (vcsFPService) SRV:64bit: - [2011.03.29 16:00:24 | 001,318,912 | ---- | M] () [Auto | Stopped] -- C:\Program Files\Hewlett-Packard\Drive Encryption\EEAgent\MfeEpeHost.exe -- (McAfee Endpoint Encryption Agent) SRV:64bit: - [2011.03.28 08:44:46 | 000,203,264 | ---- | M] (AMD) [Auto | Stopped] -- C:\Windows\SysNative\atiesrxx.exe -- (AMD External Events Utility) SRV:64bit: - [2011.02.12 05:07:16 | 000,481,104 | R--- | M] (DigitalPersona, Inc.) [Auto | Stopped] -- c:\Program Files\Hewlett-Packard\HP ProtectTools Security Manager\Bin\DpHostW.exe -- (DpHost) SRV:64bit: - [2011.01.28 18:41:30 | 000,133,688 | ---- | M] (Hewlett-Packard Company) [Auto | Stopped] -- c:\Program Files\Hewlett-Packard\HP DayStarter\32-bit\HPDayStarterService.exe -- (HPDayStarterService) SRV:64bit: - [2011.01.27 03:11:48 | 000,131,128 | ---- | M] (Hewlett-Packard Company) [Auto | Stopped] -- C:\Program Files\Hewlett-Packard\HP Power Assistant\HPPA_Service.exe -- (HP Power Assistant Service) SRV:64bit: - [2011.01.27 01:01:00 | 000,030,520 | ---- | M] (Hewlett-Packard Company) [Auto | Stopped] -- C:\Windows\SysNative\hpservice.exe -- (hpsrv) SRV:64bit: - [2009.07.14 03:41:27 | 001,011,712 | ---- | M] (Microsoft Corporation) [Auto | Running] -- C:\Program Files\Windows Defender\mpsvc.dll -- (WinDefend) SRV:64bit: - [2009.07.14 03:40:01 | 000,193,536 | ---- | M] (Microsoft Corporation) [On_Demand | Stopped] -- C:\Windows\SysNative\appmgmts.dll -- (AppMgmt) SRV - [2013.04.11 21:50:08 | 000,115,608 | ---- | M] (Mozilla Foundation) [On_Demand | Stopped] -- C:\Program Files (x86)\Mozilla Maintenance Service\maintenanceservice.exe -- (MozillaMaintenance) SRV - [2013.03.13 21:00:34 | 000,253,656 | ---- | M] (Adobe Systems Incorporated) [On_Demand | Stopped] -- C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe -- (AdobeFlashPlayerUpdateSvc) SRV - [2012.09.27 11:55:16 | 000,086,528 | ---- | M] (Hewlett-Packard Company) [Auto | Stopped] -- C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\hpsa_service.exe -- (HP Support Assistant Service) SRV - [2012.08.10 15:48:50 | 000,197,536 | ---- | M] (Hewlett-Packard Company) [Auto | Stopped] -- C:\Program Files (x86)\Hewlett-Packard\Shared\HPDrvMntSvc.exe -- (HPDrvMntSvc.exe) SRV - [2012.07.13 13:28:36 | 000,160,944 | R--- | M] (Skype Technologies) [Auto | Stopped] -- C:\Program Files (x86)\Skype\Updater\Updater.exe -- (SkypeUpdate) SRV - [2012.02.10 11:28:06 | 000,240,408 | ---- | M] (Microsoft Corporation.) [On_Demand | Stopped] -- C:\Program Files (x86)\Microsoft\BingBar\7.1.361.0\SeaPort.exe -- (BBUpdate) SRV - [2012.02.10 11:28:06 | 000,193,816 | ---- | M] (Microsoft Corporation.) [Auto | Stopped] -- C:\Program Files (x86)\Microsoft\BingBar\7.1.361.0\BBSvc.exe -- (BBSvc) SRV - [2011.10.01 08:30:22 | 000,219,496 | ---- | M] (Microsoft Corporation) [On_Demand | Stopped] -- C:\Program Files (x86)\Microsoft Application Virtualization Client\sftvsa.exe -- (sftvsa) SRV - [2011.10.01 08:30:18 | 000,508,776 | ---- | M] (Microsoft Corporation) [Auto | Stopped] -- C:\Program Files (x86)\Microsoft Application Virtualization Client\sftlist.exe -- (sftlist) SRV - [2011.08.23 05:23:48 | 002,774,320 | ---- | M] (Validity Sensors, Inc.) [Auto | Stopped] -- C:\Windows\SysWOW64\vcsFPService.exe -- (vcsFPService) SRV - [2011.04.05 20:13:46 | 001,094,712 | ---- | M] (Hewlett-Packard Development Company L.P.) [On_Demand | Stopped] -- c:\Program Files (x86)\Hewlett-Packard\HP Connection Manager\hpCMSrv.exe -- (hpCMSrv) SRV - [2011.03.07 22:48:10 | 000,062,184 | ---- | M] (Xobni Corporation) [Auto | Stopped] -- C:\Program Files (x86)\Xobni\XobniService.exe -- (XobniService) SRV - [2011.02.07 20:41:26 | 000,320,000 | ---- | M] (Hewlett-Packard) [Auto | Stopped] -- C:\Program Files (x86)\Hewlett-Packard\File Sanitizer\HPFSService.exe -- (HPFSService) SRV - [2011.02.04 00:09:18 | 000,464,480 | ---- | M] (Hewlett-Packard Company) [On_Demand | Stopped] -- c:\Windows\SysWOW64\flcdlock.exe -- (FLCDLOCK) SRV - [2011.02.01 10:23:10 | 001,127,448 | ---- | M] (PDF Complete Inc) [Auto | Stopped] -- C:\Program Files (x86)\PDF Complete\pdfsvc.exe -- (pdfcDispatcher) SRV - [2011.01.26 19:00:00 | 000,013,336 | ---- | M] (Intel Corporation) [Auto | Stopped] -- C:\Program Files (x86)\Intel\Intel(R) Rapid Storage Technology\IAStorDataMgrSvc.exe -- (IAStorDataMgrSvc) SRV - [2011.01.18 22:42:44 | 000,113,264 | ---- | M] (Portrait Displays, Inc.) [Auto | Stopped] -- C:\Program Files (x86)\Common Files\Portrait Displays\Drivers\pdisrvc.exe -- (PdiService) SRV - [2011.01.17 21:42:04 | 002,656,280 | ---- | M] (Intel Corporation) [Auto | Stopped] -- C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\UNS\UNS.exe -- (UNS) SRV - [2011.01.17 21:42:02 | 000,326,168 | ---- | M] (Intel Corporation) [Auto | Stopped] -- C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\LMS\LMS.exe -- (LMS) SRV - [2011.01.12 20:12:06 | 000,036,864 | ---- | M] (Hewlett-Packard Development Company, L.P) [On_Demand | Stopped] -- c:\Program Files (x86)\Hewlett-Packard\2009 Password Filter for HP ProtectTools\PTChangeFilterService.exe -- (HP ProtectTools Service) SRV - [2011.01.07 05:08:38 | 000,138,400 | ---- | M] (Atheros) [Auto | Stopped] -- C:\Program Files (x86)\Bluetooth Suite\Ath_CoexAgent.exe -- (Atheros Bt&Wlan Coex Agent) SRV - [2011.01.07 05:06:56 | 000,053,920 | ---- | M] (Atheros Commnucations) [Auto | Stopped] -- C:\Program Files (x86)\Bluetooth Suite\adminservice.exe -- (AtherosSvc) SRV - [2010.11.29 21:10:32 | 000,210,896 | ---- | M] (Intel Corporation) [Auto | Stopped] -- C:\Program Files (x86)\Intel\Services\IPT\jhi_service.exe -- (jhi_service) SRV - [2010.11.11 09:43:00 | 000,502,464 | ---- | M] (ArcSoft, Inc.) [Auto | Stopped] -- C:\Windows\SysWOW64\ArcVCapRender\uArcCapture.exe -- (uArcCapture) SRV - [2010.09.30 23:44:46 | 000,246,520 | ---- | M] (WildTangent, Inc.) [On_Demand | Stopped] -- C:\Program Files (x86)\HP Games\HP Game Console\GameConsoleService.exe -- (GameConsoleService) SRV - [2010.03.18 22:16:28 | 000,130,384 | ---- | M] (Microsoft Corporation) [Auto | Stopped] -- C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -- (clr_optimization_v4.0.30319_32) SRV - [2010.03.18 20:19:26 | 000,113,152 | ---- | M] (ArcSoft Inc.) [On_Demand | Stopped] -- C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACService.exe -- (ACDaemon) SRV - [2009.06.10 23:23:09 | 000,066,384 | ---- | M] (Microsoft Corporation) [Disabled | Stopped] -- C:\Windows\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe -- (clr_optimization_v2.0.50727_32) ========== Driver Services (SafeList) ========== DRV:64bit: - [2013.05.02 17:44:28 | 000,189,936 | ---- | M] () [Kernel | Boot | Stopped] -- C:\windows\SysNative\drivers\aswVmm.sys -- (aswVmm) DRV:64bit: - [2013.05.02 01:34:06 | 001,025,808 | ---- | M] (AVAST Software) [File_System | System | Stopped] -- C:\windows\SysNative\drivers\aswSnx.sys -- (aswSnx) DRV:64bit: - [2013.05.02 01:34:06 | 000,378,432 | ---- | M] (AVAST Software) [Kernel | System | Stopped] -- C:\windows\SysNative\drivers\aswSP.sys -- (aswSP) DRV:64bit: - [2013.05.02 01:34:06 | 000,072,016 | ---- | M] (AVAST Software) [Kernel | System | Stopped] -- C:\Windows\SysNative\drivers\aswRdr2.sys -- (aswRdr) DRV:64bit: - [2013.05.02 01:34:06 | 000,065,336 | ---- | M] () [Kernel | Boot | Stopped] -- C:\windows\SysNative\drivers\aswRvrt.sys -- (aswRvrt) DRV:64bit: - [2013.05.02 01:34:06 | 000,064,288 | ---- | M] (AVAST Software) [Kernel | System | Stopped] -- C:\windows\SysNative\drivers\aswTdi.sys -- (aswTdi) DRV:64bit: - [2013.05.02 01:34:05 | 000,080,816 | ---- | M] (AVAST Software) [File_System | Auto | Stopped] -- C:\Windows\SysNative\drivers\aswMonFlt.sys -- (aswMonFlt) DRV:64bit: - [2013.05.02 01:34:05 | 000,033,400 | ---- | M] (AVAST Software) [File_System | Auto | Stopped] -- C:\windows\SysNative\drivers\aswFsBlk.sys -- (aswFsBlk) DRV:64bit: - [2012.03.01 08:54:38 | 000,022,896 | ---- | M] (Microsoft Corporation) [Recognizer | Boot | Unknown] -- C:\windows\SysNative\drivers\fs_rec.sys -- (Fs_Rec) DRV:64bit: - [2012.02.27 22:41:12 | 000,528,384 | ---- | M] (IDT, Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\stwrt64.sys -- (STHDA) DRV:64bit: - [2011.10.01 08:30:22 | 000,022,376 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\Sftvollh.sys -- (Sftvol) DRV:64bit: - [2011.10.01 08:30:18 | 000,268,648 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\Sftplaylh.sys -- (Sftplay) DRV:64bit: - [2011.10.01 08:30:18 | 000,025,960 | ---- | M] (Microsoft Corporation) [File_System | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\Sftredirlh.sys -- (Sftredir) DRV:64bit: - [2011.10.01 08:30:10 | 000,764,264 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\Sftfslh.sys -- (Sftfs) DRV:64bit: - [2011.03.29 16:33:06 | 000,168,008 | ---- | M] (McAfee, Inc.) [Kernel | Boot | Running] -- C:\windows\SysNative\drivers\MfeEpePc.sys -- (MfeEpePc) DRV:64bit: - [2011.03.28 09:14:48 | 009,319,424 | ---- | M] (ATI Technologies Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\atikmdag.sys -- (amdkmdag) DRV:64bit: - [2011.03.28 08:09:12 | 000,303,616 | ---- | M] (Advanced Micro Devices, Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\atikmpag.sys -- (amdkmdap) DRV:64bit: - [2011.03.11 08:22:41 | 000,107,904 | ---- | M] (Advanced Micro Devices) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\amdsata.sys -- (amdsata) DRV:64bit: - [2011.03.11 08:22:40 | 000,027,008 | ---- | M] (Advanced Micro Devices) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\amdxata.sys -- (amdxata) DRV:64bit: - [2011.02.07 16:50:26 | 000,063,336 | ---- | M] (Hewlett-Packard Company) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\DAMDrv64.sys -- (DAMDrv) DRV:64bit: - [2011.02.04 05:59:06 | 001,413,680 | ---- | M] (Synaptics Incorporated) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\SynTP.sys -- (SynTP) DRV:64bit: - [2011.01.31 12:04:42 | 000,174,168 | ---- | M] (JMicron Technology Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\jmcr.sys -- (JMCR) DRV:64bit: - [2011.01.27 07:57:12 | 012,273,408 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\igdpmd64.sys -- (intelkmd) DRV:64bit: - [2011.01.27 01:01:00 | 000,043,320 | ---- | M] (Hewlett-Packard Company) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\Accelerometer.sys -- (Accelerometer) DRV:64bit: - [2011.01.27 01:01:00 | 000,030,008 | ---- | M] (Hewlett-Packard Company) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\hpdskflt.sys -- (hpdskflt) DRV:64bit: - [2011.01.13 03:51:44 | 000,439,320 | ---- | M] (Intel Corporation) [Kernel | Boot | Running] -- C:\Windows\SysNative\drivers\iaStor.sys -- (iaStor) DRV:64bit: - [2011.01.08 17:16:24 | 002,698,240 | ---- | M] (Atheros Communications, Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\athrx.sys -- (athr) DRV:64bit: - [2011.01.07 05:07:32 | 000,279,200 | ---- | M] (Atheros) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\btfilter.sys -- (BtFilter) DRV:64bit: - [2011.01.07 05:07:30 | 000,201,376 | ---- | M] (Atheros) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\btath_hcrp.sys -- (BTATH_HCRP) DRV:64bit: - [2011.01.07 05:07:30 | 000,154,272 | ---- | M] (Atheros) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\btath_rcp.sys -- (BTATH_RCP) DRV:64bit: - [2011.01.07 05:07:30 | 000,055,456 | ---- | M] (Atheros) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\btath_lwflt.sys -- (BTATH_LWFLT) DRV:64bit: - [2011.01.07 05:07:28 | 000,036,000 | ---- | M] (Atheros) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\btath_flt.sys -- (AthBTPort) DRV:64bit: - [2011.01.07 05:07:26 | 000,298,144 | ---- | M] (Atheros) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\btath_a2dp.sys -- (BTATH_A2DP) DRV:64bit: - [2011.01.07 05:07:26 | 000,028,832 | ---- | M] (Atheros) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\btath_bus.sys -- (BTATH_BUS) DRV:64bit: - [2010.12.21 19:21:16 | 001,826,048 | ---- | M] () [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\snp2uvc.sys -- (SNP2UVC) DRV:64bit: - [2010.12.10 23:50:36 | 000,181,248 | ---- | M] (Renesas Electronics Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\nusb3xhc.sys -- (nusb3xhc) DRV:64bit: - [2010.12.10 23:50:36 | 000,080,384 | ---- | M] (Renesas Electronics Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\nusb3hub.sys -- (nusb3hub) DRV:64bit: - [2010.12.03 02:02:58 | 000,025,912 | ---- | M] (Hewlett-Packard Company) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\HpqKbFiltr.sys -- (HpqKbFiltr) DRV:64bit: - [2010.11.30 18:32:38 | 000,406,632 | ---- | M] (Realtek ) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\Rt64win7.sys -- (RTL8167) DRV:64bit: - [2010.11.11 09:46:00 | 000,032,192 | ---- | M] (ArcSoft, Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\ArcSoftVCapture.sys -- (ARCVCAM) DRV:64bit: - [2010.10.29 05:05:56 | 000,109,056 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\sdbus.sys -- (sdbus) DRV:64bit: - [2010.10.20 03:34:26 | 000,056,344 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\HECIx64.sys -- (MEIx64) DRV:64bit: - [2010.10.14 22:28:16 | 000,317,440 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\IntcDAud.sys -- (IntcDAud) DRV:64bit: - [2009.12.31 12:04:57 | 000,360,712 | ---- | M] (Microsoft Corporation) [Kernel | System | Stopped] -- C:\Windows\SysNative\drivers\vpcvmm.sys -- (vpcvmm) DRV:64bit: - [2009.09.23 03:46:18 | 000,066,304 | ---- | M] (Microsoft Corporation) [Kernel | System | Stopped] -- C:\Windows\SysNative\drivers\vpcnfltr.sys -- (vpcnfltr) DRV:64bit: - [2009.09.23 03:32:39 | 000,095,232 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\vpcusb.sys -- (vpcusb) DRV:64bit: - [2009.09.23 03:32:33 | 000,187,904 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Running] -- C:\Windows\SysNative\drivers\vpchbus.sys -- (vpcbus) DRV:64bit: - [2009.07.14 03:52:20 | 000,194,128 | ---- | M] (AMD Technologies Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\amdsbs.sys -- (amdsbs) DRV:64bit: - [2009.07.14 03:48:04 | 000,065,600 | ---- | M] (LSI Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\lsi_sas2.sys -- (LSI_SAS2) DRV:64bit: - [2009.07.14 03:47:48 | 000,077,888 | ---- | M] (Hewlett-Packard Company) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\HpSAMD.sys -- (HpSAMD) DRV:64bit: - [2009.07.14 03:45:55 | 000,024,656 | ---- | M] (Promise Technology) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\stexstor.sys -- (stexstor) DRV:64bit: - [2009.07.14 01:21:48 | 000,038,400 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\tpm.sys -- (TPM) DRV:64bit: - [2009.06.10 23:01:06 | 001,146,880 | ---- | M] (LSI Corp) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\agrsm64.sys -- (AgereSoftModem) DRV:64bit: - [2009.06.10 22:34:33 | 003,286,016 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\evbda.sys -- (ebdrv) DRV:64bit: - [2009.06.10 22:34:28 | 000,468,480 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\bxvbda.sys -- (b06bdrv) DRV:64bit: - [2009.06.10 22:34:23 | 000,270,848 | ---- | M] (Broadcom Corporation) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\b57nd60a.sys -- (b57nd60a) DRV:64bit: - [2009.06.10 22:31:59 | 000,031,232 | ---- | M] (Hauppauge Computer Works, Inc.) [Kernel | On_Demand | Stopped] -- C:\Windows\SysNative\drivers\hcw85cir.sys -- (hcw85cir) DRV - [2009.07.14 03:19:10 | 000,019,008 | ---- | M] (Microsoft Corporation) [File_System | On_Demand | Stopped] -- C:\Windows\SysWOW64\drivers\wimmount.sys -- (WIMMount) ========== Standard Registry (SafeList) ========== ========== Internet Explorer ========== IE:64bit: - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = hxxp://g.uk.msn.com/HPCOM/10 IE:64bit: - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = hxxp://g.uk.msn.com/HPCOM/10 IE:64bit: - HKLM\..\SearchScopes,DefaultScope = IE:64bit: - HKLM\..\SearchScopes\{b7fca997-d0fb-4fe0-8afd-255e89cf9671}: "URL" = hxxp://de.search.yahoo.com/search?p={searchTerms}&ei={inputEncoding}&fr=chr-hp-psg&type=CMNTDF IE:64bit: - HKLM\..\SearchScopes\{ec29edf6-ad3c-4e1c-a087-d6cb81400c43}: "URL" = hxxp://www.bing.com/search?q={searchTerms}&form=CMNTDF&pc=CMNTDF&src=IE-SearchBox IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = hxxp://g.uk.msn.com/HPCOM/10 IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Local Page = C:\Windows\SysWOW64\blank.htm IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = hxxp://g.uk.msn.com/HPCOM/10 IE - HKLM\..\SearchScopes,DefaultScope = IE - HKLM\..\SearchScopes\{b7fca997-d0fb-4fe0-8afd-255e89cf9671}: "URL" = hxxp://de.search.yahoo.com/search?p={searchTerms}&ei={inputEncoding}&fr=chr-hp-psg&type=CMNTDF IE - HKLM\..\SearchScopes\{ec29edf6-ad3c-4e1c-a087-d6cb81400c43}: "URL" = hxxp://www.bing.com/search?q={searchTerms}&form=CMNTDF&pc=CMNTDF&src=IE-SearchBox IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = hxxp://g.uk.msn.com/HPCOM/10 IE - HKCU\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = about:blank IE - HKCU\..\SearchScopes,DefaultScope = IE - HKCU\..\SearchScopes\{b7fca997-d0fb-4fe0-8afd-255e89cf9671}: "URL" = hxxp://de.search.yahoo.com/search?p={searchTerms}&ei={inputEncoding}&fr=chr-hp-psg&type=CMNTDF IE - HKCU\..\SearchScopes\{C15A3503-647F-44E8-9F2B-B0A2411888B2}: "URL" = hxxp://www.google.de/search?q={searchTerms} IE - HKCU\..\SearchScopes\{ec29edf6-ad3c-4e1c-a087-d6cb81400c43}: "URL" = hxxp://www.bing.com/search?q={searchTerms}&form=CMNTDF&pc=CMNTDF&src=IE-SearchBox IE - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0 ========== FireFox ========== FF - prefs.js..browser.search.suggest.enabled: false FF - prefs.js..extensions.enabledAddons: %7Bb9db16a4-6edc-47ec-a1f4-b86292ed211d%7D:4.9.14 FF - prefs.js..extensions.enabledAddons: wrc%40avast.com:8.0.1488 FF - prefs.js..extensions.enabledAddons: %7B972ce4c6-7e08-4474-a285-3208198ce6fd%7D:20.0.1 FF - user.js - File not found FF:64bit: - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\windows\system32\Macromed\Flash\NPSWF64_11_6_602_180.dll File not found FF:64bit: - HKLM\Software\MozillaPlugins\@java.com/DTPlugin,version=10.17.2: C:\windows\system32\npDeployJava1.dll (Oracle Corporation) FF:64bit: - HKLM\Software\MozillaPlugins\@java.com/JavaPlugin,version=10.17.2: C:\Program Files\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation) FF:64bit: - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files\Microsoft Silverlight\5.1.20125.0\npctrl.dll ( Microsoft Corporation) FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\windows\SysWOW64\Macromed\Flash\NPSWF32_11_6_602_180.dll () FF - HKLM\Software\MozillaPlugins\@java.com/DTPlugin,version=10.17.2: C:\windows\SysWOW64\npDeployJava1.dll (Oracle Corporation) FF - HKLM\Software\MozillaPlugins\@java.com/JavaPlugin,version=10.17.2: C:\Program Files (x86)\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation) FF - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files (x86)\Microsoft Silverlight\5.1.20125.0\npctrl.dll ( Microsoft Corporation) FF - HKLM\Software\MozillaPlugins\@microsoft.com/SharePoint,version=14.0: C:\PROGRA~2\MICROS~1\Office14\NPSPWRAP.DLL (Microsoft Corporation) FF - HKLM\Software\MozillaPlugins\@microsoft.com/WLPG,version=15.4.3502.0922: C:\Program Files (x86)\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation) FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\otis@digitalpersona.com: c:\Program Files (x86)\Hewlett-Packard\HP ProtectTools Security Manager\Bin\FirefoxExt\ [2011.05.03 20:19:26 | 000,000,000 | ---D | M] FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\wrc@avast.com: C:\Program Files\AVAST Software\Avast\WebRep\FF [2013.05.05 16:11:25 | 000,000,000 | ---D | M] FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 20.0.1\extensions\\Components: C:\Program Files (x86)\Mozilla Firefox\components [2013.04.11 21:50:08 | 000,000,000 | ---D | M] FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 20.0.1\extensions\\Plugins: C:\Program Files (x86)\Mozilla Firefox\plugins [2012.02.20 22:15:32 | 000,000,000 | ---D | M] (No name found) -- C:\Users\Jörg\AppData\Roaming\mozilla\Extensions [2013.02.23 11:28:10 | 000,000,000 | ---D | M] (No name found) -- C:\Users\Jörg\AppData\Roaming\mozilla\Firefox\Profiles\lrimm10i.default\extensions [2013.02.23 11:28:10 | 000,000,000 | ---D | M] (DownloadHelper) -- C:\Users\Jörg\AppData\Roaming\mozilla\Firefox\Profiles\lrimm10i.default\extensions\{b9db16a4-6edc-47ec-a1f4-b86292ed211d} [2013.02.14 08:16:33 | 000,817,280 | ---- | M] () (No name found) -- C:\Users\Jörg\AppData\Roaming\mozilla\firefox\profiles\lrimm10i.default\extensions\{d10d0bf8-f5b5-c8b4-a8b2-2b9879e08c5d}.xpi [2013.04.11 21:50:05 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files (x86)\mozilla firefox\extensions [2013.05.05 16:11:25 | 000,000,000 | ---D | M] (avast! Online Security) -- C:\PROGRAM FILES\AVAST SOFTWARE\AVAST\WEBREP\FF File not found (No name found) -- C:\USERS\JöRG\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\LRIMM10I.DEFAULT\EXTENSIONS\{B9DB16A4-6EDC-47EC-A1F4-B86292ED211D} [2013.04.11 21:50:08 | 000,263,064 | ---- | M] (Mozilla Foundation) -- C:\Program Files (x86)\mozilla firefox\components\browsercomps.dll [2012.02.16 13:02:53 | 000,001,392 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\amazondotcom-de.xml [2012.09.23 17:35:42 | 000,002,465 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\bing.xml [2012.02.16 13:02:53 | 000,001,153 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\eBay-de.xml [2012.02.16 13:02:53 | 000,006,805 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\leo_ende_de.xml [2012.02.16 13:02:53 | 000,001,178 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\wikipedia-de.xml [2012.02.16 13:02:53 | 000,001,105 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\yahoo-de.xml O1 HOSTS File: ([2009.06.10 23:00:26 | 000,000,824 | ---- | M]) - C:\Windows\SysNative\drivers\etc\hosts O2:64bit: - BHO: (avast! Online Security) - {318A227B-5E9F-45bd-8999-7F8F10CA4CF5} - C:\Program Files\AVAST Software\Avast\aswWebRepIE64.dll (AVAST Software) O2:64bit: - BHO: (Java(tm) Plug-In SSV Helper) - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files\Java\jre7\bin\ssv.dll (Oracle Corporation) O2:64bit: - BHO: (Java(tm) Plug-In 2 SSV Helper) - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre7\bin\jp2ssv.dll (Oracle Corporation) O2 - BHO: (File Sanitizer for HP ProtectTools) - {3134413B-49B4-425C-98A5-893C1F195601} - C:\Program Files (x86)\Hewlett-Packard\File Sanitizer\IEBHO.dll (Hewlett-Packard) O2 - BHO: (Java(tm) Plug-In SSV Helper) - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files (x86)\Java\jre7\bin\ssv.dll (Oracle Corporation) O2 - BHO: (CIESpeechBHO Class) - {8D10F6C4-0E01-4BD4-8601-11AC1FDF8126} - C:\Program Files (x86)\Bluetooth Suite\IEPlugIn.dll (Atheros Commnucations) O2 - BHO: (avast! Online Security) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\AVAST Software\Avast\aswWebRepIE.dll (AVAST Software) O2 - BHO: (Bing Bar Helper) - {d2ce3e00-f94a-4740-988e-03dc2f38c34f} - C:\Program Files (x86)\Microsoft\BingBar\7.1.361.0\BingExt.dll (Microsoft Corporation.) O2 - BHO: (Java(tm) Plug-In 2 SSV Helper) - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files (x86)\Java\jre7\bin\jp2ssv.dll (Oracle Corporation) O2 - BHO: (HP Network Check Helper) - {E76FD755-C1BA-4DCB-9F13-99BD91223ADE} - C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\HPNetworkCheckPlugin.dll (Hewlett-Packard) O3:64bit: - HKLM\..\Toolbar: (avast! Online Security) - {318A227B-5E9F-45bd-8999-7F8F10CA4CF5} - C:\Program Files\AVAST Software\Avast\aswWebRepIE64.dll (AVAST Software) O3 - HKLM\..\Toolbar: (Bing Bar) - {8dcb7100-df86-4384-8842-8fa844297b3f} - C:\Program Files (x86)\Microsoft\BingBar\7.1.361.0\BingExt.dll (Microsoft Corporation.) O3 - HKLM\..\Toolbar: (avast! Online Security) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\AVAST Software\Avast\aswWebRepIE.dll (AVAST Software) O3 - HKCU\..\Toolbar\WebBrowser: (no name) - {7FEBEFE3-6B19-4349-98D2-FFB09D4B49CA} - No CLSID value found. O4:64bit: - HKLM..\Run: [AthBtTray] C:\Program Files (x86)\Bluetooth Suite\AthBtTray.exe (Atheros Commnucations) O4:64bit: - HKLM..\Run: [AtherosBtStack] C:\Program Files (x86)\Bluetooth Suite\BtvStack.exe (Atheros Communications) O4:64bit: - HKLM..\Run: [HotKeysCmds] C:\Windows\SysNative\hkcmd.exe (Intel Corporation) O4:64bit: - HKLM..\Run: [HPPowerAssistant] C:\Program Files\Hewlett-Packard\HP Power Assistant\DelayedAppStarter.exe () O4:64bit: - HKLM..\Run: [IgfxTray] C:\Windows\SysNative\igfxtray.exe (Intel Corporation) O4:64bit: - HKLM..\Run: [MfeEpePcMonitor] C:\Program Files\Hewlett-Packard\Drive Encryption\EpePcMonitor.exe () O4:64bit: - HKLM..\Run: [Persistence] C:\Windows\SysNative\igfxpers.exe (Intel Corporation) O4:64bit: - HKLM..\Run: [SysTrayApp] C:\Program Files\IDT\WDM\sttray64.exe (IDT, Inc.) O4 - HKLM..\Run: [] File not found O4 - HKLM..\Run: [avast] C:\Program Files\AVAST Software\Avast\avastUI.exe (AVAST Software) O4 - HKLM..\Run: [DTRun] c:\Program Files (x86)\ArcSoft\TotalMedia Suite\TotalMedia Theatre 3\uDTRun.exe (ArcSoft Inc.) O4 - HKLM..\Run: [File Sanitizer] C:\Program Files (x86)\Hewlett-Packard\File Sanitizer\CoreShredder.exe (Hewlett-Packard) O4 - HKLM..\Run: [HPConnectionManager] c:\Program Files (x86)\Hewlett-Packard\HP Connection Manager\HPCMDelayStart.exe (Hewlett-Packard Development Company L.P.) O4 - HKLM..\Run: [HPQuickWebProxy] c:\Program Files (x86)\Hewlett-Packard\HP QuickWeb\hpqwutils.exe (Hewlett-Packard Company) O4 - HKLM..\Run: [IAStorIcon] C:\Program Files (x86)\Intel\Intel(R) Rapid Storage Technology\IAStorIcon.exe (Intel Corporation) O4 - HKLM..\Run: [NUSB3MON] c:\Program Files (x86)\Renesas Electronics\USB 3.0 Host Controller Driver\Application\nusb3mon.exe (Renesas Electronics Corporation) O4 - HKLM..\Run: [PDF Complete] C:\Program Files (x86)\PDF Complete\pdfsty.exe (PDF Complete Inc) O4 - HKLM..\Run: [StartCCC] C:\Program Files (x86)\ATI Technologies\ATI.ACE\Core-Static\CLIStart.exe (Advanced Micro Devices, Inc.) O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoActiveDesktop = 1 O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoActiveDesktopChanges = 1 O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: ConsentPromptBehaviorAdmin = 5 O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: ConsentPromptBehaviorUser = 3 O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: PromptOnSecureDesktop = 0 O9:64bit: - Extra 'Tools' menuitem : Send by Bluetooth to - {7815BE26-237D-41A8-A98F-F7BD75F71086} - Reg Error: Value error. File not found O9 - Extra Button: @C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\HPNetworkCheckPlugin.dll,-103 - {25510184-5A38-4A99-B273-DCA8EEF6CD08} - C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\NCLauncherFromIE.exe (Hewlett-Packard) O9 - Extra 'Tools' menuitem : @C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\HPNetworkCheckPlugin.dll,-102 - {25510184-5A38-4A99-B273-DCA8EEF6CD08} - C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\NCLauncherFromIE.exe (Hewlett-Packard) O9 - Extra 'Tools' menuitem : Send by Bluetooth to - {7815BE26-237D-41A8-A98F-F7BD75F71086} - C:\Program Files (x86)\Bluetooth Suite\IEPlugIn.dll (Atheros Commnucations) O9 - Extra Button: @C:\Program Files (x86)\Evernote\Evernote\Resource.dll,-101 - {A95fe080-8f5d-11d2-a20b-00aa003c157a} - C:\Program Files (x86)\Evernote\Evernote\EvernoteIE.dll (Evernote Corp., 333 W Evelyn Ave. Mountain View, CA 94041) O9 - Extra 'Tools' menuitem : @C:\Program Files (x86)\Evernote\Evernote\Resource.dll,-101 - {A95fe080-8f5d-11d2-a20b-00aa003c157a} - C:\Program Files (x86)\Evernote\Evernote\EvernoteIE.dll (Evernote Corp., 333 W Evelyn Ave. Mountain View, CA 94041) O1364bit: - gopher Prefix: missing O13 - gopher Prefix: missing O16:64bit: - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} hxxp://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab (Shockwave Flash Object) O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.178.1 O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{20504772-5A65-488E-91A3-5D88D3BF1977}: DhcpNameServer = 192.168.178.1 O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{C7037444-9766-4FB0-9449-44E2692E1603}: DhcpNameServer = 192.168.178.1 O18:64bit: - Protocol\Handler\skype4com - No CLSID value found O18:64bit: - Protocol\Handler\wlpg - No CLSID value found O18 - Protocol\Handler\skype4com {FFC8B962-9B40-4DFF-9458-1830C7DD7F5D} - C:\PROGRA~2\COMMON~1\Skype\SKYPE4~1.DLL (Skype Technologies) O20:64bit: - HKLM Winlogon: Shell - (explorer.exe) - C:\windows\explorer.exe (Microsoft Corporation) O20:64bit: - HKLM Winlogon: UserInit - (C:\windows\system32\userinit.exe) - C:\Windows\SysNative\userinit.exe (Microsoft Corporation) O20 - HKLM Winlogon: Shell - (explorer.exe) - C:\windows\SysWow64\explorer.exe (Microsoft Corporation) O20 - HKLM Winlogon: UserInit - (userinit.exe) - C:\windows\SysWow64\userinit.exe (Microsoft Corporation) O20:64bit: - Winlogon\Notify\igfxcui: DllName - (igfxdev.dll) - C:\windows\SysNative\igfxdev.dll (Intel Corporation) O20 - Winlogon\Notify\DeviceNP: DllName - (DeviceNP.dll) - C:\windows\SysWow64\DeviceNP.dll (Hewlett-Packard Company) O21:64bit: - SSODL: WebCheck - {E6FB5E20-DE35-11CF-9C87-00AA005127ED} - No CLSID value found. O21 - SSODL: WebCheck - {E6FB5E20-DE35-11CF-9C87-00AA005127ED} - No CLSID value found. O31 - SafeBoot: UseAlternatShell - 1 O32 - HKLM CDRom: AutoRun - 1 O34 - HKLM BootExecute: (autocheck autochk *) O35:64bit: - HKLM\..comfile [open] -- "%1" %* O35:64bit: - HKLM\..exefile [open] -- "%1" %* O35 - HKLM\..comfile [open] -- "%1" %* O35 - HKLM\..exefile [open] -- "%1" %* O37:64bit: - HKLM\...com [@ = comfile] -- "%1" %* O37:64bit: - HKLM\...exe [@ = exefile] -- "%1" %* O37 - HKLM\...com [@ = comfile] -- "%1" %* O37 - HKLM\...exe [@ = exefile] -- "%1" %* O38 - SubSystems\\Windows: (ServerDll=winsrv:UserServerDllInitialization,3) O38 - SubSystems\\Windows: (ServerDll=winsrv:ConServerDllInitialization,2) O38 - SubSystems\\Windows: (ServerDll=sxssrv,4) ========== Files/Folders - Created Within 30 Days ========== [2013.05.08 23:09:24 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\ESET [2013.05.07 21:55:12 | 000,000,000 | -HSD | C] -- C:\found.000 [2013.05.05 20:12:44 | 004,745,728 | ---- | C] (AVAST Software) -- C:\Users\Jörg\Desktop\aswMBR.exe [2013.05.05 16:12:00 | 000,378,432 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswSP.sys [2013.05.05 16:12:00 | 000,033,400 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswFsBlk.sys [2013.05.05 16:12:00 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\avast! Free Antivirus [2013.05.05 16:11:59 | 000,072,016 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswRdr2.sys [2013.05.05 16:11:58 | 001,025,808 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswSnx.sys [2013.05.05 16:11:58 | 000,064,288 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswTdi.sys [2013.05.05 16:11:52 | 000,080,816 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswMonFlt.sys [2013.05.05 16:11:48 | 000,287,840 | ---- | C] (AVAST Software) -- C:\windows\SysNative\aswBoot.exe [2013.05.05 16:11:12 | 000,041,664 | ---- | C] (AVAST Software) -- C:\windows\avastSS.scr [2013.05.05 16:10:57 | 000,000,000 | ---D | C] -- C:\Program Files\AVAST Software [2013.05.05 16:08:52 | 000,000,000 | ---D | C] -- C:\ProgramData\AVAST Software [2013.05.05 12:27:24 | 000,000,000 | ---D | C] -- C:\Users\Jörg\AppData\Roaming\Malwarebytes [2013.05.05 12:25:59 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Malwarebytes' Anti-Malware [2013.05.05 12:25:59 | 000,000,000 | ---D | C] -- C:\ProgramData\Malwarebytes [2013.05.05 12:25:58 | 000,025,928 | ---- | C] (Malwarebytes Corporation) -- C:\windows\SysNative\drivers\mbam.sys [2013.05.05 12:25:58 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\Malwarebytes' Anti-Malware [2013.05.04 11:56:13 | 000,000,000 | ---D | C] -- C:\Kaspersky Rescue Disk 10.0 [2013.04.14 12:47:10 | 000,000,000 | ---D | C] -- C:\Users\Jörg\AppData\Roaming\Leadertech [2013.04.14 05:07:28 | 000,096,768 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\mshtmled.dll [2013.04.14 05:07:28 | 000,073,216 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\mshtmled.dll [2013.04.14 05:07:27 | 000,176,640 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\ieui.dll [2013.04.14 05:07:26 | 000,248,320 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\ieui.dll [2013.04.14 05:07:26 | 000,173,056 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\ieUnatt.exe [2013.04.14 05:07:26 | 000,142,848 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\ieUnatt.exe [2013.04.14 05:07:25 | 002,312,704 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\jscript9.dll [2013.04.14 05:07:25 | 001,494,528 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\inetcpl.cpl [2013.04.14 05:07:25 | 001,427,968 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\inetcpl.cpl [2013.04.14 05:07:25 | 000,729,088 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\msfeeds.dll [2013.04.14 05:07:25 | 000,237,056 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\url.dll [2013.04.14 05:07:25 | 000,231,936 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\url.dll [2013.04.14 05:07:21 | 000,816,640 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\jscript.dll [2013.04.14 05:07:21 | 000,717,824 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\jscript.dll [2013.04.14 05:07:21 | 000,599,040 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\vbscript.dll [2013.04.12 20:54:26 | 000,000,000 | ---D | C] -- C:\windows\Minidump [2013.04.11 21:50:05 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\Mozilla Firefox ========== Files - Modified Within 30 Days ========== [2013.05.11 13:34:27 | 000,067,584 | --S- | M] () -- C:\windows\bootstat.dat [2013.05.11 13:34:21 | 4226,138,112 | -HS- | M] () -- C:\hiberfil.sys [2013.05.11 13:32:59 | 000,000,035 | ---- | M] () -- C:\Users\Public\Documents\AtherosServiceConfig.ini [2013.05.09 02:40:00 | 000,000,884 | ---- | M] () -- C:\windows\tasks\Adobe Flash Player Updater.job [2013.05.08 23:14:39 | 001,614,036 | ---- | M] () -- C:\windows\SysNative\PerfStringBackup.INI [2013.05.08 23:14:39 | 000,699,216 | ---- | M] () -- C:\windows\SysNative\perfh007.dat [2013.05.08 23:14:39 | 000,653,158 | ---- | M] () -- C:\windows\SysNative\perfh009.dat [2013.05.08 23:14:39 | 000,148,982 | ---- | M] () -- C:\windows\SysNative\perfc007.dat [2013.05.08 23:14:39 | 000,121,832 | ---- | M] () -- C:\windows\SysNative\perfc009.dat [2013.05.08 17:21:36 | 000,020,720 | -H-- | M] () -- C:\windows\SysNative\7B296FB0-376B-497e-B012-9C450E1B7327-5P-1.C7483456-A289-439d-8115-601632D005A0 [2013.05.08 17:21:36 | 000,020,720 | -H-- | M] () -- C:\windows\SysNative\7B296FB0-376B-497e-B012-9C450E1B7327-5P-0.C7483456-A289-439d-8115-601632D005A0 [2013.05.05 20:14:13 | 004,745,728 | ---- | M] (AVAST Software) -- C:\Users\Jörg\Desktop\aswMBR.exe [2013.05.05 16:12:00 | 000,001,922 | ---- | M] () -- C:\Users\Public\Desktop\avast! Free Antivirus.lnk [2013.05.05 16:11:52 | 000,000,000 | ---- | M] () -- C:\windows\SysWow64\config.nt [2013.05.05 15:51:40 | 000,628,743 | ---- | M] () -- C:\Users\Jörg\Desktop\adwcleaner.exe [2013.05.05 15:28:46 | 000,000,328 | ---- | M] () -- C:\windows\tasks\HPCeeScheduleForJörg.job [2013.05.05 13:23:20 | 000,000,340 | ---- | M] () -- C:\windows\tasks\HPCeeScheduleFor*******$.job [2013.05.05 12:25:59 | 000,001,109 | ---- | M] () -- C:\Users\Public\Desktop\ Malwarebytes Anti-Malware .lnk [2013.05.02 17:44:28 | 000,189,936 | ---- | M] () -- C:\windows\SysNative\drivers\aswVmm.sys [2013.05.02 01:34:06 | 001,025,808 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswSnx.sys [2013.05.02 01:34:06 | 000,378,432 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswSP.sys [2013.05.02 01:34:06 | 000,072,016 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswRdr2.sys [2013.05.02 01:34:06 | 000,065,336 | ---- | M] () -- C:\windows\SysNative\drivers\aswRvrt.sys [2013.05.02 01:34:06 | 000,064,288 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswTdi.sys [2013.05.02 01:34:05 | 000,080,816 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswMonFlt.sys [2013.05.02 01:34:05 | 000,033,400 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswFsBlk.sys [2013.05.02 01:33:35 | 000,041,664 | ---- | M] (AVAST Software) -- C:\windows\avastSS.scr [2013.05.02 01:33:11 | 000,287,840 | ---- | M] (AVAST Software) -- C:\windows\SysNative\aswBoot.exe [2013.04.20 10:54:00 | 001,344,340 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013203.jpg [2013.04.20 09:24:50 | 001,477,102 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013202.jpg [2013.04.20 09:24:36 | 001,974,692 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013201.jpg [2013.04.20 08:47:34 | 001,398,559 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013200.jpg [2013.04.20 08:43:02 | 001,365,399 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013199.jpg [2013.04.20 08:36:10 | 001,566,010 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013198.jpg [2013.04.14 05:12:49 | 000,276,904 | ---- | M] () -- C:\windows\SysNative\FNTCACHE.DAT [2013.04.12 20:54:19 | 553,063,060 | ---- | M] () -- C:\windows\MEMORY.DMP ========== Files Created - No Company Name ========== [2013.05.06 19:25:06 | 000,628,743 | ---- | C] () -- C:\Users\Jörg\Desktop\adwcleaner.exe [2013.05.05 16:12:00 | 000,001,922 | ---- | C] () -- C:\Users\Public\Desktop\avast! Free Antivirus.lnk [2013.05.05 16:11:58 | 000,189,936 | ---- | C] () -- C:\windows\SysNative\drivers\aswVmm.sys [2013.05.05 16:11:57 | 000,065,336 | ---- | C] () -- C:\windows\SysNative\drivers\aswRvrt.sys [2013.05.05 16:11:48 | 000,000,000 | ---- | C] () -- C:\windows\SysWow64\config.nt [2013.05.05 12:25:59 | 000,001,109 | ---- | C] () -- C:\Users\Public\Desktop\ Malwarebytes Anti-Malware .lnk [2013.04.20 22:04:51 | 001,477,102 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013202.jpg [2013.04.20 22:04:50 | 001,974,692 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013201.jpg [2013.04.20 22:04:50 | 001,566,010 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013198.jpg [2013.04.20 22:04:50 | 001,398,559 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013200.jpg [2013.04.20 22:04:50 | 001,365,399 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013199.jpg [2013.04.20 22:04:50 | 001,344,340 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013203.jpg [2013.04.12 20:54:19 | 553,063,060 | ---- | C] () -- C:\windows\MEMORY.DMP [2012.03.24 20:53:59 | 000,008,192 | ---- | C] () -- C:\Users\Jörg\AppData\Local\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini [2011.10.13 11:47:06 | 000,003,120 | ---- | C] () -- C:\windows\SysWow64\drivers\wdfdbga.sys [2011.10.13 11:36:02 | 000,000,000 | ---- | C] () -- C:\windows\ativpsrm.bin [2011.10.13 11:33:16 | 000,003,914 | ---- | C] () -- C:\windows\SysWow64\atipblup.dat [2011.10.13 11:32:09 | 000,025,984 | ---- | C] () -- C:\windows\snuvcdsm.exe [2011.10.13 11:32:08 | 000,015,497 | ---- | C] () -- C:\windows\snp2uvc.ini [2011.08.23 11:10:44 | 000,000,256 | ---- | C] () -- C:\windows\SysWow64\vcsAPIShared.dll.hpsign [2011.05.30 22:58:34 | 000,185,168 | ---- | C] () -- C:\windows\SysWow64\PassThroughOTP.dll [2011.05.30 22:58:34 | 000,000,256 | ---- | C] () -- C:\windows\SysWow64\PassThroughOTP.dll.hpsign ========== ZeroAccess Check ========== [2009.07.14 06:55:00 | 000,000,227 | RHS- | M] () -- C:\windows\assembly\Desktop.ini [HKEY_CURRENT_USER\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] /64 [HKEY_CURRENT_USER\Software\Classes\Wow6432node\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] [HKEY_CURRENT_USER\Software\Classes\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InProcServer32] /64 [HKEY_CURRENT_USER\Software\Classes\Wow6432node\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InProcServer32] [HKEY_LOCAL_MACHINE\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] /64 "" = C:\Windows\SysNative\shell32.dll -- [2012.06.09 07:30:56 | 014,165,504 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Apartment [HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] "" = %SystemRoot%\system32\shell32.dll -- [2012.06.09 06:46:56 | 012,868,608 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Apartment [HKEY_LOCAL_MACHINE\Software\Classes\clsid\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InProcServer32] /64 "" = C:\Windows\SysNative\wbem\fastprox.dll -- [2009.07.14 03:40:51 | 000,909,312 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Free [HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InProcServer32] "" = %systemroot%\system32\wbem\fastprox.dll -- [2009.07.14 03:15:20 | 000,605,696 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Free [HKEY_LOCAL_MACHINE\Software\Classes\clsid\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InProcServer32] /64 "" = C:\Windows\SysNative\wbem\wbemess.dll -- [2009.07.14 03:41:56 | 000,505,856 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Both [HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InProcServer32] < End of report > |
| | #5 |
| /// Helfer-Team        | GVU Trojaner 2.12, Siredef, etc. eingefangen Downloade dir bitte
Starte keine andere Datei in diesem Ordner ohne Anweisung eines Helfers dann: Systemscan mit OTL (bebilderte Anleitung) Lade Dir bitte OTL von Oldtimer herunter und speichere es auf Deinem Desktop ( falls noch nicht vorhanden)- Doppelklick auf die OTL.exe
|
| | #6 |
| | GVU Trojaner 2.12, Siredef, etc. eingefangen Hi, hier die 3 Logfiles. MBAR: Code:
ATTFilter Malwarebytes Anti-Rootkit BETA 1.05.0.1001
www.malwarebytes.org
Database version: v2013.05.12.02
Windows 7 x64 NTFS (Safe Mode/Networking)
Internet Explorer 9.0.8112.16421
Jörg :: DUJOLAP [administrator]
12.05.2013 13:36:36
mbar-log-2013-05-12 (13-36-36).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM | P2P
Scan options disabled:
Objects scanned: 29737
Time elapsed: 8 minute(s), 52 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
OTL: OTL EXTRAS Logfile: Code:
ATTFilter OTL logfile created on: 12.05.2013 13:44:27 - Run 3 OTL by OldTimer - Version 3.2.69.0 Folder = C:\Users\Jörg\Desktop 64bit- Professional (Version = 6.1.7600) - Type = NTWorkstation Internet Explorer (Version = 9.0.8112.16421) Locale: 00000407 | Country: Deutschland | Language: DEU | Date Format: dd.MM.yyyy 3,94 Gb Total Physical Memory | 3,34 Gb Available Physical Memory | 84,90% Memory free 7,87 Gb Paging File | 7,32 Gb Available in Paging File | 93,01% Paging File free Paging file location(s): ?:\pagefile.sys [binary data] %SystemDrive% = C: | %SystemRoot% = C:\windows | %ProgramFiles% = C:\Program Files (x86) Drive C: | 275,00 Gb Total Space | 176,46 Gb Free Space | 64,17% Space Free | Partition Type: NTFS Drive D: | 1,96 Gb Total Space | 0,73 Gb Free Space | 37,18% Space Free | Partition Type: FAT32 Drive E: | 17,80 Gb Total Space | 2,70 Gb Free Space | 15,19% Space Free | Partition Type: NTFS Drive F: | 4,98 Gb Total Space | 2,13 Gb Free Space | 42,69% Space Free | Partition Type: FAT32 Computer Name: ****** | User Name: Jörg | Logged in as Administrator. Boot Mode: SafeMode with Networking | Scan Mode: All users | Include 64bit Scans Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days ========== Processes (SafeList) ========== PRC - C:\Users\Jörg\Desktop\OTL.exe (OldTimer Tools) ========== Modules (No Company Name) ========== ========== Services (SafeList) ========== SRV:64bit: - (avast! Antivirus) -- C:\Program Files\AVAST Software\Avast\AvastSvc.exe (AVAST Software) SRV:64bit: - (STacSV) -- C:\Program Files\IDT\WDM\STacSV64.exe (IDT, Inc.) SRV:64bit: - (AESTFilters) -- C:\Program Files\IDT\WDM\AESTSr64.exe (Andrea Electronics Corporation) SRV:64bit: - (vcsFPService) -- C:\Windows\SysNative\vcsFPService.exe (Validity Sensors, Inc.) SRV:64bit: - (McAfee Endpoint Encryption Agent) -- C:\Program Files\Hewlett-Packard\Drive Encryption\EEAgent\MfeEpeHost.exe () SRV:64bit: - (AMD External Events Utility) -- C:\Windows\SysNative\atiesrxx.exe (AMD) SRV:64bit: - (DpHost) -- c:\Program Files\Hewlett-Packard\HP ProtectTools Security Manager\Bin\DpHostW.exe (DigitalPersona, Inc.) SRV:64bit: - (HPDayStarterService) -- c:\Program Files\Hewlett-Packard\HP DayStarter\32-bit\HPDayStarterService.exe (Hewlett-Packard Company) SRV:64bit: - (HP Power Assistant Service) -- C:\Program Files\Hewlett-Packard\HP Power Assistant\HPPA_Service.exe (Hewlett-Packard Company) SRV:64bit: - (hpsrv) -- C:\Windows\SysNative\hpservice.exe (Hewlett-Packard Company) SRV:64bit: - (WinDefend) -- C:\Program Files\Windows Defender\mpsvc.dll (Microsoft Corporation) SRV:64bit: - (AppMgmt) -- C:\Windows\SysNative\appmgmts.dll (Microsoft Corporation) SRV - (MozillaMaintenance) -- C:\Program Files (x86)\Mozilla Maintenance Service\maintenanceservice.exe (Mozilla Foundation) SRV - (AdobeFlashPlayerUpdateSvc) -- C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe (Adobe Systems Incorporated) SRV - (HP Support Assistant Service) -- C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\hpsa_service.exe (Hewlett-Packard Company) SRV - (HPDrvMntSvc.exe) -- C:\Program Files (x86)\Hewlett-Packard\Shared\HPDrvMntSvc.exe (Hewlett-Packard Company) SRV - (SkypeUpdate) -- C:\Program Files (x86)\Skype\Updater\Updater.exe (Skype Technologies) SRV - (BBUpdate) -- C:\Program Files (x86)\Microsoft\BingBar\7.1.361.0\SeaPort.exe (Microsoft Corporation.) SRV - (BBSvc) -- C:\Program Files (x86)\Microsoft\BingBar\7.1.361.0\BBSvc.exe (Microsoft Corporation.) SRV - (sftvsa) -- C:\Program Files (x86)\Microsoft Application Virtualization Client\sftvsa.exe (Microsoft Corporation) SRV - (sftlist) -- C:\Program Files (x86)\Microsoft Application Virtualization Client\sftlist.exe (Microsoft Corporation) SRV - (vcsFPService) -- C:\Windows\SysWOW64\vcsFPService.exe (Validity Sensors, Inc.) SRV - (hpCMSrv) -- c:\Program Files (x86)\Hewlett-Packard\HP Connection Manager\hpCMSrv.exe (Hewlett-Packard Development Company L.P.) SRV - (XobniService) -- C:\Program Files (x86)\Xobni\XobniService.exe (Xobni Corporation) SRV - (HPFSService) -- C:\Program Files (x86)\Hewlett-Packard\File Sanitizer\HPFSService.exe (Hewlett-Packard) SRV - (FLCDLOCK) -- c:\Windows\SysWOW64\flcdlock.exe (Hewlett-Packard Company) SRV - (pdfcDispatcher) -- C:\Program Files (x86)\PDF Complete\pdfsvc.exe (PDF Complete Inc) SRV - (IAStorDataMgrSvc) -- C:\Program Files (x86)\Intel\Intel(R) Rapid Storage Technology\IAStorDataMgrSvc.exe (Intel Corporation) SRV - (PdiService) -- C:\Program Files (x86)\Common Files\Portrait Displays\Drivers\pdisrvc.exe (Portrait Displays, Inc.) SRV - (UNS) -- C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\UNS\UNS.exe (Intel Corporation) SRV - (LMS) -- C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\LMS\LMS.exe (Intel Corporation) SRV - (HP ProtectTools Service) -- c:\Program Files (x86)\Hewlett-Packard\2009 Password Filter for HP ProtectTools\PTChangeFilterService.exe (Hewlett-Packard Development Company, L.P) SRV - (Atheros Bt&Wlan Coex Agent) -- C:\Program Files (x86)\Bluetooth Suite\Ath_CoexAgent.exe (Atheros) SRV - (AtherosSvc) -- C:\Program Files (x86)\Bluetooth Suite\adminservice.exe (Atheros Commnucations) SRV - (jhi_service) -- C:\Program Files (x86)\Intel\Services\IPT\jhi_service.exe (Intel Corporation) SRV - (uArcCapture) -- C:\Windows\SysWOW64\ArcVCapRender\uArcCapture.exe (ArcSoft, Inc.) SRV - (GameConsoleService) -- C:\Program Files (x86)\HP Games\HP Game Console\GameConsoleService.exe (WildTangent, Inc.) SRV - (clr_optimization_v4.0.30319_32) -- C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe (Microsoft Corporation) SRV - (ACDaemon) -- C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACService.exe (ArcSoft Inc.) SRV - (clr_optimization_v2.0.50727_32) -- C:\Windows\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe (Microsoft Corporation) ========== Driver Services (SafeList) ========== DRV:64bit: - (aswVmm) -- C:\windows\SysNative\drivers\aswVmm.sys () DRV:64bit: - (aswSnx) -- C:\windows\SysNative\drivers\aswSnx.sys (AVAST Software) DRV:64bit: - (aswSP) -- C:\windows\SysNative\drivers\aswSP.sys (AVAST Software) DRV:64bit: - (aswRdr) -- C:\Windows\SysNative\drivers\aswRdr2.sys (AVAST Software) DRV:64bit: - (aswRvrt) -- C:\windows\SysNative\drivers\aswRvrt.sys () DRV:64bit: - (aswTdi) -- C:\windows\SysNative\drivers\aswTdi.sys (AVAST Software) DRV:64bit: - (aswMonFlt) -- C:\Windows\SysNative\drivers\aswMonFlt.sys (AVAST Software) DRV:64bit: - (aswFsBlk) -- C:\windows\SysNative\drivers\aswFsBlk.sys (AVAST Software) DRV:64bit: - (Fs_Rec) -- C:\windows\SysNative\drivers\fs_rec.sys (Microsoft Corporation) DRV:64bit: - (STHDA) -- C:\Windows\SysNative\drivers\stwrt64.sys (IDT, Inc.) DRV:64bit: - (Sftvol) -- C:\Windows\SysNative\drivers\Sftvollh.sys (Microsoft Corporation) DRV:64bit: - (Sftplay) -- C:\Windows\SysNative\drivers\Sftplaylh.sys (Microsoft Corporation) DRV:64bit: - (Sftredir) -- C:\Windows\SysNative\drivers\Sftredirlh.sys (Microsoft Corporation) DRV:64bit: - (Sftfs) -- C:\Windows\SysNative\drivers\Sftfslh.sys (Microsoft Corporation) DRV:64bit: - (MfeEpePc) -- C:\windows\SysNative\drivers\MfeEpePc.sys (McAfee, Inc.) DRV:64bit: - (amdkmdag) -- C:\Windows\SysNative\drivers\atikmdag.sys (ATI Technologies Inc.) DRV:64bit: - (amdkmdap) -- C:\Windows\SysNative\drivers\atikmpag.sys (Advanced Micro Devices, Inc.) DRV:64bit: - (amdsata) -- C:\Windows\SysNative\drivers\amdsata.sys (Advanced Micro Devices) DRV:64bit: - (amdxata) -- C:\Windows\SysNative\drivers\amdxata.sys (Advanced Micro Devices) DRV:64bit: - (DAMDrv) -- C:\Windows\SysNative\drivers\DAMDrv64.sys (Hewlett-Packard Company) DRV:64bit: - (SynTP) -- C:\Windows\SysNative\drivers\SynTP.sys (Synaptics Incorporated) DRV:64bit: - (JMCR) -- C:\Windows\SysNative\drivers\jmcr.sys (JMicron Technology Corporation) DRV:64bit: - (intelkmd) -- C:\Windows\SysNative\drivers\igdpmd64.sys (Intel Corporation) DRV:64bit: - (Accelerometer) -- C:\Windows\SysNative\drivers\Accelerometer.sys (Hewlett-Packard Company) DRV:64bit: - (hpdskflt) -- C:\Windows\SysNative\drivers\hpdskflt.sys (Hewlett-Packard Company) DRV:64bit: - (iaStor) -- C:\Windows\SysNative\drivers\iaStor.sys (Intel Corporation) DRV:64bit: - (athr) -- C:\Windows\SysNative\drivers\athrx.sys (Atheros Communications, Inc.) DRV:64bit: - (BtFilter) -- C:\Windows\SysNative\drivers\btfilter.sys (Atheros) DRV:64bit: - (BTATH_HCRP) -- C:\Windows\SysNative\drivers\btath_hcrp.sys (Atheros) DRV:64bit: - (BTATH_RCP) -- C:\Windows\SysNative\drivers\btath_rcp.sys (Atheros) DRV:64bit: - (BTATH_LWFLT) -- C:\Windows\SysNative\drivers\btath_lwflt.sys (Atheros) DRV:64bit: - (AthBTPort) -- C:\Windows\SysNative\drivers\btath_flt.sys (Atheros) DRV:64bit: - (BTATH_A2DP) -- C:\Windows\SysNative\drivers\btath_a2dp.sys (Atheros) DRV:64bit: - (BTATH_BUS) -- C:\Windows\SysNative\drivers\btath_bus.sys (Atheros) DRV:64bit: - (SNP2UVC) -- C:\Windows\SysNative\drivers\snp2uvc.sys () DRV:64bit: - (nusb3xhc) -- C:\Windows\SysNative\drivers\nusb3xhc.sys (Renesas Electronics Corporation) DRV:64bit: - (nusb3hub) -- C:\Windows\SysNative\drivers\nusb3hub.sys (Renesas Electronics Corporation) DRV:64bit: - (HpqKbFiltr) -- C:\Windows\SysNative\drivers\HpqKbFiltr.sys (Hewlett-Packard Company) DRV:64bit: - (RTL8167) -- C:\Windows\SysNative\drivers\Rt64win7.sys (Realtek ) DRV:64bit: - (ARCVCAM) -- C:\Windows\SysNative\drivers\ArcSoftVCapture.sys (ArcSoft, Inc.) DRV:64bit: - (sdbus) -- C:\Windows\SysNative\drivers\sdbus.sys (Microsoft Corporation) DRV:64bit: - (MEIx64) -- C:\Windows\SysNative\drivers\HECIx64.sys (Intel Corporation) DRV:64bit: - (IntcDAud) -- C:\Windows\SysNative\drivers\IntcDAud.sys (Intel(R) Corporation) DRV:64bit: - (vpcvmm) -- C:\Windows\SysNative\drivers\vpcvmm.sys (Microsoft Corporation) DRV:64bit: - (vpcnfltr) -- C:\Windows\SysNative\drivers\vpcnfltr.sys (Microsoft Corporation) DRV:64bit: - (vpcusb) -- C:\Windows\SysNative\drivers\vpcusb.sys (Microsoft Corporation) DRV:64bit: - (vpcbus) -- C:\Windows\SysNative\drivers\vpchbus.sys (Microsoft Corporation) DRV:64bit: - (amdsbs) -- C:\Windows\SysNative\drivers\amdsbs.sys (AMD Technologies Inc.) DRV:64bit: - (LSI_SAS2) -- C:\Windows\SysNative\drivers\lsi_sas2.sys (LSI Corporation) DRV:64bit: - (HpSAMD) -- C:\Windows\SysNative\drivers\HpSAMD.sys (Hewlett-Packard Company) DRV:64bit: - (stexstor) -- C:\Windows\SysNative\drivers\stexstor.sys (Promise Technology) DRV:64bit: - (TPM) -- C:\Windows\SysNative\drivers\tpm.sys (Microsoft Corporation) DRV:64bit: - (AgereSoftModem) -- C:\Windows\SysNative\drivers\agrsm64.sys (LSI Corp) DRV:64bit: - (ebdrv) -- C:\Windows\SysNative\drivers\evbda.sys (Broadcom Corporation) DRV:64bit: - (b06bdrv) -- C:\Windows\SysNative\drivers\bxvbda.sys (Broadcom Corporation) DRV:64bit: - (b57nd60a) -- C:\Windows\SysNative\drivers\b57nd60a.sys (Broadcom Corporation) DRV:64bit: - (hcw85cir) -- C:\Windows\SysNative\drivers\hcw85cir.sys (Hauppauge Computer Works, Inc.) DRV - (WIMMount) -- C:\Windows\SysWOW64\drivers\wimmount.sys (Microsoft Corporation) ========== Standard Registry (SafeList) ========== ========== Internet Explorer ========== IE:64bit: - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = hxxp://g.uk.msn.com/HPCOM/10 IE:64bit: - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = hxxp://g.uk.msn.com/HPCOM/10 IE:64bit: - HKLM\..\SearchScopes,DefaultScope = IE:64bit: - HKLM\..\SearchScopes\{b7fca997-d0fb-4fe0-8afd-255e89cf9671}: "URL" = hxxp://de.search.yahoo.com/search?p={searchTerms}&ei={inputEncoding}&fr=chr-hp-psg&type=CMNTDF IE:64bit: - HKLM\..\SearchScopes\{ec29edf6-ad3c-4e1c-a087-d6cb81400c43}: "URL" = hxxp://www.bing.com/search?q={searchTerms}&form=CMNTDF&pc=CMNTDF&src=IE-SearchBox IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = hxxp://g.uk.msn.com/HPCOM/10 IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Local Page = C:\Windows\SysWOW64\blank.htm IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = hxxp://g.uk.msn.com/HPCOM/10 IE - HKLM\..\SearchScopes,DefaultScope = IE - HKLM\..\SearchScopes\{b7fca997-d0fb-4fe0-8afd-255e89cf9671}: "URL" = hxxp://de.search.yahoo.com/search?p={searchTerms}&ei={inputEncoding}&fr=chr-hp-psg&type=CMNTDF IE - HKLM\..\SearchScopes\{ec29edf6-ad3c-4e1c-a087-d6cb81400c43}: "URL" = hxxp://www.bing.com/search?q={searchTerms}&form=CMNTDF&pc=CMNTDF&src=IE-SearchBox IE - HKU\.DEFAULT\..\SearchScopes,DefaultScope = IE - HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0 IE - HKU\S-1-5-18\..\SearchScopes,DefaultScope = IE - HKU\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0 IE - HKU\S-1-5-19\..\SearchScopes,DefaultScope = IE - HKU\S-1-5-20\..\SearchScopes,DefaultScope = IE - HKU\S-1-5-21-2069978452-285043259-3883334984-1002\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = hxxp://g.uk.msn.com/HPCOM/10 IE - HKU\S-1-5-21-2069978452-285043259-3883334984-1002\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = about:blank IE - HKU\S-1-5-21-2069978452-285043259-3883334984-1002\..\SearchScopes,DefaultScope = IE - HKU\S-1-5-21-2069978452-285043259-3883334984-1002\..\SearchScopes\{b7fca997-d0fb-4fe0-8afd-255e89cf9671}: "URL" = hxxp://de.search.yahoo.com/search?p={searchTerms}&ei={inputEncoding}&fr=chr-hp-psg&type=CMNTDF IE - HKU\S-1-5-21-2069978452-285043259-3883334984-1002\..\SearchScopes\{C15A3503-647F-44E8-9F2B-B0A2411888B2}: "URL" = hxxp://www.google.de/search?q={searchTerms} IE - HKU\S-1-5-21-2069978452-285043259-3883334984-1002\..\SearchScopes\{ec29edf6-ad3c-4e1c-a087-d6cb81400c43}: "URL" = hxxp://www.bing.com/search?q={searchTerms}&form=CMNTDF&pc=CMNTDF&src=IE-SearchBox IE - HKU\S-1-5-21-2069978452-285043259-3883334984-1002\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0 ========== FireFox ========== FF - prefs.js..browser.search.suggest.enabled: false FF - prefs.js..extensions.enabledAddons: %7Bb9db16a4-6edc-47ec-a1f4-b86292ed211d%7D:4.9.14 FF - prefs.js..extensions.enabledAddons: wrc%40avast.com:8.0.1488 FF - prefs.js..extensions.enabledAddons: %7B972ce4c6-7e08-4474-a285-3208198ce6fd%7D:20.0.1 FF - user.js - File not found FF:64bit: - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\windows\system32\Macromed\Flash\NPSWF64_11_6_602_180.dll File not found FF:64bit: - HKLM\Software\MozillaPlugins\@java.com/DTPlugin,version=10.17.2: C:\windows\system32\npDeployJava1.dll (Oracle Corporation) FF:64bit: - HKLM\Software\MozillaPlugins\@java.com/JavaPlugin,version=10.17.2: C:\Program Files\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation) FF:64bit: - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files\Microsoft Silverlight\5.1.20125.0\npctrl.dll ( Microsoft Corporation) FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\windows\SysWOW64\Macromed\Flash\NPSWF32_11_6_602_180.dll () FF - HKLM\Software\MozillaPlugins\@java.com/DTPlugin,version=10.17.2: C:\windows\SysWOW64\npDeployJava1.dll (Oracle Corporation) FF - HKLM\Software\MozillaPlugins\@java.com/JavaPlugin,version=10.17.2: C:\Program Files (x86)\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation) FF - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files (x86)\Microsoft Silverlight\5.1.20125.0\npctrl.dll ( Microsoft Corporation) FF - HKLM\Software\MozillaPlugins\@microsoft.com/SharePoint,version=14.0: C:\PROGRA~2\MICROS~1\Office14\NPSPWRAP.DLL (Microsoft Corporation) FF - HKLM\Software\MozillaPlugins\@microsoft.com/WLPG,version=15.4.3502.0922: C:\Program Files (x86)\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation) FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\otis@digitalpersona.com: c:\Program Files (x86)\Hewlett-Packard\HP ProtectTools Security Manager\Bin\FirefoxExt\ [2011.05.03 20:19:26 | 000,000,000 | ---D | M] FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\wrc@avast.com: C:\Program Files\AVAST Software\Avast\WebRep\FF [2013.05.05 16:11:25 | 000,000,000 | ---D | M] FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 20.0.1\extensions\\Components: C:\Program Files (x86)\Mozilla Firefox\components [2013.04.11 21:50:08 | 000,000,000 | ---D | M] FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 20.0.1\extensions\\Plugins: C:\Program Files (x86)\Mozilla Firefox\plugins [2012.02.20 22:15:32 | 000,000,000 | ---D | M] (No name found) -- C:\Users\Jörg\AppData\Roaming\mozilla\Extensions [2013.02.23 11:28:10 | 000,000,000 | ---D | M] (No name found) -- C:\Users\Jörg\AppData\Roaming\mozilla\Firefox\Profiles\lrimm10i.default\extensions [2013.02.23 11:28:10 | 000,000,000 | ---D | M] (DownloadHelper) -- C:\Users\Jörg\AppData\Roaming\mozilla\Firefox\Profiles\lrimm10i.default\extensions\{b9db16a4-6edc-47ec-a1f4-b86292ed211d} [2013.02.14 08:16:33 | 000,817,280 | ---- | M] () (No name found) -- C:\Users\Jörg\AppData\Roaming\mozilla\firefox\profiles\lrimm10i.default\extensions\{d10d0bf8-f5b5-c8b4-a8b2-2b9879e08c5d}.xpi [2013.04.11 21:50:05 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files (x86)\mozilla firefox\extensions [2013.05.05 16:11:25 | 000,000,000 | ---D | M] (avast! Online Security) -- C:\PROGRAM FILES\AVAST SOFTWARE\AVAST\WEBREP\FF File not found (No name found) -- C:\USERS\JöRG\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\LRIMM10I.DEFAULT\EXTENSIONS\{B9DB16A4-6EDC-47EC-A1F4-B86292ED211D} [2013.04.11 21:50:08 | 000,263,064 | ---- | M] (Mozilla Foundation) -- C:\Program Files (x86)\mozilla firefox\components\browsercomps.dll [2012.02.16 13:02:53 | 000,001,392 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\amazondotcom-de.xml [2012.09.23 17:35:42 | 000,002,465 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\bing.xml [2012.02.16 13:02:53 | 000,001,153 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\eBay-de.xml [2012.02.16 13:02:53 | 000,006,805 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\leo_ende_de.xml [2012.02.16 13:02:53 | 000,001,178 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\wikipedia-de.xml [2012.02.16 13:02:53 | 000,001,105 | ---- | M] () -- C:\Program Files (x86)\mozilla firefox\searchplugins\yahoo-de.xml O1 HOSTS File: ([2009.06.10 23:00:26 | 000,000,824 | ---- | M]) - C:\Windows\SysNative\drivers\etc\hosts O2:64bit: - BHO: (avast! Online Security) - {318A227B-5E9F-45bd-8999-7F8F10CA4CF5} - C:\Program Files\AVAST Software\Avast\aswWebRepIE64.dll (AVAST Software) O2:64bit: - BHO: (Java(tm) Plug-In SSV Helper) - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files\Java\jre7\bin\ssv.dll (Oracle Corporation) O2:64bit: - BHO: (Java(tm) Plug-In 2 SSV Helper) - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre7\bin\jp2ssv.dll (Oracle Corporation) O2 - BHO: (File Sanitizer for HP ProtectTools) - {3134413B-49B4-425C-98A5-893C1F195601} - C:\Program Files (x86)\Hewlett-Packard\File Sanitizer\IEBHO.dll (Hewlett-Packard) O2 - BHO: (Java(tm) Plug-In SSV Helper) - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files (x86)\Java\jre7\bin\ssv.dll (Oracle Corporation) O2 - BHO: (CIESpeechBHO Class) - {8D10F6C4-0E01-4BD4-8601-11AC1FDF8126} - C:\Program Files (x86)\Bluetooth Suite\IEPlugIn.dll (Atheros Commnucations) O2 - BHO: (avast! Online Security) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\AVAST Software\Avast\aswWebRepIE.dll (AVAST Software) O2 - BHO: (Bing Bar Helper) - {d2ce3e00-f94a-4740-988e-03dc2f38c34f} - C:\Program Files (x86)\Microsoft\BingBar\7.1.361.0\BingExt.dll (Microsoft Corporation.) O2 - BHO: (Java(tm) Plug-In 2 SSV Helper) - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files (x86)\Java\jre7\bin\jp2ssv.dll (Oracle Corporation) O2 - BHO: (HP Network Check Helper) - {E76FD755-C1BA-4DCB-9F13-99BD91223ADE} - C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\HPNetworkCheckPlugin.dll (Hewlett-Packard) O3:64bit: - HKLM\..\Toolbar: (avast! Online Security) - {318A227B-5E9F-45bd-8999-7F8F10CA4CF5} - C:\Program Files\AVAST Software\Avast\aswWebRepIE64.dll (AVAST Software) O3 - HKLM\..\Toolbar: (Bing Bar) - {8dcb7100-df86-4384-8842-8fa844297b3f} - C:\Program Files (x86)\Microsoft\BingBar\7.1.361.0\BingExt.dll (Microsoft Corporation.) O3 - HKLM\..\Toolbar: (avast! Online Security) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\AVAST Software\Avast\aswWebRepIE.dll (AVAST Software) O3 - HKU\S-1-5-21-2069978452-285043259-3883334984-1002\..\Toolbar\WebBrowser: (no name) - {7FEBEFE3-6B19-4349-98D2-FFB09D4B49CA} - No CLSID value found. O4:64bit: - HKLM..\Run: [AthBtTray] C:\Program Files (x86)\Bluetooth Suite\AthBtTray.exe (Atheros Commnucations) O4:64bit: - HKLM..\Run: [AtherosBtStack] C:\Program Files (x86)\Bluetooth Suite\BtvStack.exe (Atheros Communications) O4:64bit: - HKLM..\Run: [HotKeysCmds] C:\Windows\SysNative\hkcmd.exe (Intel Corporation) O4:64bit: - HKLM..\Run: [HPPowerAssistant] C:\Program Files\Hewlett-Packard\HP Power Assistant\DelayedAppStarter.exe () O4:64bit: - HKLM..\Run: [IgfxTray] C:\Windows\SysNative\igfxtray.exe (Intel Corporation) O4:64bit: - HKLM..\Run: [MfeEpePcMonitor] C:\Program Files\Hewlett-Packard\Drive Encryption\EpePcMonitor.exe () O4:64bit: - HKLM..\Run: [Persistence] C:\Windows\SysNative\igfxpers.exe (Intel Corporation) O4:64bit: - HKLM..\Run: [SysTrayApp] C:\Program Files\IDT\WDM\sttray64.exe (IDT, Inc.) O4 - HKLM..\Run: [] File not found O4 - HKLM..\Run: [avast] C:\Program Files\AVAST Software\Avast\avastUI.exe (AVAST Software) O4 - HKLM..\Run: [DTRun] c:\Program Files (x86)\ArcSoft\TotalMedia Suite\TotalMedia Theatre 3\uDTRun.exe (ArcSoft Inc.) O4 - HKLM..\Run: [File Sanitizer] C:\Program Files (x86)\Hewlett-Packard\File Sanitizer\CoreShredder.exe (Hewlett-Packard) O4 - HKLM..\Run: [HPConnectionManager] c:\Program Files (x86)\Hewlett-Packard\HP Connection Manager\HPCMDelayStart.exe (Hewlett-Packard Development Company L.P.) O4 - HKLM..\Run: [HPQuickWebProxy] c:\Program Files (x86)\Hewlett-Packard\HP QuickWeb\hpqwutils.exe (Hewlett-Packard Company) O4 - HKLM..\Run: [IAStorIcon] C:\Program Files (x86)\Intel\Intel(R) Rapid Storage Technology\IAStorIcon.exe (Intel Corporation) O4 - HKLM..\Run: [NUSB3MON] c:\Program Files (x86)\Renesas Electronics\USB 3.0 Host Controller Driver\Application\nusb3mon.exe (Renesas Electronics Corporation) O4 - HKLM..\Run: [PDF Complete] C:\Program Files (x86)\PDF Complete\pdfsty.exe (PDF Complete Inc) O4 - HKLM..\Run: [StartCCC] C:\Program Files (x86)\ATI Technologies\ATI.ACE\Core-Static\CLIStart.exe (Advanced Micro Devices, Inc.) O4 - HKU\S-1-5-19..\Run: [Sidebar] C:\Program Files (x86)\Windows Sidebar\Sidebar.exe (Microsoft Corporation) O4 - HKU\S-1-5-20..\Run: [Sidebar] C:\Program Files (x86)\Windows Sidebar\Sidebar.exe (Microsoft Corporation) O4 - HKLM..\RunOnce: [Z1] C:\windows\SysWow64\cmd.exe (Microsoft Corporation) O4 - HKU\S-1-5-19..\RunOnce: [mctadmin] C:\Windows\System32\mctadmin.exe File not found O4 - HKU\S-1-5-20..\RunOnce: [mctadmin] C:\Windows\System32\mctadmin.exe File not found O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoActiveDesktop = 1 O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoActiveDesktopChanges = 1 O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: ConsentPromptBehaviorAdmin = 5 O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: ConsentPromptBehaviorUser = 3 O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System: PromptOnSecureDesktop = 0 O9:64bit: - Extra 'Tools' menuitem : Send by Bluetooth to - {7815BE26-237D-41A8-A98F-F7BD75F71086} - Reg Error: Value error. File not found O9 - Extra Button: @C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\HPNetworkCheckPlugin.dll,-103 - {25510184-5A38-4A99-B273-DCA8EEF6CD08} - C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\NCLauncherFromIE.exe (Hewlett-Packard) O9 - Extra 'Tools' menuitem : @C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\HPNetworkCheckPlugin.dll,-102 - {25510184-5A38-4A99-B273-DCA8EEF6CD08} - C:\Program Files (x86)\Hewlett-Packard\HP Support Framework\Resources\HPNetworkCheck\NCLauncherFromIE.exe (Hewlett-Packard) O9 - Extra 'Tools' menuitem : Send by Bluetooth to - {7815BE26-237D-41A8-A98F-F7BD75F71086} - C:\Program Files (x86)\Bluetooth Suite\IEPlugIn.dll (Atheros Commnucations) O9 - Extra Button: @C:\Program Files (x86)\Evernote\Evernote\Resource.dll,-101 - {A95fe080-8f5d-11d2-a20b-00aa003c157a} - C:\Program Files (x86)\Evernote\Evernote\EvernoteIE.dll (Evernote Corp., 333 W Evelyn Ave. Mountain View, CA 94041) O9 - Extra 'Tools' menuitem : @C:\Program Files (x86)\Evernote\Evernote\Resource.dll,-101 - {A95fe080-8f5d-11d2-a20b-00aa003c157a} - C:\Program Files (x86)\Evernote\Evernote\EvernoteIE.dll (Evernote Corp., 333 W Evelyn Ave. Mountain View, CA 94041) O1364bit: - gopher Prefix: missing O13 - gopher Prefix: missing O16:64bit: - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} hxxp://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab (Shockwave Flash Object) O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 192.168.178.1 O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{20504772-5A65-488E-91A3-5D88D3BF1977}: DhcpNameServer = 192.168.178.1 O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{C7037444-9766-4FB0-9449-44E2692E1603}: DhcpNameServer = 192.168.178.1 O18:64bit: - Protocol\Handler\skype4com - No CLSID value found O18:64bit: - Protocol\Handler\wlpg - No CLSID value found O18 - Protocol\Handler\skype4com {FFC8B962-9B40-4DFF-9458-1830C7DD7F5D} - C:\PROGRA~2\COMMON~1\Skype\SKYPE4~1.DLL (Skype Technologies) O20:64bit: - HKLM Winlogon: Shell - (explorer.exe) - C:\windows\explorer.exe (Microsoft Corporation) O20:64bit: - HKLM Winlogon: UserInit - (C:\windows\system32\userinit.exe) - C:\Windows\SysNative\userinit.exe (Microsoft Corporation) O20 - HKLM Winlogon: Shell - (explorer.exe) - C:\windows\SysWow64\explorer.exe (Microsoft Corporation) O20 - HKLM Winlogon: UserInit - (userinit.exe) - C:\windows\SysWow64\userinit.exe (Microsoft Corporation) O20:64bit: - Winlogon\Notify\igfxcui: DllName - (igfxdev.dll) - C:\windows\SysNative\igfxdev.dll (Intel Corporation) O20 - Winlogon\Notify\DeviceNP: DllName - (DeviceNP.dll) - C:\windows\SysWow64\DeviceNP.dll (Hewlett-Packard Company) O21:64bit: - SSODL: WebCheck - {E6FB5E20-DE35-11CF-9C87-00AA005127ED} - No CLSID value found. O21 - SSODL: WebCheck - {E6FB5E20-DE35-11CF-9C87-00AA005127ED} - No CLSID value found. O32 - HKLM CDRom: AutoRun - 1 O34 - HKLM BootExecute: (autocheck autochk *) O35:64bit: - HKLM\..comfile [open] -- "%1" %* O35:64bit: - HKLM\..exefile [open] -- "%1" %* O35 - HKLM\..comfile [open] -- "%1" %* O35 - HKLM\..exefile [open] -- "%1" %* O37:64bit: - HKLM\...com [@ = comfile] -- "%1" %* O37:64bit: - HKLM\...exe [@ = exefile] -- "%1" %* O37 - HKLM\...com [@ = comfile] -- "%1" %* O37 - HKLM\...exe [@ = exefile] -- "%1" %* O38 - SubSystems\\Windows: (ServerDll=winsrv:UserServerDllInitialization,3) O38 - SubSystems\\Windows: (ServerDll=winsrv:ConServerDllInitialization,2) O38 - SubSystems\\Windows: (ServerDll=sxssrv,4) ========== Files/Folders - Created Within 30 Days ========== [2013.05.12 13:42:02 | 000,602,112 | ---- | C] (OldTimer Tools) -- C:\Users\Jörg\Desktop\OTL.exe [2013.05.12 13:23:45 | 000,000,000 | ---D | C] -- C:\Users\Jörg\Desktop\mbar [2013.05.08 23:09:24 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\ESET [2013.05.07 21:55:12 | 000,000,000 | -HSD | C] -- C:\found.000 [2013.05.05 20:12:44 | 004,745,728 | ---- | C] (AVAST Software) -- C:\Users\Jörg\Desktop\aswMBR.exe [2013.05.05 16:12:00 | 000,378,432 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswSP.sys [2013.05.05 16:12:00 | 000,033,400 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswFsBlk.sys [2013.05.05 16:12:00 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\avast! Free Antivirus [2013.05.05 16:11:59 | 000,072,016 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswRdr2.sys [2013.05.05 16:11:58 | 001,025,808 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswSnx.sys [2013.05.05 16:11:58 | 000,064,288 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswTdi.sys [2013.05.05 16:11:52 | 000,080,816 | ---- | C] (AVAST Software) -- C:\windows\SysNative\drivers\aswMonFlt.sys [2013.05.05 16:11:48 | 000,287,840 | ---- | C] (AVAST Software) -- C:\windows\SysNative\aswBoot.exe [2013.05.05 16:11:12 | 000,041,664 | ---- | C] (AVAST Software) -- C:\windows\avastSS.scr [2013.05.05 16:10:57 | 000,000,000 | ---D | C] -- C:\Program Files\AVAST Software [2013.05.05 16:08:52 | 000,000,000 | ---D | C] -- C:\ProgramData\AVAST Software [2013.05.05 12:27:24 | 000,000,000 | ---D | C] -- C:\Users\Jörg\AppData\Roaming\Malwarebytes [2013.05.05 12:25:59 | 000,000,000 | ---D | C] -- C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Malwarebytes' Anti-Malware [2013.05.05 12:25:59 | 000,000,000 | ---D | C] -- C:\ProgramData\Malwarebytes [2013.05.05 12:25:58 | 000,025,928 | ---- | C] (Malwarebytes Corporation) -- C:\windows\SysNative\drivers\mbam.sys [2013.05.05 12:25:58 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\Malwarebytes' Anti-Malware [2013.05.04 11:56:13 | 000,000,000 | ---D | C] -- C:\Kaspersky Rescue Disk 10.0 [2013.04.14 12:47:10 | 000,000,000 | ---D | C] -- C:\Users\Jörg\AppData\Roaming\Leadertech [2013.04.14 05:07:28 | 000,096,768 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\mshtmled.dll [2013.04.14 05:07:28 | 000,073,216 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\mshtmled.dll [2013.04.14 05:07:27 | 000,176,640 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\ieui.dll [2013.04.14 05:07:26 | 000,248,320 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\ieui.dll [2013.04.14 05:07:26 | 000,173,056 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\ieUnatt.exe [2013.04.14 05:07:26 | 000,142,848 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\ieUnatt.exe [2013.04.14 05:07:25 | 002,312,704 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\jscript9.dll [2013.04.14 05:07:25 | 001,494,528 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\inetcpl.cpl [2013.04.14 05:07:25 | 001,427,968 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\inetcpl.cpl [2013.04.14 05:07:25 | 000,729,088 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\msfeeds.dll [2013.04.14 05:07:25 | 000,237,056 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\url.dll [2013.04.14 05:07:25 | 000,231,936 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\url.dll [2013.04.14 05:07:21 | 000,816,640 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\jscript.dll [2013.04.14 05:07:21 | 000,717,824 | ---- | C] (Microsoft Corporation) -- C:\windows\SysWow64\jscript.dll [2013.04.14 05:07:21 | 000,599,040 | ---- | C] (Microsoft Corporation) -- C:\windows\SysNative\vbscript.dll [2013.04.12 20:54:26 | 000,000,000 | ---D | C] -- C:\windows\Minidump ========== Files - Modified Within 30 Days ========== [2013.05.12 13:26:25 | 000,067,584 | --S- | M] () -- C:\windows\bootstat.dat [2013.05.12 13:26:19 | 4226,138,112 | -HS- | M] () -- C:\hiberfil.sys [2013.05.11 13:32:59 | 000,000,035 | ---- | M] () -- C:\Users\Public\Documents\AtherosServiceConfig.ini [2013.05.09 02:40:00 | 000,000,884 | ---- | M] () -- C:\windows\tasks\Adobe Flash Player Updater.job [2013.05.08 23:14:39 | 001,614,036 | ---- | M] () -- C:\windows\SysNative\PerfStringBackup.INI [2013.05.08 23:14:39 | 000,699,216 | ---- | M] () -- C:\windows\SysNative\perfh007.dat [2013.05.08 23:14:39 | 000,653,158 | ---- | M] () -- C:\windows\SysNative\perfh009.dat [2013.05.08 23:14:39 | 000,148,982 | ---- | M] () -- C:\windows\SysNative\perfc007.dat [2013.05.08 23:14:39 | 000,121,832 | ---- | M] () -- C:\windows\SysNative\perfc009.dat [2013.05.08 17:21:36 | 000,020,720 | -H-- | M] () -- C:\windows\SysNative\7B296FB0-376B-497e-B012-9C450E1B7327-5P-1.C7483456-A289-439d-8115-601632D005A0 [2013.05.08 17:21:36 | 000,020,720 | -H-- | M] () -- C:\windows\SysNative\7B296FB0-376B-497e-B012-9C450E1B7327-5P-0.C7483456-A289-439d-8115-601632D005A0 [2013.05.07 21:48:46 | 000,602,112 | ---- | M] (OldTimer Tools) -- C:\Users\Jörg\Desktop\OTL.exe [2013.05.05 20:14:13 | 004,745,728 | ---- | M] (AVAST Software) -- C:\Users\Jörg\Desktop\aswMBR.exe [2013.05.05 16:12:00 | 000,001,922 | ---- | M] () -- C:\Users\Public\Desktop\avast! Free Antivirus.lnk [2013.05.05 16:11:52 | 000,000,000 | ---- | M] () -- C:\windows\SysWow64\config.nt [2013.05.05 15:51:40 | 000,628,743 | ---- | M] () -- C:\Users\Jörg\Desktop\adwcleaner.exe [2013.05.05 15:28:46 | 000,000,328 | ---- | M] () -- C:\windows\tasks\HPCeeScheduleForJörg.job [2013.05.05 13:23:20 | 000,000,340 | ---- | M] () -- C:\windows\tasks\HPCeeScheduleFor******$.job [2013.05.05 12:25:59 | 000,001,109 | ---- | M] () -- C:\Users\Public\Desktop\ Malwarebytes Anti-Malware .lnk [2013.05.02 17:44:28 | 000,189,936 | ---- | M] () -- C:\windows\SysNative\drivers\aswVmm.sys [2013.05.02 01:34:06 | 001,025,808 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswSnx.sys [2013.05.02 01:34:06 | 000,378,432 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswSP.sys [2013.05.02 01:34:06 | 000,072,016 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswRdr2.sys [2013.05.02 01:34:06 | 000,065,336 | ---- | M] () -- C:\windows\SysNative\drivers\aswRvrt.sys [2013.05.02 01:34:06 | 000,064,288 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswTdi.sys [2013.05.02 01:34:05 | 000,080,816 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswMonFlt.sys [2013.05.02 01:34:05 | 000,033,400 | ---- | M] (AVAST Software) -- C:\windows\SysNative\drivers\aswFsBlk.sys [2013.05.02 01:33:35 | 000,041,664 | ---- | M] (AVAST Software) -- C:\windows\avastSS.scr [2013.05.02 01:33:11 | 000,287,840 | ---- | M] (AVAST Software) -- C:\windows\SysNative\aswBoot.exe [2013.04.20 10:54:00 | 001,344,340 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013203.jpg [2013.04.20 09:24:50 | 001,477,102 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013202.jpg [2013.04.20 09:24:36 | 001,974,692 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013201.jpg [2013.04.20 08:47:34 | 001,398,559 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013200.jpg [2013.04.20 08:43:02 | 001,365,399 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013199.jpg [2013.04.20 08:36:10 | 001,566,010 | ---- | M] () -- C:\Users\Jörg\Desktop\20042013198.jpg [2013.04.14 16:29:55 | 016,638,853 | ---- | M] () -- C:\Users\Jörg\Desktop\sidon.pdf [2013.04.14 05:12:49 | 000,276,904 | ---- | M] () -- C:\windows\SysNative\FNTCACHE.DAT [2013.04.12 20:54:19 | 553,063,060 | ---- | M] () -- C:\windows\MEMORY.DMP ========== Files Created - No Company Name ========== [2013.05.06 19:25:06 | 000,628,743 | ---- | C] () -- C:\Users\Jörg\Desktop\adwcleaner.exe [2013.05.05 16:12:00 | 000,001,922 | ---- | C] () -- C:\Users\Public\Desktop\avast! Free Antivirus.lnk [2013.05.05 16:11:58 | 000,189,936 | ---- | C] () -- C:\windows\SysNative\drivers\aswVmm.sys [2013.05.05 16:11:57 | 000,065,336 | ---- | C] () -- C:\windows\SysNative\drivers\aswRvrt.sys [2013.05.05 16:11:48 | 000,000,000 | ---- | C] () -- C:\windows\SysWow64\config.nt [2013.05.05 12:25:59 | 000,001,109 | ---- | C] () -- C:\Users\Public\Desktop\ Malwarebytes Anti-Malware .lnk [2013.04.20 22:04:51 | 001,477,102 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013202.jpg [2013.04.20 22:04:50 | 001,974,692 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013201.jpg [2013.04.20 22:04:50 | 001,566,010 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013198.jpg [2013.04.20 22:04:50 | 001,398,559 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013200.jpg [2013.04.20 22:04:50 | 001,365,399 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013199.jpg [2013.04.20 22:04:50 | 001,344,340 | ---- | C] () -- C:\Users\Jörg\Desktop\20042013203.jpg [2013.04.20 17:49:21 | 016,638,853 | ---- | C] () -- C:\Users\Jörg\Desktop\sidon.pdf [2013.04.12 20:54:19 | 553,063,060 | ---- | C] () -- C:\windows\MEMORY.DMP [2012.03.24 20:53:59 | 000,008,192 | ---- | C] () -- C:\Users\Jörg\AppData\Local\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini [2011.10.13 11:47:06 | 000,003,120 | ---- | C] () -- C:\windows\SysWow64\drivers\wdfdbga.sys [2011.10.13 11:36:02 | 000,000,000 | ---- | C] () -- C:\windows\ativpsrm.bin [2011.10.13 11:33:16 | 000,003,914 | ---- | C] () -- C:\windows\SysWow64\atipblup.dat [2011.10.13 11:32:09 | 000,025,984 | ---- | C] () -- C:\windows\snuvcdsm.exe [2011.10.13 11:32:08 | 000,015,497 | ---- | C] () -- C:\windows\snp2uvc.ini [2011.08.23 11:10:44 | 000,000,256 | ---- | C] () -- C:\windows\SysWow64\vcsAPIShared.dll.hpsign [2011.05.30 22:58:34 | 000,185,168 | ---- | C] () -- C:\windows\SysWow64\PassThroughOTP.dll [2011.05.30 22:58:34 | 000,000,256 | ---- | C] () -- C:\windows\SysWow64\PassThroughOTP.dll.hpsign ========== ZeroAccess Check ========== [2009.07.14 06:55:00 | 000,000,227 | RHS- | M] () -- C:\windows\assembly\Desktop.ini [HKEY_CURRENT_USER\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] /64 [HKEY_CURRENT_USER\Software\Classes\Wow6432node\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] [HKEY_CURRENT_USER\Software\Classes\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InProcServer32] /64 [HKEY_CURRENT_USER\Software\Classes\Wow6432node\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InProcServer32] [HKEY_LOCAL_MACHINE\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] /64 "" = C:\Windows\SysNative\shell32.dll -- [2012.06.09 07:30:56 | 014,165,504 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Apartment [HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32] "" = %SystemRoot%\system32\shell32.dll -- [2012.06.09 06:46:56 | 012,868,608 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Apartment [HKEY_LOCAL_MACHINE\Software\Classes\clsid\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InProcServer32] /64 "" = C:\Windows\SysNative\wbem\fastprox.dll -- [2009.07.14 03:40:51 | 000,909,312 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Free [HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InProcServer32] "" = %systemroot%\system32\wbem\fastprox.dll -- [2009.07.14 03:15:20 | 000,605,696 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Free [HKEY_LOCAL_MACHINE\Software\Classes\clsid\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InProcServer32] /64 "" = C:\Windows\SysNative\wbem\wbemess.dll -- [2009.07.14 03:41:56 | 000,505,856 | ---- | M] (Microsoft Corporation) "ThreadingModel" = Both [HKEY_LOCAL_MACHINE\Software\Wow6432Node\Classes\clsid\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InProcServer32] ========== LOP Check ========== [2013.02.07 21:41:33 | 000,000,000 | ---D | M] -- C:\Users\Jörg\AppData\Roaming\Audacity [2013.02.07 21:24:28 | 000,000,000 | ---D | M] -- C:\Users\Jörg\AppData\Roaming\Canneverbe Limited [2012.02.18 21:09:37 | 000,000,000 | ---D | M] -- C:\Users\Jörg\AppData\Roaming\DigitalPersona [2013.02.07 21:14:29 | 000,000,000 | ---D | M] -- C:\Users\Jörg\AppData\Roaming\EAC [2013.04.14 12:47:10 | 000,000,000 | ---D | M] -- C:\Users\Jörg\AppData\Roaming\Leadertech [2013.04.25 22:30:07 | 000,000,000 | ---D | M] -- C:\Users\Jörg\AppData\Roaming\SoftGrid Client [2012.02.18 21:33:02 | 000,000,000 | ---D | M] -- C:\Users\Jörg\AppData\Roaming\Synaptics [2012.03.31 22:21:39 | 000,000,000 | ---D | M] -- C:\Users\Jörg\AppData\Roaming\TP ========== Purity Check ========== < End of report > und die Extras: [CODE]fOTL EXTRAS Logfile: Code:
ATTFilter OTL Extras logfile created on: 12.05.2013 13:44:27 - Run 3
OTL by OldTimer - Version 3.2.69.0 Folder = C:\Users\Jörg\Desktop
64bit- Professional (Version = 6.1.7600) - Type = NTWorkstation
Internet Explorer (Version = 9.0.8112.16421)
Locale: 00000407 | Country: Deutschland | Language: DEU | Date Format: dd.MM.yyyy
3,94 Gb Total Physical Memory | 3,34 Gb Available Physical Memory | 84,90% Memory free
7,87 Gb Paging File | 7,32 Gb Available in Paging File | 93,01% Paging File free
Paging file location(s): ?:\pagefile.sys [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\windows | %ProgramFiles% = C:\Program Files (x86)
Drive C: | 275,00 Gb Total Space | 176,46 Gb Free Space | 64,17% Space Free | Partition Type: NTFS
Drive D: | 1,96 Gb Total Space | 0,73 Gb Free Space | 37,18% Space Free | Partition Type: FAT32
Drive E: | 17,80 Gb Total Space | 2,70 Gb Free Space | 15,19% Space Free | Partition Type: NTFS
Drive F: | 4,98 Gb Total Space | 2,13 Gb Free Space | 42,69% Space Free | Partition Type: FAT32
Computer Name: ****** | User Name: Jörg | Logged in as Administrator.
Boot Mode: SafeMode with Networking | Scan Mode: All users | Include 64bit Scans
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days
========== Extra Registry (SafeList) ==========
========== File Associations ==========
64bit: [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\<extension>]
.url[@ = InternetShortcut] -- C:\windows\SysNative\rundll32.exe (Microsoft Corporation)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\<extension>]
.cpl [@ = cplfile] -- C:\windows\SysWow64\control.exe (Microsoft Corporation)
[HKEY_USERS\S-1-5-21-2069978452-285043259-3883334984-1002\SOFTWARE\Classes\<extension>]
.html [@ = FirefoxHTML] -- C:\Program Files (x86)\Mozilla Firefox\firefox.exe (Mozilla Corporation)
========== Shell Spawning ==========
64bit: [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\<key>\shell\[command]\command]
batfile [open] -- "%1" %*
cmdfile [open] -- "%1" %*
comfile [open] -- "%1" %*
exefile [open] -- "%1" %*
helpfile [open] -- Reg Error: Key error.
htmlfile [edit] -- Reg Error: Key error.
htmlfile [print] -- rundll32.exe %windir%\system32\mshtml.dll,PrintHTML "%1"
inffile [install] -- %SystemRoot%\System32\InfDefaultInstall.exe "%1" (Microsoft Corporation)
InternetShortcut [open] -- "C:\Windows\System32\rundll32.exe" "C:\Windows\System32\ieframe.dll",OpenURL %l (Microsoft Corporation)
InternetShortcut [print] -- "C:\Windows\System32\rundll32.exe" "C:\Windows\System32\mshtml.dll",PrintHTML "%1" (Microsoft Corporation)
piffile [open] -- "%1" %*
regfile [merge] -- Reg Error: Key error.
scrfile [config] -- "%1"
scrfile [install] -- rundll32.exe desk.cpl,InstallScreenSaver %l
scrfile [open] -- "%1" /S
txtfile [edit] -- Reg Error: Key error.
Unknown [openas] -- %SystemRoot%\system32\rundll32.exe %SystemRoot%\system32\shell32.dll,OpenAs_RunDLL %1
Directory [cmd] -- cmd.exe /s /k pushd "%V" (Microsoft Corporation)
Directory [find] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
Folder [open] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
Folder [explore] -- Reg Error: Value error.
Drive [find] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\<key>\shell\[command]\command]
batfile [open] -- "%1" %*
cmdfile [open] -- "%1" %*
comfile [open] -- "%1" %*
cplfile [cplopen] -- %SystemRoot%\System32\control.exe "%1",%* (Microsoft Corporation)
exefile [open] -- "%1" %*
helpfile [open] -- Reg Error: Key error.
htmlfile [edit] -- Reg Error: Key error.
htmlfile [print] -- rundll32.exe %windir%\system32\mshtml.dll,PrintHTML "%1"
inffile [install] -- %SystemRoot%\System32\InfDefaultInstall.exe "%1" (Microsoft Corporation)
piffile [open] -- "%1" %*
regfile [merge] -- Reg Error: Key error.
scrfile [config] -- "%1"
scrfile [install] -- rundll32.exe desk.cpl,InstallScreenSaver %l
scrfile [open] -- "%1" /S
txtfile [edit] -- Reg Error: Key error.
Unknown [openas] -- %SystemRoot%\system32\rundll32.exe %SystemRoot%\system32\shell32.dll,OpenAs_RunDLL %1
Directory [cmd] -- cmd.exe /s /k pushd "%V" (Microsoft Corporation)
Directory [find] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
Folder [open] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
Folder [explore] -- Reg Error: Value error.
Drive [find] -- %SystemRoot%\Explorer.exe (Microsoft Corporation)
========== Security Center Settings ==========
64bit: [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center]
"cval" = 1
64bit: [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Monitoring]
64bit: [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Svc]
"VistaSp1" = 28 4D B2 76 41 04 CA 01 [binary data]
"AntiVirusOverride" = 0
"AntiSpywareOverride" = 0
"FirewallOverride" = 0
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Svc]
========== Firewall Settings ==========
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile]
"DisableNotifications" = 0
"EnableFirewall" = 1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile]
"DisableNotifications" = 0
"EnableFirewall" = 1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\PublicProfile]
"DisableNotifications" = 0
"EnableFirewall" = 1
========== Authorized Applications List ==========
========== Vista Active Open Ports Exception List ==========
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\FirewallRules]
"{0192A64B-1AD9-4D5F-B588-6085CE2F4095}" = lport=139 | protocol=6 | dir=in | app=system |
"{16EB882F-3738-45D8-9533-017F782C9C52}" = rport=137 | protocol=17 | dir=out | app=system |
"{19850CB9-D072-468F-9F19-7A51CAC6CA8A}" = lport=808 | protocol=6 | dir=in | svc=nettcpactivator | app=c:\windows\microsoft.net\framework64\v4.0.30319\smsvchost.exe |
"{2160C548-F10C-4AEA-B4F1-3BB78D8ED451}" = rport=138 | protocol=17 | dir=out | app=system |
"{272DF92A-7BF3-4276-A74B-46FD2E1BC61F}" = lport=rpc | protocol=6 | dir=in | svc=spooler | app=%systemroot%\system32\spoolsv.exe |
"{3291524E-91E1-49E9-93B2-A76B3BE1AD59}" = rport=2177 | protocol=6 | dir=out | svc=qwave | app=%systemroot%\system32\svchost.exe |
"{3D1D9211-8C88-4A2C-89FE-391DF1460D01}" = lport=2177 | protocol=6 | dir=in | svc=qwave | app=%systemroot%\system32\svchost.exe |
"{40DDCBA2-0C1D-407D-94A1-9DB119880E37}" = lport=137 | protocol=17 | dir=in | app=system |
"{59C80455-474C-4727-9DDF-B20E12651936}" = lport=rpc-epmap | protocol=6 | dir=in | svc=rpcss | name=@firewallapi.dll,-28539 |
"{5ECEFD36-6258-4B20-B1A7-946D1011A9B6}" = lport=10243 | protocol=6 | dir=in | app=system |
"{6AB479D5-2093-4EAE-9BD2-DCB9660FF587}" = rport=139 | protocol=6 | dir=out | app=system |
"{918AA308-6A5D-4468-99BA-E5B4AF733611}" = lport=138 | protocol=17 | dir=in | app=system |
"{92D21149-C10A-48CF-A1AA-4271503E5AFB}" = lport=2869 | protocol=6 | dir=in | name=windows live communications platform (upnp) |
"{A4522E36-05CF-4099-B431-21A021329DDD}" = lport=1900 | protocol=17 | dir=in | name=windows live communications platform (ssdp) |
"{A49C1B00-62AB-49EF-99FC-E82239B702B6}" = rport=2177 | protocol=17 | dir=out | svc=qwave | app=%systemroot%\system32\svchost.exe |
"{BF5177BB-C28E-4BC3-B90F-238015CA7BBC}" = lport=2869 | protocol=6 | dir=in | app=system |
"{C893528C-303F-49F5-B8FC-89263CB61171}" = rport=445 | protocol=6 | dir=out | app=system |
"{CC813BBB-40C6-4E61-BC16-CED3C6B74759}" = lport=445 | protocol=6 | dir=in | app=system |
"{D07382A9-5088-4D2F-91A0-79580FF3C44E}" = lport=5355 | protocol=17 | dir=in | svc=dnscache | app=%systemroot%\system32\svchost.exe |
"{D7451446-AEC7-47DD-A5AA-381CFDAC123E}" = lport=2177 | protocol=17 | dir=in | svc=qwave | app=%systemroot%\system32\svchost.exe |
"{EA973CE8-75A2-4BEF-92D0-3CA2CD2F2D98}" = rport=1900 | protocol=17 | dir=out | svc=ssdpsrv | app=%systemroot%\system32\svchost.exe |
"{EE576888-5397-4880-B548-BBD6616E5638}" = rport=10243 | protocol=6 | dir=out | app=system |
"{F34618FA-D6D2-445E-B846-F8D18567EAF5}" = rport=5355 | protocol=17 | dir=out | svc=dnscache | app=%systemroot%\system32\svchost.exe |
"{F82863A7-475C-4E71-A54E-6F6B56174AD9}" = lport=1900 | protocol=17 | dir=in | svc=ssdpsrv | app=%systemroot%\system32\svchost.exe |
========== Vista Active Application Exception List ==========
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\FirewallRules]
"{0A364CDC-F028-4DF0-97F0-E7D7F61272C0}" = protocol=17 | dir=in | app=%programfiles%\windows media player\wmplayer.exe |
"{0B3BD192-3BF5-45D4-812B-12A82396898C}" = protocol=58 | dir=in | name=@firewallapi.dll,-28545 |
"{0DD9A12C-AB23-4CE7-86F9-467CA52C66F9}" = protocol=17 | dir=out | app=%programfiles%\windows media player\wmpnetwk.exe |
"{1420040F-05DC-4763-8310-19F5616EE6A1}" = protocol=17 | dir=in | app=%programfiles(x86)%\windows media player\wmplayer.exe |
"{33D12B0C-6806-4FFC-8EF4-9A02701F5D53}" = protocol=6 | dir=out | app=system |
"{350A76D2-FBFD-44DF-AC46-AE4F1453A241}" = protocol=6 | dir=out | app=%programfiles%\windows media player\wmplayer.exe |
"{35724AED-19DC-4BF0-9ABE-88E3C61E89A0}" = protocol=1 | dir=out | name=@firewallapi.dll,-28544 |
"{378F5AE0-29BE-4FB1-A025-622573ED7744}" = dir=in | app=c:\program files (x86)\windows live\contacts\wlcomm.exe |
"{5C803020-5D39-4DEC-AEFD-BFBD93B953AD}" = protocol=17 | dir=in | app=%programfiles%\windows media player\wmpnetwk.exe |
"{6447EFB3-ED85-4D32-B491-D24CB0139E50}" = protocol=17 | dir=out | app=%programfiles(x86)%\windows media player\wmplayer.exe |
"{7DEC5AF2-2377-46B7-B9EE-3A99A8639B32}" = protocol=6 | dir=out | app=%programfiles%\windows media player\wmpnetwk.exe |
"{815DC455-BEEF-4728-9A13-717AF0A39973}" = protocol=58 | dir=out | name=@firewallapi.dll,-28546 |
"{8B24FBF7-7879-4989-B239-B78A3AF339D6}" = protocol=6 | dir=in | app=%programfiles%\windows media player\wmpnetwk.exe |
"{91531839-201A-4481-9626-E0C0B120603C}" = protocol=6 | dir=out | app=%programfiles(x86)%\windows media player\wmplayer.exe |
"{A060D564-D617-44D2-96DC-FBC3B801EFA2}" = protocol=17 | dir=in | app=%programfiles%\windows media player\wmplayer.exe |
"{A4984F99-2126-4AC6-B9FE-E73C7017DBE4}" = protocol=17 | dir=out | app=%programfiles%\windows media player\wmplayer.exe |
"{A86A8C7F-42DF-4068-9A7C-B851D084A889}" = protocol=6 | dir=out | svc=upnphost | app=%systemroot%\system32\svchost.exe |
"{CB16115E-D1F3-4F0C-9491-6F981B9C3FF4}" = protocol=1 | dir=in | name=@firewallapi.dll,-28543 |
"{DDD07C69-AAEE-49F3-B17C-F7308F7E746B}" = protocol=17 | dir=out | app=%programfiles%\windows media player\wmplayer.exe |
"{ECC8B4B6-9056-4536-BEDD-CE3AF381243D}" = protocol=6 | dir=out | app=%programfiles%\windows media player\wmplayer.exe |
"{FF377F92-17AF-4A01-9585-28083EF22F33}" = dir=in | app=c:\program files (x86)\skype\phone\skype.exe |
========== HKEY_LOCAL_MACHINE Uninstall List ==========
64bit: [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall]
"{071c9b48-7c32-4621-a0ac-3f809523288f}" = Microsoft Visual C++ 2005 Redistributable (x64)
"{1B8ABA62-74F0-47ED-B18C-A43128E591B8}" = Windows Live ID Sign-in Assistant
"{230D1595-57DA-4933-8C4E-375797EBB7E1}" = Bluetooth Win7 Suite (64)
"{26A24AE4-039D-4CA4-87B4-2F86417017FF}" = Java 7 Update 17 (64-bit)
"{3D8EDF72-13CC-4E51-AAB6-32A20524D2E0}" = HP Power Assistant
"{422BA615-2133-4DC0-8673-09C8CC7557F2}" = HP ProtectTools Security Manager
"{483D5A49-A26B-4CB8-AA2D-0D1811322061}" = HP DayStarter
"{4B6C7001-C7D6-3710-913E-5BC23FCE91E6}" = Microsoft Visual C++ 2008 Redistributable - x64 9.0.30729.4148
"{503F672D-6C84-448A-8F8F-4BC35AC83441}" = AMD APP SDK Runtime
"{555ECC75-AB3B-6434-8900-2BBA4F91F107}" = ccc-utility64
"{55B52830-024A-443E-AF61-61E1E71AFA1B}" = Device Access Manager for HP ProtectTools
"{5EB6F3CB-46F4-451F-A028-7F6D8D35D7D0}" = Windows Live Language Selector
"{5FCE6D76-F5DC-37AB-B2B8-22AB8CEDB1D4}" = Microsoft Visual C++ 2008 Redistributable - x64 9.0.30729.6161
"{63E42DE7-C468-31B0-E373-173C67C87B88}" = ATI Catalyst Install Manager
"{6ce5bae9-d3ca-4b99-891a-1dc6c118a5fc}" = Microsoft Visual C++ 2005 Redistributable (x64)
"{8220EEFE-38CD-377E-8595-13398D740ACE}" = Microsoft Visual C++ 2008 Redistributable - x64 9.0.30729.17
"{83DA38AB-1014-41C2-A3CD-E2B93832A71A}" = HP 3D DriveGuard
"{89F4137D-6C26-4A84-BDB8-2E5A4BB71E00}" = Microsoft Silverlight
"{8A0041CD-277C-4C1F-BFE4-7AC508B20B4C}" = Drive Encryption For HP ProtectTools
"{8E34682C-8118-31F1-BC4C-98CD9675E1C2}" = Microsoft .NET Framework 4 Extended
"{90140000-006D-0407-1000-0000000FF1CE}" = Microsoft Office Klick-und-Los 2010
"{95120000-00B9-0409-1000-0000000FF1CE}" = Microsoft Application Error Reporting
"{ACA53F68-B003-4D0E-9C3D-0C4EE09D08A8}" = Privacy Manager for HP ProtectTools
"{ad8a2fa1-06e7-4b0d-927d-6e54b3d31028}" = Microsoft Visual C++ 2005 Redistributable (x64)
"{BFA2D2A7-4FAC-4862-B7A3-960B329C2177}" = Validity Fingerprint Sensor Driver
"{CC4D56B7-6F18-470B-8734-ABCD75BCF4F1}" = HP Auto
"{D3A775F2-2674-4452-8D80-1FC1446052EE}" = Face Recognition for HP ProtectTools
"{DA5E371C-6333-3D8A-93A4-6FD5B20BCC6E}" = Microsoft Visual C++ 2010 x64 Redistributable - 10.0.30319
"{F5B09CFD-F0B2-36AF-8DF4-1DF6B63FC7B4}" = Microsoft .NET Framework 4 Client Profile
"{FB06FBC7-3CE3-50D9-1803-CC28E5ADF780}" = WMV9/VC-1 Video Playback
"HPProtectTools" = HP ProtectTools Security Manager
"Microsoft .NET Framework 4 Client Profile" = Microsoft .NET Framework 4 Client Profile
"Microsoft .NET Framework 4 Extended" = Microsoft .NET Framework 4 Extended
"SynTPDeinstKey" = Synaptics Pointing Device Driver
"WinRAR archiver" = WinRAR 4.20 (64-Bit)
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall]
"{03046EBB-CB7C-4B98-BEFB-690EB955DA22}" = HP Setup
"{07FA4960-B038-49EB-891B-9F95930AA544}" = HP Customer Experience Enhancements
"{08F10409-00BB-8843-4813-37FDDD972CB1}" = CCC Help Chinese Standard
"{08FB6F00-7D8D-5474-B70D-607638405BEB}" = CCC Help Korean
"{09F56A49-A7B1-4AAB-95B9-D13094254AD1}" = Windows Live UX Platform Language Pack
"{0B0F231F-CE6A-483D-AA23-77B364F75917}" = Windows Live Installer
"{0BE5C4DB-8EA2-483D-BD71-D7EB09040CDE}" = Windows Live UX Platform Language Pack
"{0DEA342C-15CB-4F52-97B6-06A9C4B9C06F}" = SDK
"{11C9A461-DD9D-4C71-85A4-6DCE7F99CC44}" = HP Wallpaper
"{12379137-5A34-8311-A00C-4571E468F507}" = CCC Help Polish
"{1392513C-F92A-2893-E263-071E943CB4B8}" = Catalyst Control Center InstallProxy
"{1529490E-DC67-A7DA-E7FE-789B929E67F0}" = CCC Help Norwegian
"{18C94B21-9C7B-11D0-933A-00608CEA7318}_is1" = 1.0.2
"{190A7D93-3823-439C-91B9-ADCE3EC2A6A2}" = ArcSoft Webcam Sharing Manager
"{19BA08F7-C728-469C-8A35-BFBD3633BE08}" = Windows Live Movie Maker
"{1F1C2DFC-2D24-3E06-BCB8-725134ADF989}" = Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.4148
"{200FEC62-3C34-4D60-9CE8-EC372E01C08F}" = Windows Live SOXE Definitions
"{20976B1F-E910-404D-9261-C16EE7E12DC8}" = HP QuickWeb
"{26604C7E-A313-4D12-867F-7C6E7820BE4C}" = JMicron Flash Media Controller Driver
"{26A24AE4-039D-4CA4-87B4-2F83217017FF}" = Java 7 Update 17
"{2A07C35B-8384-4DA4-9A95-442B6C89A073}" = Windows Live Essentials
"{2C43790E-8470-1027-82D3-DF319F3C410F}" = Intel(R) Identity Protection Technology 1.0.71.0
"{2E07A6AE-C2EC-05DB-8344-B562E5D9E341}" = CCC Help Swedish
"{3336F667-9049-4D46-98B6-4C743EEBC5B1}" = Windows Live Photo Gallery
"{34319F1F-7CF2-4CC9-B357-1AE7D2FF3AC5}" = Windows Live
"{344A1AA2-AC8E-4741-BDB0-65B68FDA883C}" = HP SoftPaq Download Manager
"{34F4D9A4-42C2-4348-BEF4-E553C84549E7}" = Windows Live Photo Gallery
"{399C37FB-08AF-493B-BFED-20FBD85EDF7F}" = HP Webcam Driver
"{3E29EE6C-963A-4aae-86C1-DC237C4A49FC}" = Intel(R) Rapid Storage Technology
"{3E918CE9-BDA6-282D-0E19-E11DF8004ABE}" = CCC Help Thai
"{4114A073-7385-4742-8A5E-A5788FAC838F}" = ArcSoft TotalMedia
"{4441B01C-0AF2-6EE7-CDB3-AD0DB41E7147}" = CCC Help Hungarian
"{488F0347-C4A7-4374-91A7-30818BEDA710}" = Galerie de photos Windows Live
"{4A03706F-666A-4037-7777-5F2748764D10}" = Java Auto Updater
"{4B21E4B2-89B8-499D-803A-34ABF929401E}" = HP Connection Manager
"{4CBABDFD-49F8-47FD-BE7D-ECDE7270525A}" = Windows Live PIMT Platform
"{51C7AD07-C3F6-4635-8E8A-231306D810FE}" = Cisco LEAP Module
"{531000B3-DBEE-4115-BBF3-DA48B67C053F}" = HP Software Setup
"{5442DAB8-7177-49E1-8B22-09A049EA5996}" = Renesas Electronics USB 3.0 Host Controller Driver
"{54C65FE7-83BD-4A5B-A9B4-41F793C5F241}" = HP System Default Settings
"{61EDBE71-5D3E-4AB7-AD95-E53FEAF68C17}" = Bing Rewards Client Installer
"{64BF0187-F3D2-498B-99EA-163AF9AE6EC9}" = Cisco EAP-FAST Module
"{65153EA5-8B6E-43B6-857B-C6E4FC25798A}" = Intel(R) Management Engine Components
"{668643A5-48DD-B0E9-62E1-1FDA18D54F66}" = CCC Help Finnish
"{682B3E4F-696A-42DE-A41C-4C07EA1678B4}" = Windows Live SOXE
"{69EA3784-E961-76A2-6C11-7B83AA50E56A}" = CCC Help Czech
"{6A05FEDF-662E-46BF-8A25-010E3F1C9C69}" = Windows Live UX Platform Language Pack
"{6A9C9BE1-14A3-42ED-A388-42E30A1412E9}" = HP Documentation
"{6AFCA4E1-9B78-3640-8F72-A7BF33448200}" = Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729
"{6D6ADF03-B257-4EA5-BBC1-1D145AF8D514}" = File Sanitizer For HP ProtectTools
"{6DEC8BD5-7574-47FA-B080-492BBBE2FEA3}" = Windows Live Movie Maker
"{6F340107-F9AA-47C6-B54C-C3A19F11553F}" = Hewlett-Packard ACLM.NET v1.2.1.1
"{710f4c1c-cc18-4c49-8cbf-51240c89a1a2}" = Microsoft Visual C++ 2005 Redistributable
"{71543470-E3F8-6A06-08C8-783CD286D2BA}" = CCC Help German
"{737DCE46-824C-40BA-8776-81D9D1DB04AB}" = Catalyst Control Center - Branding
"{73FC3510-6421-40F7-9503-EDAE4D0CF70D}" = Windows Live Photo Common
"{76BAC71B-00A7-BBFA-5DAE-EEB0DF9F4098}" = CCC Help English
"{7CF1347C-61F6-C495-127C-912FD6CB432D}" = CCC Help Japanese
"{7E265513-8CDA-4631-B696-F40D983F3B07}_is1" = CDBurnerXP
"{80C45B94-2BA0-8E23-95A7-8A9FCD836EFD}" = PX Profile Update
"{85BE1D9F-FC67-E84E-F73A-BC7125E3B717}" = CCC Help Portuguese
"{8DC069E7-893C-41E1-9442-DE89FEC33371}" = Xobni Core
"{8DD46C6A-0056-4FEC-B70A-28BB16A1F11F}" = MSVCRT
"{90140011-0066-0407-0000-0000000FF1CE}" = Microsoft Office Starter 2010 - Deutsch
"{92EA4134-10D1-418A-91E1-5A0453131A38}" = Windows Live Movie Maker
"{95140000-0070-0000-0000-0000000FF1CE}" = Microsoft Office 2010
"{95140000-00AF-0407-0000-0000000FF1CE}" = Microsoft PowerPoint Viewer
"{9A25302D-30C0-39D9-BD6F-21E6EC160475}" = Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.17
"{9BD262D0-B788-4546-A0A5-F4F56EC3834B}" = Windows Live Photo Common
"{9BE518E6-ECC6-35A9-88E4-87755C07200F}" = Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161
"{9E48FF52-082C-4CC2-BB67-6E10D09C0431}" = Windows Live UX Platform Language Pack
"{A1EFCBD2-B171-E24D-FAD2-4E711A312DEF}" = CCC Help Danish
"{A60B3BF0-954B-42AF-B8D8-2C1D34B613AA}" = Windows Live Photo Gallery
"{A6365256-0FBA-4DCD-88CE-D92A4DC9328E}" = HP ESU for Microsoft Windows 7
"{A9BDCA6B-3653-467B-AC83-94367DA3BFE3}" = Windows Live Photo Common
"{AB9F8790-4ECB-1BFA-1B80-21DCD40664C3}" = CCC Help Greek
"{ADC70B7A-530B-46E3-8384-48D22681A41E}" = Theft Recovery for HP ProtectTools
"{AE6BF609-EF6A-8764-85EE-6CC65602D88E}" = CCC Help Chinese Traditional
"{B113D18C-67B0-4FB7-B329-E89B66194AE6}" = Windows Live Fotogalerie
"{B26B64E8-DB83-7904-2DF9-F92A7ABC14D9}" = Catalyst Control Center Localization All
"{B3E31950-C92F-BCD9-963D-A520887A262A}" = CCC Help Turkish
"{B7F60A16-7A7B-41FB-9AE3-DE9E324FBA06}" = HP Software Framework
"{BD1A34C9-4764-4F79-AE1F-112F8C89D3D4}" = Energy Star Digital Logo
"{BE211EBE-AC92-515C-D122-A9DD0BC9FFA9}" = Catalyst Control Center
"{C2AB7DC4-489E-4BE9-887A-52262FBADBE0}" = Windows Live Photo Common
"{C3A32068-8AB1-4327-BB16-BED9C6219DC7}" = Atheros Driver Installation Program
"{C6CD49BC-E6A5-F247-0489-F3188F300A8E}" = Catalyst Control Center Profiles Mobile
"{C7C60D93-E5B7-82D7-44A4-E3EE404B56A3}" = CCC Help Dutch
"{C893D8C0-1BA0-4517-B11C-E89B65E72F70}" = Windows Live Photo Common
"{CB7224D9-6DCA-43F1-8F83-6B1E39A00F92}" = Windows Live Movie Maker
"{CBD548E9-E421-7B51-5732-2F63B37589E2}" = CCC Help French
"{CE95A79E-E4FC-4FFF-8A75-29F04B942FF2}" = Windows Live UX Platform
"{D2131BFA-A0D6-4FDE-8614-75B07A9B15EE}" = Windows Live UX Platform Language Pack
"{D436F577-1695-4D2F-8B44-AC76C99E0002}" = Windows Live Photo Common
"{D45240D3-B6B3-4FF9-B243-54ECE3E10066}" = Windows Live Communications Platform
"{D6C3C9E7-D334-4918-BD57-5B1EF14C207D}" = Bing Bar
"{D7922D23-642E-0649-A3C9-38F9E0FA263E}" = CCC Help Russian
"{DEF91E0F-D266-453D-B6F2-1BA002B40CB6}" = Windows Live Essentials
"{DF2035BE-5820-4965-BD97-7FAF8D4A7879}" = Microsoft_VC90_CRT_x86
"{DF63FA79-75AE-45D6-715E-81E92F134702}" = CCC Help Italian
"{E09C4DB7-630C-4F06-A631-8EA7239923AF}" = D3DX10
"{E2531547-0789-690E-9F12-3EDBDBC64DA8}" = CCC Help Spanish
"{E3A5A8AB-58F6-45FF-AFCB-C9AE18C05001}" = IDT Audio
"{E4E88B54-4777-4659-967A-2EED1E6AFD83}" = Windows Live Movie Maker
"{ED16B700-D91F-44B0-867C-7EB5253CA38D}" = Raccolta foto di Windows Live
"{ED5776D5-59B4-46B7-AF81-5F2D94D7C640}" = Cisco PEAP Module
"{EE202411-2C26-49E8-9784-1BC1DBF7DE96}" = HP Support Assistant
"{EE7257A2-39A2-4D2F-9DAC-F9F25B8AE1D8}" = Skype 5.10
"{F07E6C5F-6AE1-72B3-8659-08E2ABB86DF8}" = Catalyst Control Center Graphics Previews Common
"{F0B430D1-B6AA-473D-9B06-AA3DD01FD0B8}" = Microsoft SQL Server 2005 Compact Edition [ENU]
"{F0C3E5D1-1ADE-321E-8167-68EF0DE699A5}" = Microsoft Visual C++ 2010 x86 Redistributable - 10.0.40219
"{F0E3AD40-2BBD-4360-9C76-B9AC9A5886EA}" = Intel(R) Display Audio Driver
"{F761359C-9CED-45AE-9A51-9D6605CD55C4}" = Evernote v. 4.2.2
"{F7E7F0CB-AA41-4D5A-B6F2-8E6738EB063F}" = Realtek Ethernet Controller All-In-One Windows Driver
"{F95E4EE0-0C6E-4273-B6B9-91FD6F071D76}" = Windows Live Essentials
"{FE044230-9CA5-43F7-9B58-5AC5A28A1F33}" = Windows Live Essentials
"{FF3DFA01-1E98-46B4-A065-DA8AD47C9598}" = Windows Live Movie Maker
"Adobe Flash Player ActiveX" = Adobe Flash Player 11 ActiveX
"Adobe Flash Player Plugin" = Adobe Flash Player 11 Plugin
"ArcSoft TotalMedia" = ArcSoft TotalMedia
"Audacity_is1" = Audacity 2.0.3
"avast" = avast! Free Antivirus
"ESET Online Scanner" = ESET Online Scanner v3
"Exact Audio Copy" = Exact Audio Copy 1.0beta3
"InstallShield_{5442DAB8-7177-49E1-8B22-09A049EA5996}" = Renesas Electronics USB 3.0 Host Controller Driver
"InstallShield_{ADC70B7A-530B-46E3-8384-48D22681A41E}" = Theft Recovery for HP ProtectTools
"Malwarebytes' Anti-Malware_is1" = Malwarebytes Anti-Malware Version 1.75.0.1300
"Mozilla Firefox 20.0.1 (x86 de)" = Mozilla Firefox 20.0.1 (x86 de)
"MozillaMaintenanceService" = Mozilla Maintenance Service
"My HP Game Console" = HP Game Console
"Office14.Click2Run" = Microsoft Office Klick-und-Los 2010
"PDF Complete" = PDF Complete Special Edition
"VIP Access SDK" = VIP Access SDK x64(1.0.0.50)
"VLC media player" = VLC media player 2.0.0
"WildTangent hp Master Uninstall" = HP Games
"WinLiveSuite" = Windows Live Essentials
"WT087330" = Bounce Symphony
"WT087361" = FATE
"WT087380" = John Deere Drive Green
"WT087394" = Penguins!
"WT087396" = Polar Bowler
"WT087428" = Bejeweled 2 Deluxe
"WT087453" = Chuzzle Deluxe
"WT087480" = Insaniquarium Deluxe
"WT087485" = Jewel Quest II
"WT087490" = Jewel Quest Solitaire
"WT087501" = Plants vs. Zombies
"WT087510" = Slingo Deluxe
"WT087513" = Virtual Villagers - The Secret City
"WT087519" = Wedding Dash
"WT087533" = Zuma Deluxe
"WT087536" = Diner Dash 2 Restaurant Rescue
"WT089303" = Build-a-Lot - The Elizabethan Era
"WT089308" = Blasterball 3
"WT089328" = Farm Frenzy
"WT089359" = Cake Mania
"WT089362" = Agatha Christie - Peril at End House
"XobniMain" = Xobni
========== Last 20 Event Log Errors ==========
[ Application Events ]
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
Error - 15.04.2013 02:15:57 | Computer Name = ****** | Source = ATIeRecord | ID = 16398
Description = ATI EEU failed to post message to CCC
[ Hewlett-Packard Events ]
Error - 02.05.2012 02:03:33 | Computer Name = ****** | Source = HPSF.exe | ID = 4000
Description =
Error - 25.02.2013 16:26:59 | Computer Name = ****** | Source = hpsa_service.exe | ID = 2000
Description =
[ HP Connection Manager Events ]
Error - 10.04.2013 15:47:52 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/10 21:47:52.771|00001B88|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 10.04.2013 16:30:56 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/10 22:30:56.118|00000340|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 11.04.2013 02:35:06 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/11 08:35:06.187|0000112C|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 11.04.2013 02:35:09 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/11 08:35:09.307|0000112C|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 11.04.2013 15:40:58 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/11 21:40:58.368|00001658|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 12.04.2013 01:38:17 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/12 07:38:17.308|00001B04|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 13.04.2013 16:17:46 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/13 22:17:46.744|0000195C|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 13.04.2013 16:17:49 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/13 22:17:49.458|0000195C|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 13.04.2013 23:11:25 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/14 05:11:25.387|00000DFC|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
Error - 13.04.2013 23:11:33 | Computer Name = ****** | Source = hpCMSrv | ID = 5
Description = 2013/04/14 05:11:33.639|00000DFC|Error |CWLAN::SignalStrengthChanged|Fire_SignalStrengthChanged
failed [hr:0x800706BA]
[ HP Power Assistant Events ]
Error - 07.04.2013 00:22:28 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Wireless.GlobalChanged returned e_INVALID_PARAMETER
Error - 08.04.2013 02:05:36 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Debug.PowerSource failed : e_INVALID_PARAMETER
Error - 08.04.2013 02:05:36 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Debug.PowerSource failed : e_INVALID_PARAMETER
Error - 08.04.2013 13:18:02 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Wireless.GlobalChanged returned e_INVALID_PARAMETER
Error - 09.04.2013 02:29:37 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Debug.PowerSource failed : e_INVALID_PARAMETER
Error - 09.04.2013 02:29:37 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Debug.PowerSource failed : e_INVALID_PARAMETER
Error - 09.04.2013 12:51:14 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Wireless.GlobalChanged returned e_INVALID_PARAMETER
Error - 09.04.2013 14:29:39 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Debug.PowerSource failed : e_INVALID_PARAMETER
Error - 09.04.2013 14:29:39 | Computer Name = ****** | Source = HP PA Service | ID = 1002
Description = An error occurred while using HP CASL. Please restart HP Power Assistant
application. Additional details may be available in the Details section. DETAILS
CASL Error! Get Debug.PowerSource failed : e_INVALID_PARAMETER
Error - 05.05.2013 13:13:42 | Computer Name = ****** | Source = HP PA Application | ID = 1001
Description = An error occurred in HP Power Assistant application. Please restart
HP Power Assistant application. Additional details may be available in the Details
section. DETAILS Das Handle ist ungültig.
[ HP Software Framework Events ]
Error - 11.04.2013 02:35:18 | Computer Name = ******* | Source = CaslSmBios | ID = 5
Description = 2013.04.11 08:35:18.495|00001B58|Error |[CaslWmi]A::Unregister{hpCasl.enReturnCode(string)}|Error
unregistering the PMC.Data event. Exception: Der Objektverweis wurde nicht auf
eine Objektinstanz festgelegt.
Error - 11.04.2013 02:35:18 | Computer Name = ****** | Source = CaslSmBios | ID = 5
Description = 2013.04.11 08:35:18.838|00001B58|Error |[CaslWmi]A::Unregister{hpCasl.enReturnCode(string)}|Error
unregistering the Wireless.GlobalChanged event. Exception: Der Objektverweis wurde
nicht auf eine Objektinstanz festgelegt.
Error - 05.05.2013 13:13:45 | Computer Name = ****** | Source = CaslSmBios | ID = 5
Description = 2013.05.05 19:13:45.826|000016B8|Error |[CaslSmBios]hpSMBIOS::D{bool(byte[]&)}|Der
Typeninitialisierer für "System.Management.ManagementPath" hat eine Ausnahme verursacht.
[ System Events ]
Error - 12.05.2013 07:26:54 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:26:58 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:26:58 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:26:58 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:27:08 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:27:08 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:27:08 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:27:30 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:27:30 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
Error - 12.05.2013 07:27:30 | Computer Name = ****** | Source = Service Control Manager | ID = 7001
Description = Der Dienst "Computerbrowser" ist vom Dienst "Server" abhängig, der
aufgrund folgenden Fehlers nicht gestartet wurde: %%1068
< End of report >
|
| | #7 |
| /// Helfer-Team        | GVU Trojaner 2.12, Siredef, etc. eingefangen sieht alles gut aus... bitte abarbeiten: http://www.trojaner-board.de/126216-...epair-aio.html dann: Downloade Dir bitte
|
| | #8 |
| | GVU Trojaner 2.12, Siredef, etc. eingefangen Ok, hier die beiden Logs. Anmerkung: Ich bin weiterhin im abgesicherten Modus unterwegs. Windows-Repair: Code:
ATTFilter Running Repair Under Current User Account
Starting Repairs...
Start (12.05.2013 17:00:51)
Reset Registry Permissions 01/03
HKEY_CURRENT_USER & Sub Keys
Start (12.05.2013 17:00:51)
Running Repair Under Current User Account
Done (12.05.2013 17:00:53)
Reset Registry Permissions 02/03
HKEY_LOCAL_MACHINE & Sub Keys
Start (12.05.2013 17:00:53)
Running Repair Under Current User Account
Done (12.05.2013 17:00:56)
Reset Registry Permissions 03/03
HKEY_CLASSES_ROOT & Sub Keys
Start (12.05.2013 17:00:56)
Running Repair Under Current User Account
Done (12.05.2013 17:00:58)
Reset File Permissions 01/14
C:\boot & Sub Folders
Start (12.05.2013 17:00:58)
Running Repair Under Current User Account
Done (12.05.2013 17:01:01)
Reset File Permissions 02/14
C:\EFI & Sub Folders
Start (12.05.2013 17:01:01)
Running Repair Under Current User Account
Done (12.05.2013 17:01:03)
Reset File Permissions 03/14
C:\found.000 & Sub Folders
Start (12.05.2013 17:01:03)
Running Repair Under Current User Account
Done (12.05.2013 17:01:05)
Reset File Permissions 04/14
C:\hp & Sub Folders
Start (12.05.2013 17:01:05)
Running Repair Under Current User Account
Done (12.05.2013 17:01:08)
Reset File Permissions 05/14
C:\Kaspersky Rescue Disk 10.0 & Sub Folders
Start (12.05.2013 17:01:08)
Running Repair Under Current User Account
Done (12.05.2013 17:01:10)
Reset File Permissions 06/14
C:\PerfLogs & Sub Folders
Start (12.05.2013 17:01:10)
Running Repair Under Current User Account
Done (12.05.2013 17:01:13)
Reset File Permissions 07/14
C:\Program Files & Sub Folders
Start (12.05.2013 17:01:13)
Running Repair Under Current User Account
Done (12.05.2013 17:01:15)
Reset File Permissions 08/14
C:\Program Files (x86) & Sub Folders
Start (12.05.2013 17:01:15)
Running Repair Under Current User Account
Done (12.05.2013 17:01:17)
Reset File Permissions 09/14
C:\ProgramData & Sub Folders
Start (12.05.2013 17:01:17)
Running Repair Under Current User Account
Done (12.05.2013 17:01:20)
Reset File Permissions 10/14
C:\RegBackup & Sub Folders
Start (12.05.2013 17:01:20)
Running Repair Under Current User Account
Done (12.05.2013 17:01:22)
Reset File Permissions 11/14
C:\Spiele & Sub Folders
Start (12.05.2013 17:01:22)
Running Repair Under Current User Account
Done (12.05.2013 17:01:25)
Reset File Permissions 12/14
C:\swsetup & Sub Folders
Start (12.05.2013 17:01:25)
Running Repair Under Current User Account
Done (12.05.2013 17:01:27)
Reset File Permissions 13/14
C:\SYSTEM.SAV & Sub Folders
Start (12.05.2013 17:01:27)
Running Repair Under Current User Account
Done (12.05.2013 17:01:29)
Reset File Permissions 14/14
C:\Windows & Sub Folders
Start (12.05.2013 17:01:30)
Running Repair Under Current User Account
Done (12.05.2013 17:01:32)
Reset File Permissions 01/03
E:\boot & Sub Folders
Start (12.05.2013 17:01:32)
Running Repair Under Current User Account
Done (12.05.2013 17:01:34)
Reset File Permissions 02/03
E:\Recovery & Sub Folders
Start (12.05.2013 17:01:34)
Running Repair Under Current User Account
Done (12.05.2013 17:01:37)
Reset File Permissions 03/03
E:\system.sav & Sub Folders
Start (12.05.2013 17:01:37)
Running Repair Under Current User Account
Done (12.05.2013 17:01:39)
Reset File Permissions 01/01
F:\Hewlett-Packard & Sub Folders
Start (12.05.2013 17:01:39)
Running Repair Under Current User Account
Done (12.05.2013 17:01:42)
Reset File Permissions: Cleanup
& Sub Folders
Start (12.05.2013 17:01:42)
Running Repair Under Current User Account
Done (12.05.2013 17:01:44)
Register System Files
Start (12.05.2013 17:01:44)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:02:01)
Repair WMI
Start (12.05.2013 17:02:01)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:02:10)
Repair Windows Firewall
Start (12.05.2013 17:02:10)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:02:14)
Repair Internet Explorer
Start (12.05.2013 17:02:14)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:02:36)
Repair MDAC/MS Jet
Start (12.05.2013 17:02:36)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:02:48)
Repair Hosts File
Start (12.05.2013 17:02:48)
Running Repair Under Current User Account
Done (12.05.2013 17:02:51)
Remove Policies Set By Infections
Start (12.05.2013 17:02:51)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:02:55)
Repair Missing Start Menu Icons Removed By Infections
Start (12.05.2013 17:02:55)
Running Repair Under Current User Account
Done (12.05.2013 17:02:58)
Repair Icons
Start (12.05.2013 17:02:58)
Running Repair Under Current User Account
Done (12.05.2013 17:03:00)
Repair Winsock & DNS Cache
Start (12.05.2013 17:03:00)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:03:05)
Remove Temp Files
Start (12.05.2013 17:03:05)
Running Repair Under Current User Account
Done (12.05.2013 17:03:07)
Repair Proxy Settings
Start (12.05.2013 17:03:07)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:03:12)
Unhide Non System Files
Start (12.05.2013 17:03:12)
C:\ - Total Files Unhidden: 556
E:\ - Total Files Unhidden: 0
F:\ - Total Files Unhidden: 0
Done (12.05.2013 17:09:13)
Repair Windows Updates
Start (12.05.2013 17:09:13)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:10:59)
Repair CD/DVD Missing/Not Working
Start (12.05.2013 17:10:59)
Done (12.05.2013 17:10:59)
Repair Volume Shadow Copy Service
Start (12.05.2013 17:10:59)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:04)
Repair Windows Sidebar/Gadgets
Start (12.05.2013 17:11:04)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:08)
Repair MSI (Windows Installer)
Start (12.05.2013 17:11:09)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:13)
Repair Windows Snipping Tool
Start (12.05.2013 17:11:13)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:18)
Repair bat Association
Start (12.05.2013 17:11:18)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:22)
Repair cmd Association
Start (12.05.2013 17:11:22)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:27)
Repair com Association
Start (12.05.2013 17:11:27)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:32)
Repair Directory Association
Start (12.05.2013 17:11:32)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:36)
Repair Drive Association
Start (12.05.2013 17:11:36)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:41)
Repair exe Association
Start (12.05.2013 17:11:41)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:45)
Repair Folder Association
Start (12.05.2013 17:11:45)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:50)
Repair inf Association
Start (12.05.2013 17:11:50)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:55)
Repair lnk (Shortcuts) Association
Start (12.05.2013 17:11:55)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:11:59)
Repair msc Association
Start (12.05.2013 17:11:59)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:12:04)
Repair reg Association
Start (12.05.2013 17:12:04)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:12:08)
Repair scr Association
Start (12.05.2013 17:12:08)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:12:13)
Repair Windows Safe Mode
Start (12.05.2013 17:12:13)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:12:18)
Repair Print Spooler
Start (12.05.2013 17:12:18)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:12:22)
Restore Important Windows Services
Start (12.05.2013 17:12:22)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:12:27)
Set Windows Services To Default Startup
Start (12.05.2013 17:12:27)
Running Repair Under Current User Account
Running Repair Under Current User Account
Done (12.05.2013 17:12:44)
Cleaning up empty logs...
All Selected Repairs Done.
Done (12.05.2013 17:12:44)
Total Repair Time: 00:11:53
...YOU MUST RESTART YOUR SYSTEM...
Running Repair Under Current User Account
Code:
ATTFilter Results of screen317's Security Check version 0.99.63 Windows 7 x64 (UAC is enabled) Out of date service pack!! Internet Explorer 9 ``````````````Antivirus/Firewall Check:`````````````` Windows Security Center service is not running! This report may not be accurate! avast! Antivirus Antivirus up to date! (On Access scanning disabled!) `````````Anti-malware/Other Utilities Check:````````` Malwarebytes Anti-Malware Version 1.75.0.1300 Java 7 Update 17 Java version out of Date! Adobe Flash Player 11.6.602.180 Mozilla Firefox (20.0.1) ````````Process Check: objlist.exe by Laurent```````` `````````````````System Health check````````````````` Total Fragmentation on Drive C: ````````````````````End of Log`````````````````````` |
| | #9 | |
| /// Helfer-Team        | GVU Trojaner 2.12, Siredef, etc. eingefangenZitat:
Normal booten! Alles Windows Updates einspielen, inkl. Service Pack! http://windowsupdate.microsoft.com Java aktualisieren Dein Java ist nicht mehr aktuell. Älter Versionen enthalten Sicherheitslücken, die von Malware missbraucht werden können.
Dann so einstellen: http://www.trojaner-board.de/105213-...tellungen.html Danach poste (kopieren und einfuegen) mir, was du hier angezeigt bekommst: PluginCheck Java deaktivieren Aufgrund derezeitigen Sicherheitsluecke: http://www.trojaner-board.de/122961-...ktivieren.html Danach poste mir (kopieren und einfuegen), was du hier angezeigt bekommst: PluginCheck Downloade Dir bitte
|
| | #10 |
| | GVU Trojaner 2.12, Siredef, etc. eingefangen Aus dem Grund, dass wenn ich "normal" boote, der Rechner nach einer Minute neu startet mit der Meldung "Ein kritischer Fehler ist aufgetreten. Windows wird in einer Minute neu gestartet. Speichern Sie jetzt Ihre Daten." Dies ist seit dem ersten Neustart nach der Installation von Avast der Fall (siehe Posting vom 8.5. um 7:49) Das einzige Mal, dass der Laptop nachher nochmal "normal" bootete, ohne eine Minute später wieder einen Neustart hinzulegen war direkt nach dem Gebrauch des OTL-Fix' Der Rechner war anschließend eine Weile an (ich saß zu dem Zeitpunkt nicht dran) und hat wohl Updates gezogen und dann selbstständig einen Neustart hingelegt (siehe Posting vom 08.05.2013, 10:39 unten ... mein neuer Beitrag vom 9.5. wurde an den bestehenden Beitrag vom 8.5. angehängt). Wie auch bei meinem Posting vom 11.5. beschrieben, war das Problem auch bei späteren Boot-Versuchen noch vorhanden. Die späteren Logs von MBAR, OTL-Scan, Windows-Repair und SecurityCheck (also MBAR-Log vom 05.05.2013 19:52:11 und später) sind also im abgesicherten Modus entstanden. Als ich versucht hatte den Rechner nach dem Ausführen von "Windows-Repair" normal zu booten, blieb der Bildschirm (abgesehen vom Mauszeiger) nach dem Login und einer langen Anzeige des "Willkommen"-Bildschirms fast eine Minute lang schwarz, bis dann das Fenster mit der beschriebenen Meldung auftauchte. Kurze Zeit später sah ich dann noch den Desktop, aber es dauerte erwartungsgemäß nicht lange, bis der Rechner den nächsten Neustart hinlegte. Ich kann nochmal versuchen die Windows Updates im abgesicherten Modus zu laden, aber als ich dies das letzte Mal probierte (das war nach der Avast-Installation und vor dem Ausführen von aswMBR.exe) gelang mir dies nicht. Allerdings klappte damals auch nur ein Start im abgesicherter Modus ohne Netzwerktreiber. Ebenso könnte ich nachschauen, ob ein Systemwiderherstellungspunkt vom Nachmittag des 8.5. besteht. Also für den Zeitpunk nachdem der OTL-Fix gelaufen war und bevor der Laptop eine Weile lief, Updates zog, neustartete (mit Bildschirm "Windows wird konfiguriert. Schalten sie ihren Computer nicht aus.") und dann wieder die Meldung "Ein kritischer Fehler ist aufgetreten. Windows wird in einer Minute neu gestartet. Speichern Sie jetzt Ihre Daten." Allerdings will ich nun auch nicht einfach ohne deine Anweisung einen Widerherstellungspunkt suchen und nutzen, weil ich mir sonst womöglich bereits behobene Probleme wieder einhandele. -------------------- Nachtrag: Ich hab's nun probiert Windows Update im abgesicherten Modus zu starten. Bei Aufruf der Microsoft-Homepage werde ich auf die Verknüpfung im Startmenü verwiesen. Bei Anklicken der Verknüpfung geschieht jedoch ... nichts. Auch über die Systemsteuerung lässt sich kein Windows Update durchführen. Das Deinstallieren des Java-Updates 17 gelingt ebensowenig, da auf den "Windows Installer-Dienst" nicht zugegriffen werden konnte. |
| | #11 |
| | GVU Trojaner 2.12, Siredef, etc. eingefangen Hallo, da ich nichts weiter von dir gehört hatte, habe ich es mal mit der Windows-Systemwiederherstellung probiert und den Rechner auf den Stand vom 8.5. um 17:30Uhr gebracht ... also nach dem OTL-Fix und vor dem automatischen Installieren von Windows-Updates. Danach konnte ich den Rechner auch wieder normal booten, ohne dass eine Minute später ein "Zwangs-Neustart" hingelegt wird. Ich habe dann eine neue Java-Version installiert und die Windows-Updates geladen ... inklusive dem Service Pack 1. Nach dem nächsten Neustart kam aber wieder die altbekannte Meldung, identisch mit dem Screenshot den "Kansas" gepostet hatte: 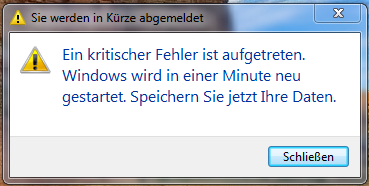 Übrigens, selbst wenn ich mich nicht einlogge, startet der PC neu ... also ich kann den Rechner einschalten und ihm zusehen, wie er alle paar Minuten neu startet ... wenn ich möchte. Ich brauche dafür nichtmal mein Passwort eingeben, tolle Show. Nunja, mit der Installation des Service Pack 1 sind die älteren Wiederherstellungspunkte von Windows gelöscht worden. Ich kann also keinen "funktionieren Zustand" über diese Variante wiederherstellen. Damit bin ich also erstmal ratlos ... sowohl was die Ursache für diese Fehler betrifft, als auch wie man sie bekämpfen könnte. Wenn du keinen weiteren Vorschlag hast, was man machen könnte, so würde ich versuchen über Pfingsten meine Dateien zu sichern und dann das System neu aufsetzen. |
| | #12 |
| /// Helfer-Team        | GVU Trojaner 2.12, Siredef, etc. eingefangen Warum schickst du mir nicht einfac eine PM? Dein Thread ist einfach untergegangen. Da du jetzt alles rueckgaengig gemacht hast: Du hast mehr als eine schwere Infektion auf Deinem Rechner. http://www.trojaner-board.de/56634-rootkits.html Er ist kompromittiert und ist nicht mehr vertrauenswuerdig. Du solletest von einem sauberen System aus alle deine Passwoerter aendern. Ich empfehle dir dringendst den PC vom Netz zu trennen und neu aufzusetzen. Anleitungen zum Neuaufsetzen (bebildert) > Windows 7 neu aufsetzen > Vista > XP 1. Datenrettung:
2. Formatieren, Windows neu instalieren:
3. PC absichern: http://www.trojaner-board.de/96344-a...-rechners.html ich werde außerdem noch weitere punkte dazu posten. 4. alle Passwörter ändern! 5. nach PC Absicherung, die gesicherten Daten prüfen und falls sauber: zurückspielen. |
| | #13 |
| /// Helfer-Team        | GVU Trojaner 2.12, Siredef, etc. eingefangen Fehlende Rückmeldung Gibt es Probleme beim Abarbeiten obiger Anleitung? Um Kapazitäten für andere Hilfesuchende freizumachen, lösche ich dieses Thema aus meinen Benachrichtigungen. Solltest Du weitermachen wollen, schreibe mir eine PN oder eröffne ein neues Thema. http://www.trojaner-board.de/69886-a...-beachten.html Hinweis: Das Verschwinden der Symptome bedeutet nicht, dass Dein Rechner sauber ist. |
 |
| Themen zu GVU Trojaner 2.12, Siredef, etc. eingefangen |
| .dll, administrator, antivir, antivirus, avast, classpnp.sys, computer, desktop, explorer, fehler, firefox, hal.dll, hijack.trojan.siredef.c, internet browser, kaspersky, log file, log-file, neustart, problem, recycle.bin, registrierungsdatenbank, registry, schutz, security, starten, svchost.exe, trojan-ransom.win32.foreign.bxjj, trojan.0access, trojan.siredef.c, trojaner |